Attach IAM Role to an AWS Elastic Container Service Task
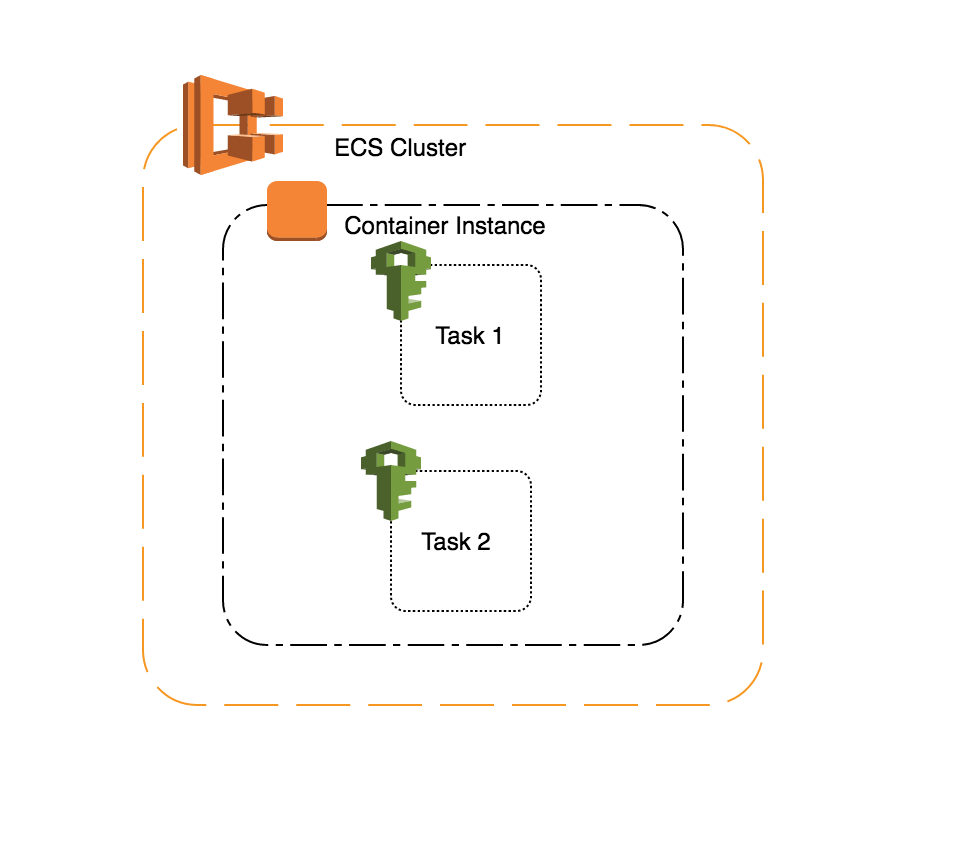
If you are hosting some micro websites on the AWS ECS, where every task is a separate application, and each task has running multiple containers on a Cluster. If we have a scenario where we want each of our application should upload its data to a separate AWS S3 bucket, we create a single role giving access to all S3 buckets and attach it to the cluster instance. This would give access to every application to access every S3 bucket.
To control the application access to S3 buckets, we have to assign IAM role at the task level, so that each application has access only to its own bucket.
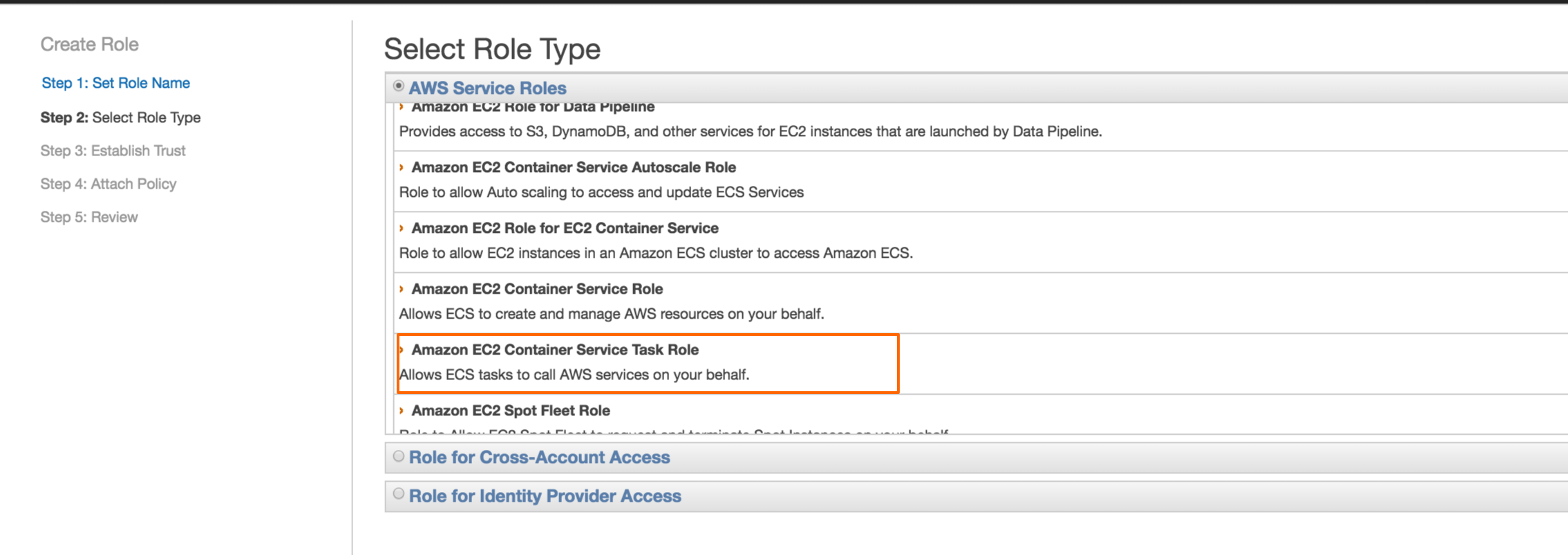
Create IAM Role:
First, you need to create a new Role, select Amazon EC2 Container Service Task Role type in the Select Role type option while creating the IAM role.
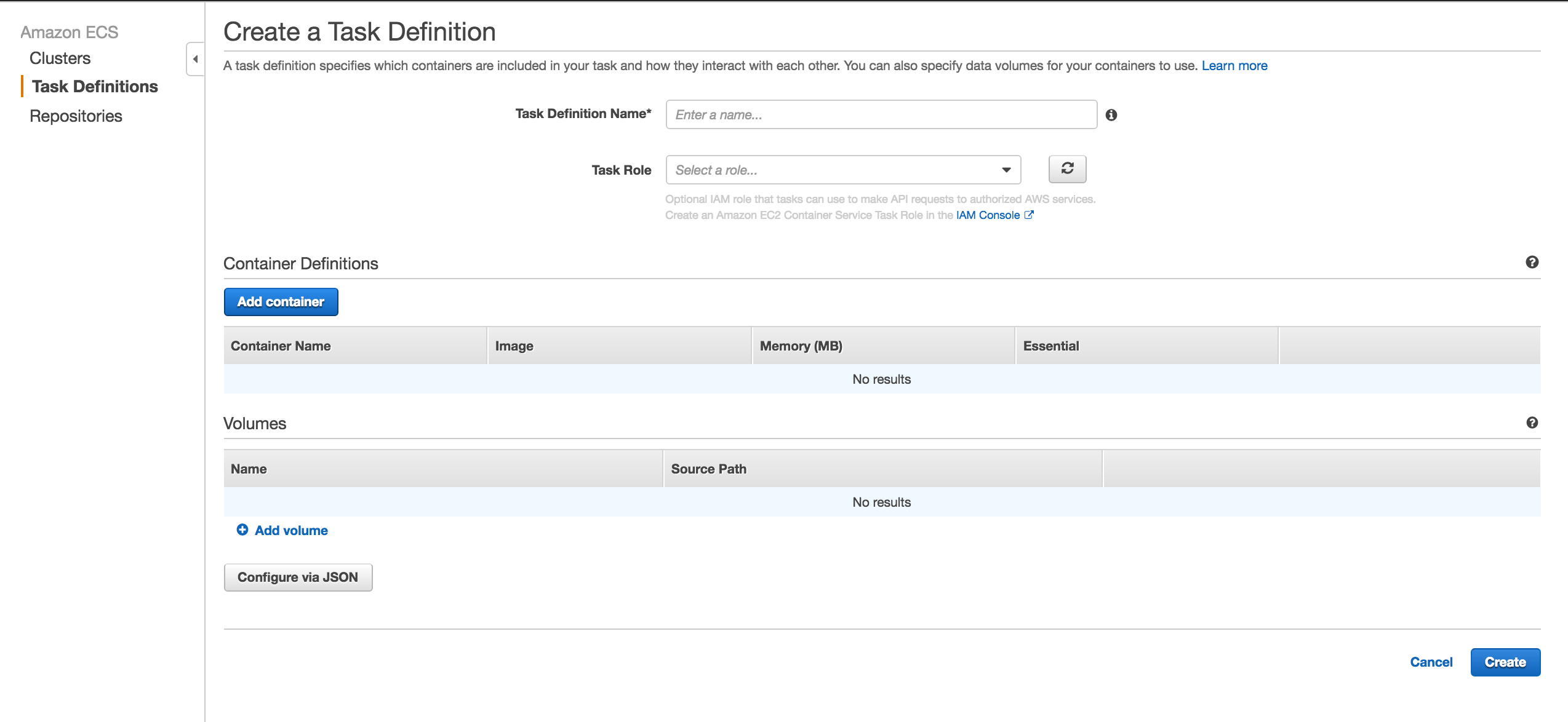
Create Task:
Select IAM role from the Task Role drop-down list, add container definition and save the task. Now, if you run that task manually or create any service from that task, it will have the selected IAM role with it:
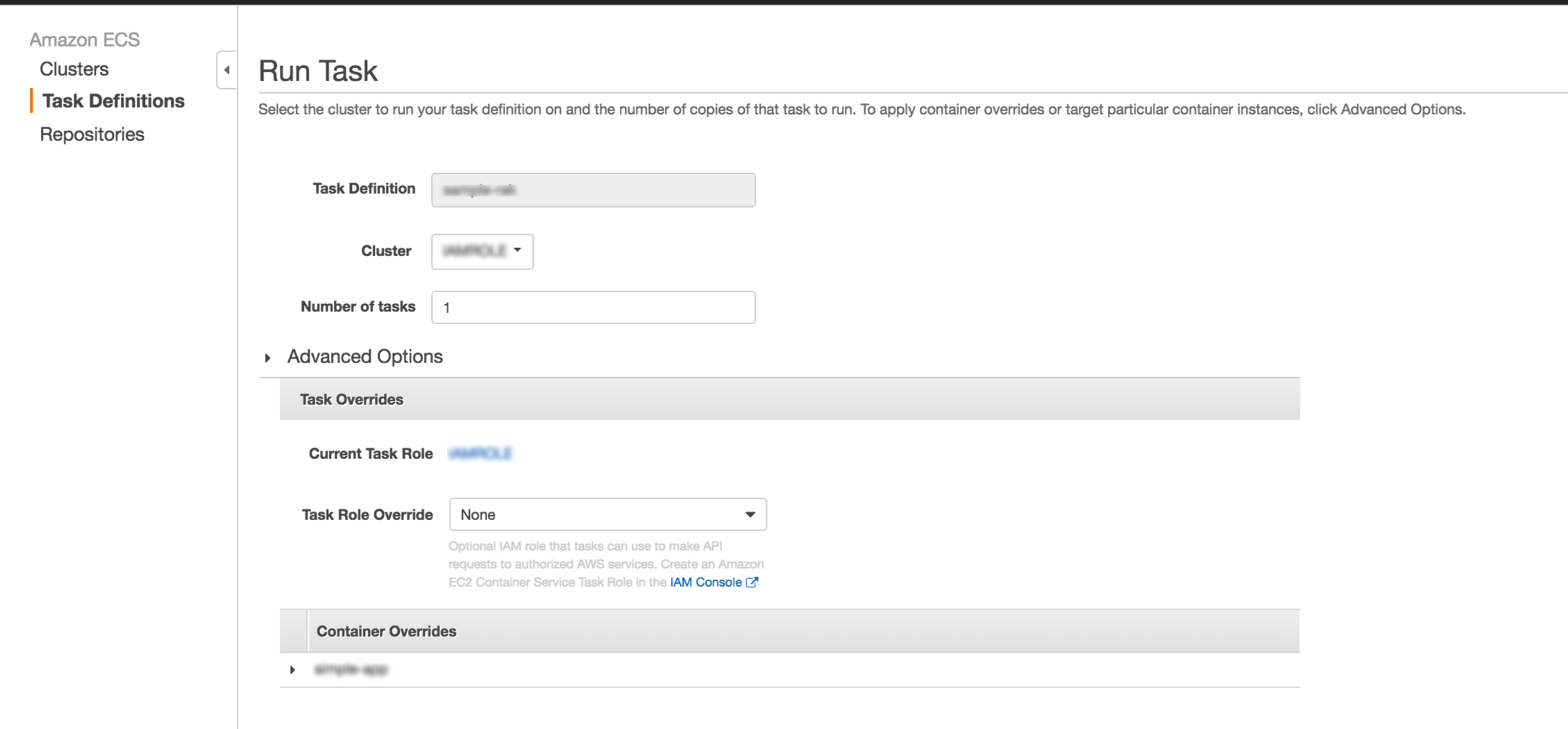
Run Task:
You can also override IAM role while running any task manually. You need to select the new IAM role that you want to attach to that task:
Query Credentials:
From the container you can also query the credentials from the following CURL request:
$ curl 169.254.170.2$AWS_CONTAINER_CREDENTIALS_RELATIVE_URI -ss | python -mjson.tool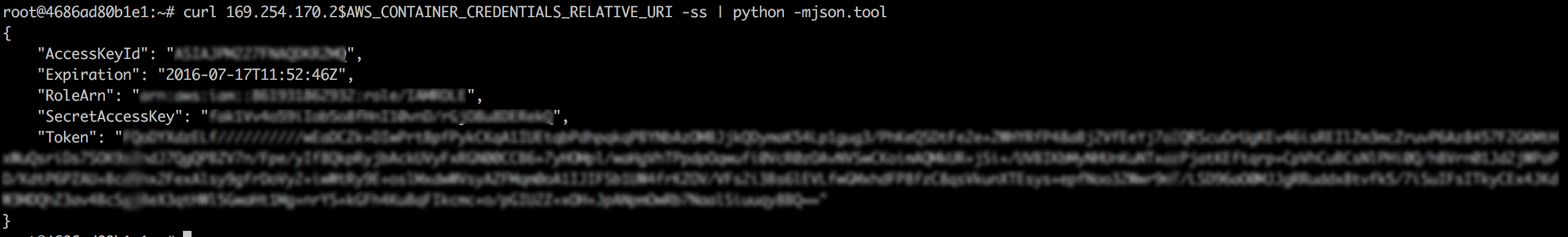
IAM Logs:
When the IAM roles for tasks credential provider is used to provide credentials to tasks, these requests are logged in/var/log/ecs/audit.log.YYYY–MM–DD–HH. Each log has an entry for TaskARN & Container Instance ARN with other entries like timestamp etc, so if you are pushing these logs on a centralized location, you can easily identify the task and the instance from which that log has been generated.
Conclusion:
- Now a container can only access the resources that are allowed in the IAM role that is defined in the task definition and can never access the credentials of another container running into the same container Instance.
- From Access log, auditing is possible, and now you can track which task from which container instance is accessing the resources.
Hope this helps you understand ECS in a better way. I will be back with another blog soon.



