Configure NAT Instance on AWS
The purpose of this blog post is to configure NAT (network address translation) instance on AWS by setting up customized Virtual Private Cloud (VPC) . AWS EC2 Instances that we have launched into a private sub-nets in a VPC can’t communicate with the Internet. So we use NAT instance launched in our public sub-net in our VPC to enable instances in the private sub-nets to initiate outbound traffic to the Internet, but prevent the instances from receiving inbound traffic by someone on the Internet for security reasons.NAT is a methodology of remapping one IP address into another by modifying network address information in internet protocol data-gram packet headers while they are in transit across a traffic routing device.
NAT is the process where a network device, usually a firewall, assigns a public address to a server (or group of servers) inside a private network. The main use of NAT is to limit the number of public IP addresses for both economy and security purposes.
Brief Overview to configure NAT instance on AWS ::
- Create a VPC with two sub-nets (Public and Private Sub-net)
- Launch Instance in each sub-net.
- Modify the security groups (Inbound & outbound rules) for each instance launched in public and private sub-net.
- Download NAT instances AMI (Amazon Machine Image) from AWS Community AMI’s
- Edit routing tables
- Disabling Source/Destination Checks for NAT instance.
Steps to configure NAT:
- Create a VPC “Nat_Testing_VPC” with two sub-nets one “Nat_Testing_Private” and other “Nat_Testing_Public“
- We launch our NAT instance AMI in Public sub-net “Nat_Testing_Public” inside our VPC “Nat_Testing_VPC“
VPC “Nat_Testing_VPC” CIDR range : 10.0.0.0/24
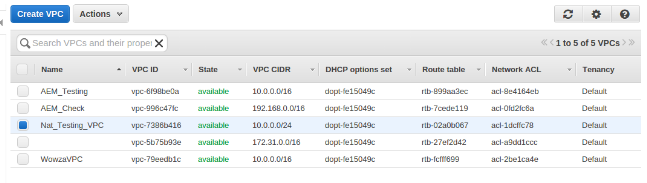
Sub-nets CIDR range:”Nat_Testing_Private” :10.0.0.128/25
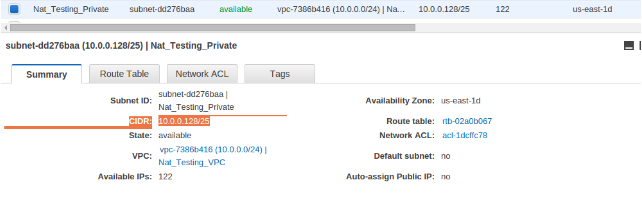
CIDR range:”Nat_Testing_Public“:10.0.0.0/25
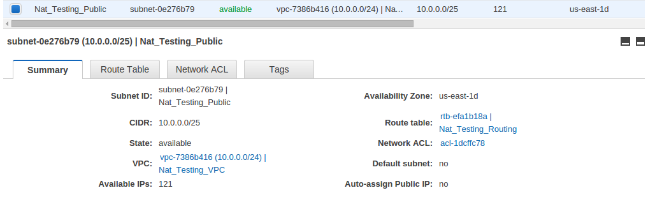
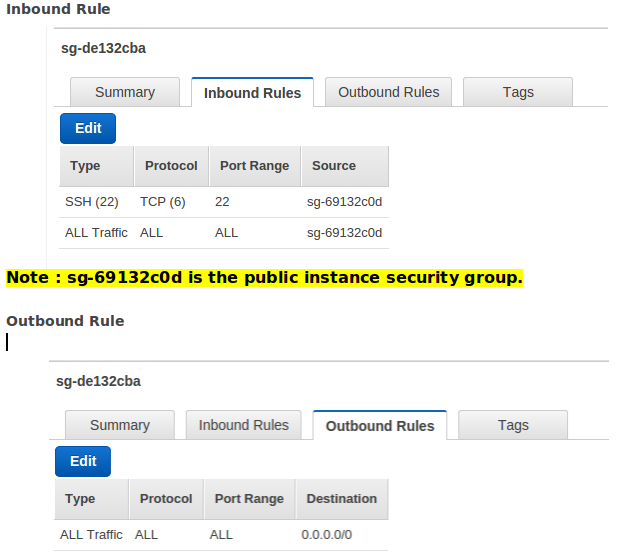
- Modify the security groups (Inbound & outbound rules) for each instance launched in public and private sub-net.
Security Group for NAT Instance .
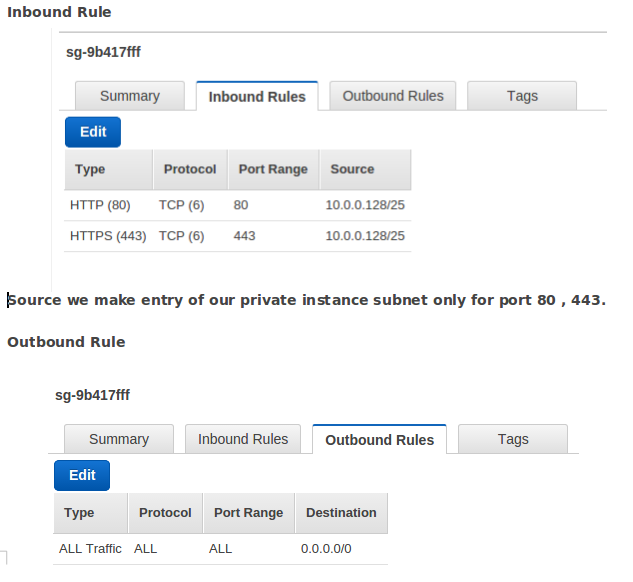
Security Group for Instances in “Nat_Testing_Private” sub-net.
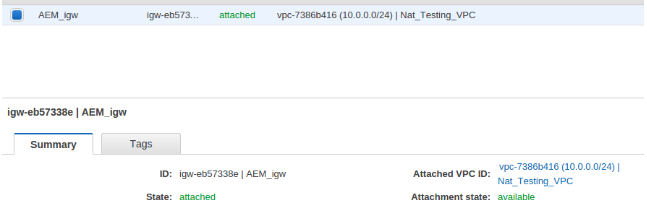
- To route the traffic to our VPC “Nat_Testing_Public” then we create the igw “AEM_igw” (Internet Gateway) and attach it to VPC “Nat_Testing_Public”.
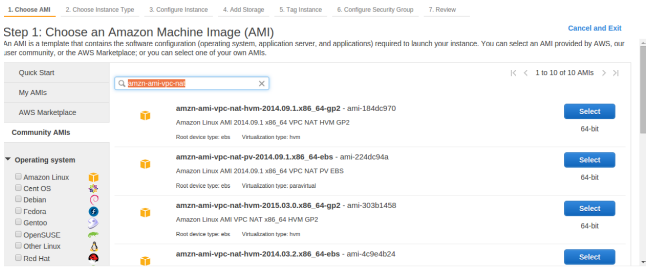
- By launching NAT instance in public sub-net “Nat_Testing_Public” inside our VPC “Nat_Testing_VPC” by using the AMI from “Community AMI“. Search the AMI by name “amzn-ami-vpc-nat“.
Note: Please enable the auto assign public ip for NAT instance (only for instances launched in Nat_Testing_Public sub-net )
- A route table specifies how packets are forwarded between the sub-nets within your VPC, the Internet, and your VPN connection so we need to create routing table “Nat_Testing_Routing_public” for the same.
Note:Next step to edit the ROUTES in our Routing table “Nat_Testing_Routing_public”
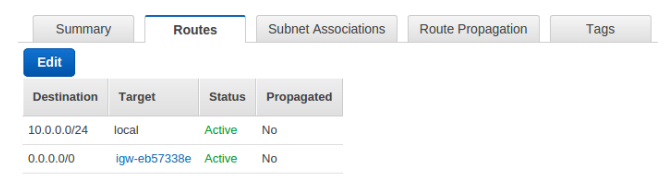
With this entry, we define routes for Internet via Internet Gateway attached to our VPC.
- By Associate public sub-nets with below routing table “Nat_Testing_Routing_public“.
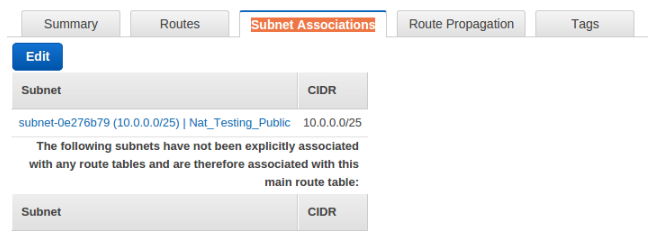
- By Default in AWS account we get default Routing table called Main Routing table and we are not going to make changes in the Main Routing Table.(Not recommended to make changes in MAIN routing table )
- So we created new routing table “Nat_Testing_Routing_private” and attached “Nat_Testing_Private” sub-net through Sub-nets Associations to initiate traffic flow. In below image Routes for this table.
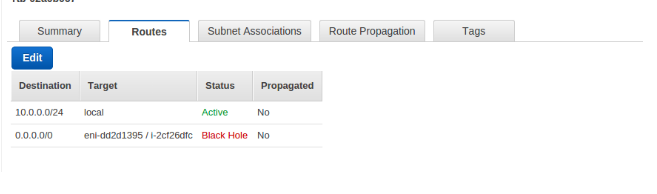
Note :: [0.0.0.0/0 eni-dd2d1395 / i-2cf26dfc ] (0.0.0.0/0 nat-instance-id) Routing Table to route the traffic from EC2 instances in private sub-nets to internet through NAT instance.
Status is showing Black Hole because my NAT instances are in stop state.
- Last step to Disabling Source/Destination Checks for NAT instance
Each EC2 instance performs source/destination checks by default. This means that the instance must be the source or destination of any traffic it sends or receives. However, a NAT instance must be able to send and receive traffic when the source or destination is not itself. Therefore, you must disable source/destination checks on the NAT instance




It’s not working.