Is your MongoDB publicly accessible?
MongoDB is a NoSQL database that delivers a performance oriented, highly available and scalable database system. Recently, a large number of MongoDB instances were found to be publicly accessible over the Internet. A large amount of data was leaked due to the fact that these instances were running an outdated and unpatched version of MongoDB. It is much of a misconfiguration than a vulnerability. This raises a serious question: “Is your MongoDB publicly accessible?”
What is this issue about?
In 2012, this issue was first reported. It made a database server vulnerable if they were not properly configured. The default installation of MongoDB did not have a ‘bind_ip 127.0.0.1’ option set in the mongodb.conf file. The best practice proposed was to control the database access to allow access from least possible sources. Although, this issue is being resolved in 2.6.0 version of MongoDb. The configuration file “mongod.conf”(which is located in /etc directory) has the net.bindIp address set to 127.0.0.1.
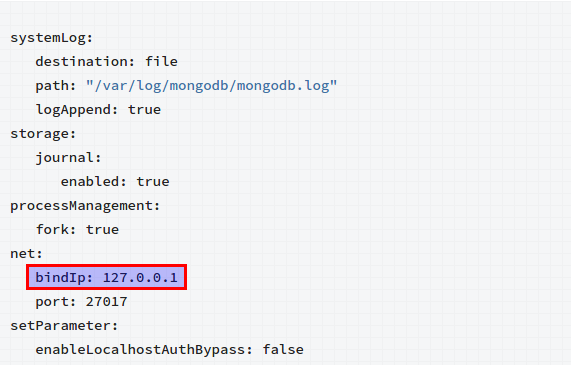
Significance of bindIp
It is the IP address that MongoDB binds to listen for connections from different applications. We can attach MongoDB to a different interface as well. To bind MongoDB to multiple IP addresses, we have to enter a list of comma separated values.
Origin of vulnerability
There are instances, such that the application which uses MongoDB probably has an authentication mechanism, but the database itself doesn’t have any authentication. Also, it is found in many cases, the database and the application using the database are present on different servers.The system adminstrator may have removed the “bind_ip” flag, in order to allow all network connections to the MongoDB database. This allows access from all untrusted network and if encryption of transmission and access control are not implemented properly, the database becomes publicly exposed.
Possible detection
- In the mongo.conf file, look for the bindIp address as 0.0.0.0 or any value that might be making it accessible from insecure and not required origins.
- We can use Mongo Management Service and set an alert to notify host being exposed to the public internet.
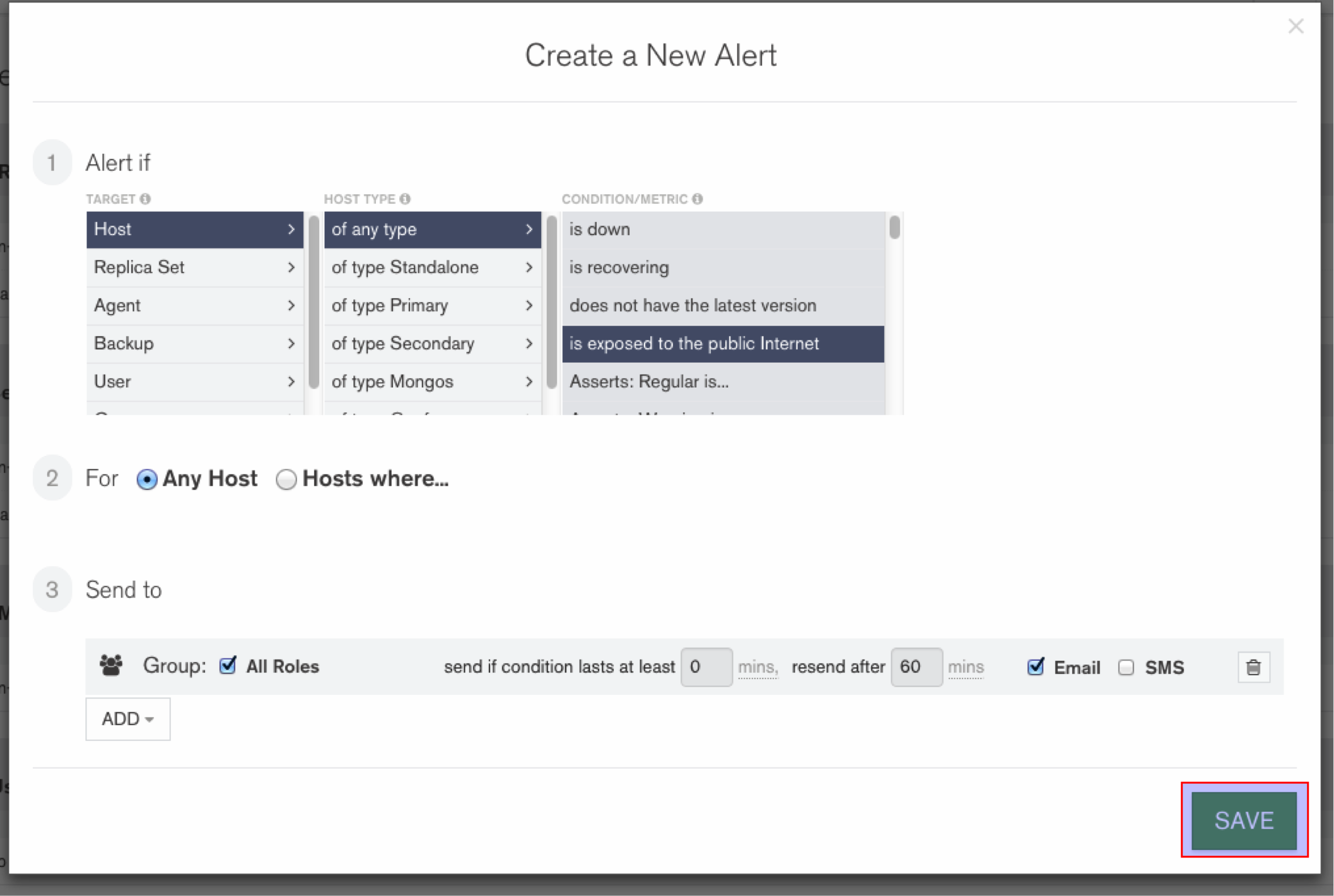
For setting up Mongo Management Service, you can follow a previous blog of mine.
How to solve this issue
- Carefully, set the bind_ip to localhost or 127.0.0.1 (avoid using 0.0.0.0 ).
- Try to use the latest version of MongoDB.
- Make sure to install all security patches of the version being used.
- Keep the MongoDB instance in a private subnet.
- Follow the Security Checklist documented by MongoDB.



