Ransomware – A CryptoViral Extortion Attack
Ransomware is malicious software that blocks access to data until the ransom is paid. An advanced type of ransomware encrypts the files on the system. Since it restricts the user from accessing their records, it can be termed as Denial Of Service attack. To get back the access to files or to get the data decrypted, the victim is demanded a ransom amount. Usually, the ransom amount is asked to be paid in bitcoins*.
*Bitcoins are a type of digital currency which operates independently of a central bank. It makes use of encryption techniques for regulating the generation of units of currency and verifies the transfer of funds. Unlike credit/debit cards, you can’t be traced based on the transaction made using bitcoins as it is entirely anonymous. When you trade in bitcoins, a private key associated with your wallet is used to generate an address. It is then associated with your transaction, but there is no personal identification information.
How does a ransomware operate?
The concept of file encrypting ransomware is called cryptoviral extortion. It is a 3 step process:
- The attacker generates a key pair, and the corresponding public key is placed in the malware. The malware is then released to the victim.
- The malware generates a random symmetric key and encrypts victim’s files and data with it. Further, the symmetric key is encrypted using the public key in malware.It results in a small asymmetric ciphertext as well as ciphertext of victim’s data. A message is displayed to the user that includes the asymmetric ciphertext and how to pay the ransom. The victim sends the asymmetric ciphertext along with the payment amount to an attacker.
- The attacker deciphers the asymmetric ciphertext on receiving the payment with their (attacker’s) private key. Now the attacker sends the symmetric key to the victim. The victim interprets the encrypted data thereby completing the crypto virology attack.
However, there have been instances when attackers refused decryption of files even after receiving the extortion money.In few cases, they demanded more money after having received the initial payment. So security experts advise against paying the ransom amount to the attacker.
How does ransomware spreads?
Attackers make use of bait to lure their victims. Bait can be anything – an attachment in mail, any file downloaded from the internet or simply by making a victim click on some link. Once a user performs any of the mentioned actions, eg., opens any e-mail attachment from the attacker, his system gets infected as the malware starts encrypting all the files. Further, it might replicate itself and move to all the victim’s contacts. Now, when the contacts access the attachment, it will further spread to their contacts and so on.
WannaCry Ransomware
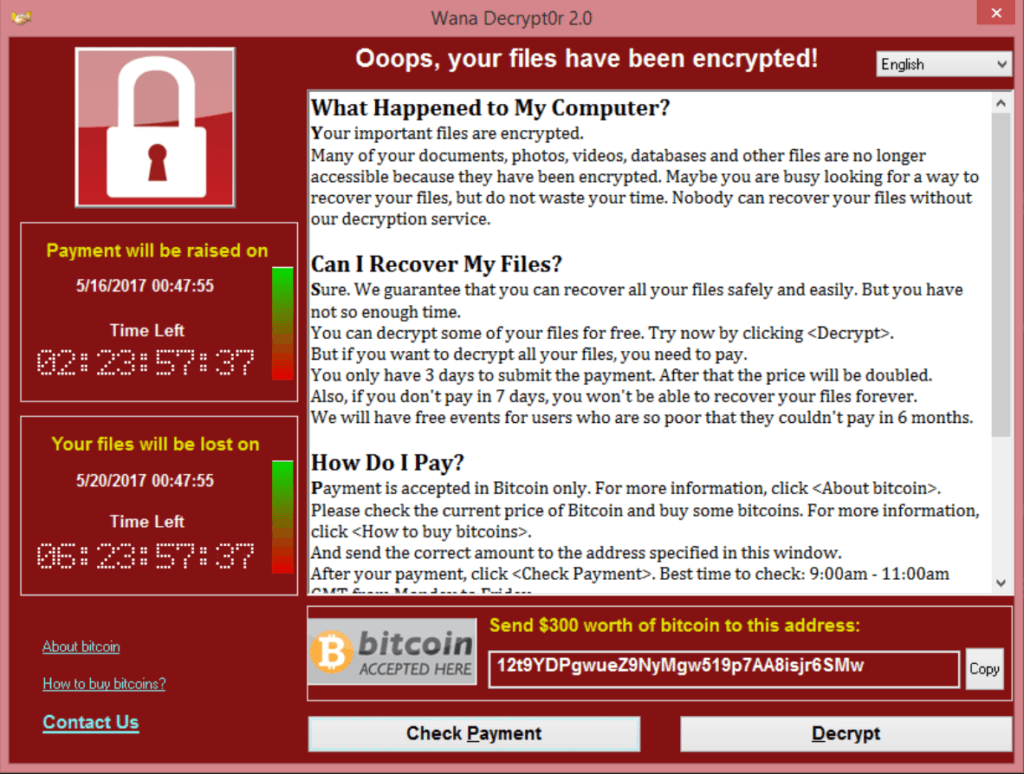
WannaCry Ransomware (or WannaCrypt or Wanna Decryptor) is an ongoing cyber-attack (at the time of writing this blog). The attack started on 12th May 2017 and just in 4 days, it infected more than 2,30,000 computers in 150 counties. This ransomware spread by phishing emails and made use of EternalBlue* exploit. People who were using unpatched and unsupported versions of operating systems, such as Windows XP and Windows Server 2003 were at risk.Microsoft took an unusual step and provided a patch for even unsupported versions.
*EternalBlue is an exploit which is believed to have been developed by NSA (National Security Agency, USA). It exploits a vulnerability in Microsoft’s implementation of Server Message Block (SMB) Protocol. This vulnerability allows attackers to send specially crafted packets on SMBv1 Server in various versions of Microsoft Windows and execute arbitrary code on target computers.
Protecting yourself from any malware
Most of such cyber-attacks are successful because people fail to follow basic security practices:
- Security Updates: Always make sure that you keep your operating system updated with latest security patches.
- Suspicious Mails: Be very alert while opening any mail from an unknown source. NEVER open an attachment or click on any link in such a mail. Sometimes you might receive an infected mail from a known source just because they accessed a malware containing mail. Now when you click on any link or access the attachment in such a mail, your contact list further receives an infected mail from you and it goes on.
- Downloading Files From the Internet: Downloading any file from internet can prove to be very dangerous as it can be a trojan or the file might be infected with virus, keyloggers or the latest threat – Ransomware
- Anti-Virus And Firewall: Always use a good anti-virus and a robust firewall even if you are not connected to the internet because pen-drives might contain the malware as well.




Informative, well explained (Y)
Thank you Deepika.