Enabling SSO with CQ5 – Part III
In previous part , we discussed protecting CQ5 author instance when CQ5 acts as a service provider (SP). In this blog post, we’ll cover how to protect any published resource/website. We’ll be using Shibboleth SP for the same.
Necessary Steps:
- Installing LDAP Server.
- Installing Shibboleth IdP.
- Installing Apache tomcat on Ubuntu.
- Configuring Shibboleth IdP.
- Installation of SP.
- Make Apache aware of shibboleth
- The configuration of Shibboleth SP and providing it to IdP.
- Protecting and accessing the CQ published resource.
Steps 1-4 have already been covered in Part I. Subsequent steps are explained below :
-
Installation of SP
Installing SP and it’s configuration was a bit difficult task for me as the existing documentation was not very clear. I would like to mention few important points and brief the installation steps below .
-
Installing Apache2
[shell]sudo apt-get install apache2[/shell]
-
Installing Shibboleth SP
Easiest way to install SP is via command line.
[shell]sudo apt-get install libapache2-mod-shib2 shibboleth-sp2-schemas[/shell]
When the installation is completed, various components of Shibboleth will be placed in appropriate directories based on the OS file system layout. You may check:
- Shibboleth configuration files will be placed at
/etc/shibboleth/and the necessary Apache configuration in/etc/httpd/conf.d/shib.conf - shibd will be installed to
/usr/sbinand may be managed using/sbin/serviceand/sbin/chkconfig - An appropriate version of
mod_shiband other pluggable modules will be installed to/usr/lib/shibboleth/ - Logs will be located in
/var/log/shibboleth/shibd.log
The installation directory structure may vary depending upon the OS version/type you are using. It might happen that some of the folders/files mentioned above might not be present in your file system. In my case, I was not able to see /etc/httpd/conf.d/shib.conf file . If same thing happens with you, then make all apache related configurations in apache2.conf file as per the apache installation directory structure in your system.
-
Initial testing can be done by hitting the URL http://localhost/Shibboleth.sso/Status .
-
Make Apache aware of Shibboleth
Tell apache where to find the mod_shib you just installed (assuming you are using Apache 2.2). Add the below line in apache2.conf file.
[shell] LoadModule mod_shib /usr/lib/apache2/modules/mod_shib_22.so [/shell]
Note : (For CQ only ) If you have enabled dispatcher, make sure you specify the above line before dispatcher loading i.e. shibd should load before dispatcher gets load.
-
Configuration of Shibboleth SP and providing it to IdP.
The way shibboleth works is by running a daemon called shibd at the same time apache runs, and then mod_shib.so knows how to talk to shibd.
-
Configure
/etc/shibboleth/shibboleth2.xmlThis file tells
mod_shibandshibdall about your setup. It is probably already full of data, but be careful – you need to configure it to know which IdP you’re connecting to. Take a backup of the original file before directly editing this one.-
Make sure the ‘entityID’ points at your machine. Update the
entityIDin<ApplicationDefaults>tag as follows . (You can provide your own ID as well)
[xml]&lt;ApplicationDefaults REMOTE_USER=&quot;eppn persistent-id targeted-id&quot; entityID=&quot;http://&lt;your domain&gt;/shibboleth&quot;&gt;[/xml]
I’ll be using as the Entity Id.
-
Configure the IdP you want to use. Provide the entity ID of the IdP configured in part I or you can simply copy the entity ID present in
<SAML_IDP_HOME>/metadata/idp-metadata.xmlfile
[xml]&lt;SSO entityID=&quot;https://idp.intelligrape.com/idp/shibboleth&quot;&gt;SAML2 SAML1&lt;/SSO&gt;[/xml]
-
Also, specify from where the IdP’s metadata will come from. At the IdP server , copy its metadata file
idp-metadata.xmllocated at<SAML_IDP_HOME>/metadatadirectory and place it at your SP server at location/etc/shibboleth/directory. Add the below tag in/etc/shibboleth/shibboleth2.xmlif not already present.
[xml] &lt;MetadataProvider type=&quot;XML&quot; file=&quot;idp-metadata.xml&quot;/&gt;[/xml]
-
-
Configure SP’s Metadata file
-
If you read the instructions at the shibboleth site they seem to VERY STRONGLY IMPLY that you need to construct your own Metadata file for an SP. It is PARTLY true. To start off with, let provide a Metadata file for you.
shibdwill create one on-the-fly and serve it to you auto-matically. -
Copy and paste the contents in a file say
sp-metadata.xml. Save this file to the location<SAML_IDP_HOME>/metadata. Once you create or acquire metadata for SP, you must supply it to the IdP. Similarly, the IdP MUST supply its metadata to the SP which was already done in the previous step. -
At IdP server add the following to the
relying-party.xmlfile (at <SAML_IDP_HOME>/conf/) just after the IdP’s own metadata is defined:
[xml]&lt;metadata:MetadataProvider xsi:type=&quot;FilesystemMetadataProvider&quot; xmlns=&quot;urn:mace:shibboleth:2.0:metadata&quot;
id=&quot;SPMETADATA&quot; metadataFile=&quot;&lt;SAML_IDP_HOME&gt;/metadata/sp-metadata.xml&quot;/&gt;[/xml] -
- In relyingParty.xml, we need to specify the details of IdP’s metadata and any other service provider’s metadata file that relies on our IdP. IdP’s metadata file is already provided in Part I. While specifying the relying party and metadata of SP, value of Provider attribute in
<rp:RelyingParty>tag should be the same as that of EntityId specified in above metadata file. Also, changeencryptAssertionsattribute to “never”.[xml]&lt;rp:RelyingParty id=&quot;my.domain.com&quot; provider=&quot;http://my.domain.com/shibboleth&quot; defaultSigningCredentialRef=&quot;IdPCredential&quot;
defaultAuthenticationMethod=&quot;urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport&quot;&gt;
&lt;rp:ProfileConfiguration xsi:type=&quot;saml:SAML2SSOProfile&quot; inclu deAttributeStatement=&quot;true&quot;
assertionLifetime=&quot;PT5M&quot; assertionProxyCount=&quot;0&quot;
signResponses=&quot;never&quot; signAssertions=&quot;always&quot;
encryptAssertions=&quot;never&quot; encryptNameIds=&quot;never&quot;
includeConditionsNotBefore=&quot;true&quot;/&gt;
&lt;rp:ProfileConfiguration xsi:type=&quot;saml:SAML2ArtifactResolutio nProfile&quot; signResponses=&quot;never&quot; signAssertions=&quot;always&quot;
encryptAssertions=&quot;never&quot; encryptNameIds=&quot;never&quot;/&gt;
&lt;/rp:RelyingParty&gt; [/xml] -
Modify the
/etc/shibboleth/attribute-map.xmlfile to have list of all the attributes being released from IdP. There are already a lot of attributes mentioned in the file but are commented out. You can find out your own attribute and uncomment it or you can use the below.
[xml]&lt;Attribute name=&quot;urn:mace:dir:attribute-def:uid&quot; id=&quot;uid&quot;/&gt;[/xml]
-
Protecting and accessing the CQ published resource.
-
In apache2.conf , enable the dispatcher if not already enabled. You can refer the existing documentation or this excellent blog can be followed.
-
We can use shibboleth to secure the published content. Only authenticated users can access a resource , otherwise the request should not be processed. Below is the block diagram for how the request is processed.
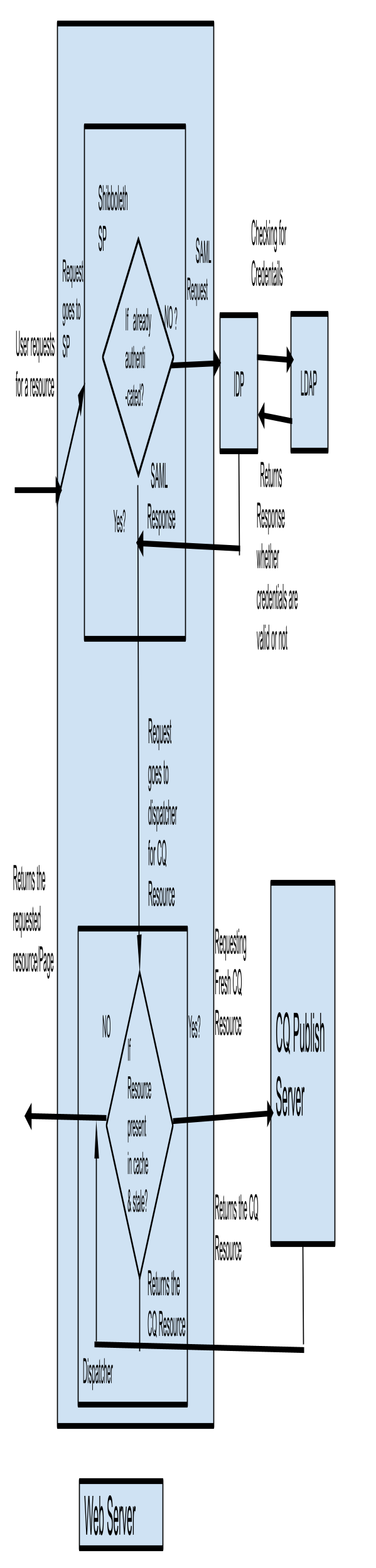
-
In order to check that SP is working, protect a directory by acquiring a shibboleth session. Add the below in
shib.conf(if present in your system) , otherwise you can specify the same inhttpd.conffile. For ubuntu , you can specify it in the file where virtual hosts entries are present. In my case it was/etc/apache2/sites-available/default. It may vary depending upon the installation structure.[xml]&lt;Location /path/to/secure/content&gt;
# this Location directive is what redirects apache over to the IdP.
AuthType shibboleth
ShibRequestSetting requireSession 1
require valid-user
&lt;/Location&gt;[/xml]Note that the path mentioned in Location element is relative to the Directory root. A sample configuration can be found at the end of the document.
- Try to access the published page , you should be presented with a IDP login page. Pass the valid credentials to access the page.
-
Note that this configuration can be used to protect any cached website/directory. This implementation is not just limited to CQ.
Troubleshooting :
-
Please make sure to restart tomcat to reflect the changes you do in IdP’s configuration files. For starting/shutting tomcat , go to <TOMCAT_HOME>/bin and run the startup.sh/shutdown.sh respectively.
-
Restart apache server after every change in the apache.conf files.
-
If you have enabled dispatcher module for CQ, make sure you enable it for CQ cached directory only to avoid unwanted errors.
[xml]&lt;Directory /path/to/CQ/cached/content&gt;
&lt;IfModule disp_apache2.c&gt;
SetHandler dispatcher-handler
&lt;/IfModule&gt;
Options FollowSymLinks
AllowOverride None
&lt;/Directory&gt;[/xml]
-
When you access the published page, make sure not to specify the port no <4503>.
-
Sample Virtual Host Entry in apache configuration .
[xml]&lt;VirtualHost *:80&gt;
ServerAdmin webmaster@localhost
ServerName publish.intelligrape.com
DocumentRoot /var/cache/apache2/cq-cache
&lt;Directory /&gt;
Allow from all
Options FollowSymLinks MultiViews
AllowOverride None
&lt;/Directory&gt;
&lt;Location /content&gt;
AuthType shibboleth
ShibRequireSession On
require valid-user
&lt;/Location&gt;
ErrorLog ${APACHE_LOG_DIR}/error.log
LogLevel warn
CustomLog ${APACHE_LOG_DIR}/access.log combined
&lt;/VirtualHost&gt; [/xml]
Reference Links
http://csrdu.org/blog/2011/07/04/shibboleth-idp-sp-installation-configuration/
http://www.jeesty.com/shibboleth
https://wiki.shibboleth.net/confluence/display/SHIB2/Installation
http://www.switch.ch/aai/support/serviceproviders/sp-access-rules.html




Thank you Geetika, the blog is really very helpful.
I am facing an issue to integrate AEM 6.1 with OKTA SSO. I provide following configuration in OKTA end. 1) SP URL, 2) NameIDFormat – “urn:oasis:names:tc:SAML:2.0:nameid-format:transient” rest of the configurations are default. In AEM end I provide following information, 1) IDP URL (OKTA URL), 2) Service Provider Entity ID, 3) Create trust store by supplying the password & then upload the IdP certificate 4) Create KeyStore by supplying the password 5) Rest of the configuration I did as per the “http://www.aemstuff.com/blogs/july/saml.html” URL. But when I am trying to execute the AEM I am getting “com.adobe.granite.auth.saml.SamlAuthenticationHandler Private key of SP not provided: Cannot sign Authn request” warning and the screen is blinking continuously. I may have to provide some public or private key, but I am not sure who will provide that key and where I have to import that. Could you please help me on this issue?
Thanks
Tridib
Thanks for your efforts, i found your blog very helpful.
I have a question that definitely was not required to be covered in this blog but is a requirement in our scenario. The IDM we are connecting with only give us Authentication, for authorization we are relying on CQ. So how do I invoke a sling auth handler , create a CQ session and can get the user’s permission?