How I discovered RCE through a Misconfigured plugin
We have seen a lot of applications where some sub-domains or sub-directories are publicly exposed (intently or by mistake). So, with experience from our past pentests we have made a habit of testing for vulnerable or accessible sub-domains.
During one of such testing, I was manually testing the URLs of different sub-domains of the application and found a sub-directory which appeared interesting to me, so I went ahead to test it. It was a surprise to see grails console opening up. So, entering a Linux command in it was the next thing that one will do and waited for the response of the same.
But the result was not as per my expectation as the command did not yield any result. Then I went forward and reloaded the page, to my surprise the command did got executed this time. And a complete list of usernames along with their respective password (which were present on this local system/server) was fetched as an output on the screen. The following is the screenshot of the same:
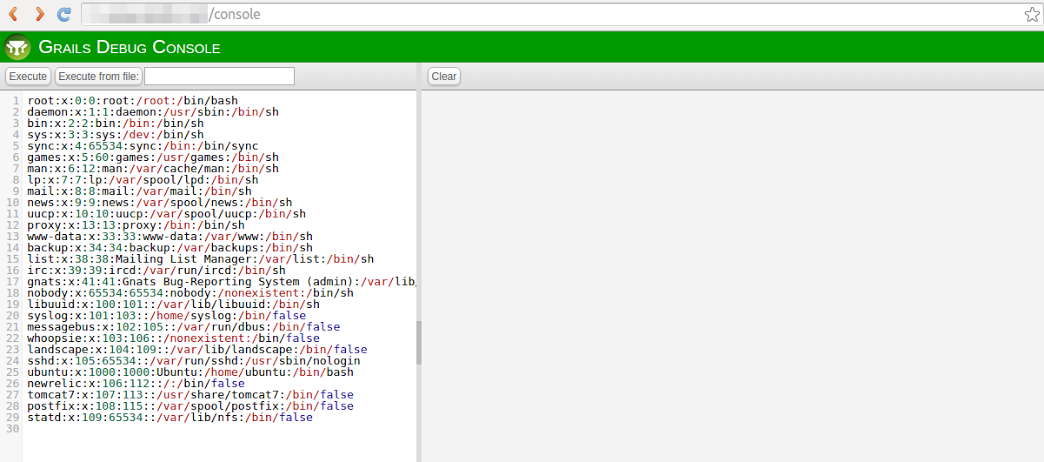
What took me by surprise is that this sub-domain could have been easily found through Google dorking. There was no restriction on the particular page of the application i.e. based on IP Address. This made me think about the necessity of having a proper check over consoles which can execute Remote Code Execution. So, this blog post will be covering the devastating impact of a publicly exposed console and how to protect this from happening.
There are different ways to search for the possible sub-directories such as:
– Google dorking or using a tool such as Knockpy or Wfuzz.
Following are the detailed demonstration of performing directory fuzzing in applications:
Use of fuzz to enumerate sub-directories
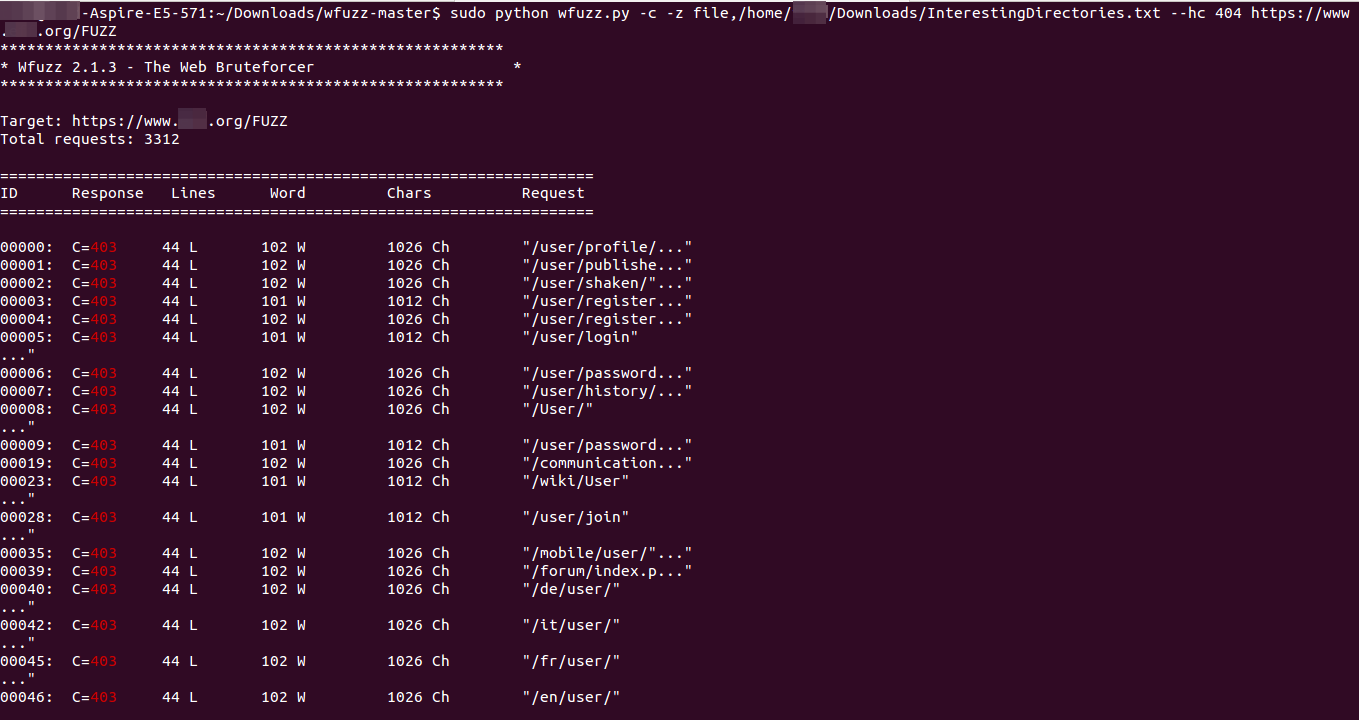
The above-mentioned command has the following components:
-c argument is for color output.
-z is for a file as a payload and the path of the file is given after a coma.
–hc 404 is used for hiding the pages that fetched a 404 error response.
/FUZZ is used in the place where the payload has to be inserted.
The trick that one should follow is observing the response codes and the length of response received. If you observe the screenshot, the value C=403 is the response code which can be the following:
200 OK
302 Found
404 Not found
For the complete list of HTTP Status Code, refer to the following link.
So, while fuzzing an application for sub-directories one should look for successful response codes such as 200 (302 at times). Also, there might be a case where two pages will be giving the same response code but different length of response. In such scenario, one should always manually traverse the sub-directory.
Possible Impacts of Publicly Accessible Console
The console can be used to perform RCE(Remote Code Execution). A RCE is code execution technique used to execute any commands of the attacker’s choice on a target machine. A program that made possible successful execution of a command is called code execution exploit. In this case, Grails console was the exploit entry point. This vulnerability allows the execution of code or command and therefore mostly used to inject and execute a shell script to give an attacker an easy way to manually execute commands.on victims server/system. Since an attacker is able to execute code from one machine on another (especially via a wide-area network such as the Internet), this attack is referred as remote code execution.



