JOSE Encryption and AEM Keystore Integration
What is JOSE?
JOSE or JSON Object Signing and Encryption , in brief, is a framework intended to provide a method to securely transfer claims (such as authorization information) between parties. The JOSE framework provides a collection of specifications to serve this purpose.
One big plus for this framework is that it has excellent support in most programming languages.
Usages
JOSE encryption can be used for encryption of token along the network for maintaining authenticity.
We used it for securing payments on our website. According to RBI circular “ An appropriate level of encryption and security shall be implemented in the digital payment ecosystem.”
Other use cases are Security Tokens, OAuth, Web Cryptography, XMPP.
Understanding the structure
Now these are the things that comprise the JOSE standard.
- JWK : JSON Web Key (Public Key shared over the network in JSON format)
- JWS : JSON Web Signature. So this is a serialized message with 3 (.) separated strings of below format.
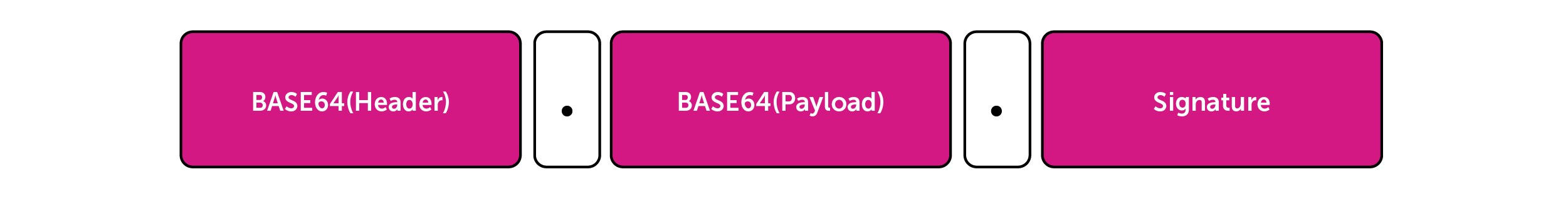
- JWE : JSON Web Encryption. This is a serialized message with 5 (.) separated strings of below format.

This is how the decryption works at the receiver end.
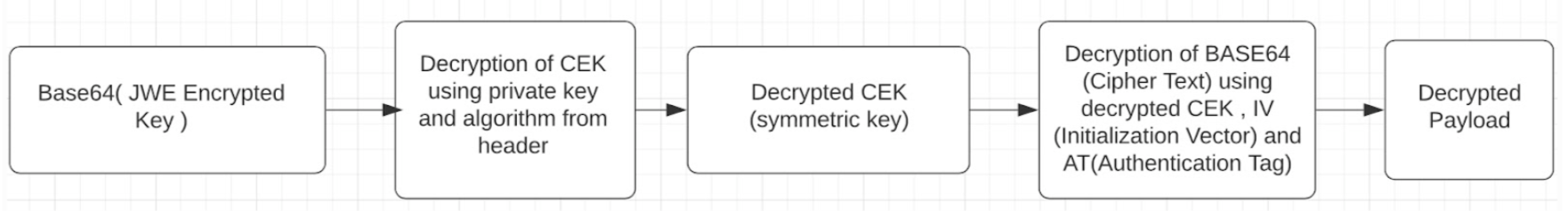
This blog talks about integration of JOSE with an application hosted on AEM utilizing AEM keystore for safekeeping of key pairs i.e. Public and Private Keys.
Here are the four steps required to follow:
1. Storing Encryption Keys in AEM
Firstly let’s go through the process of storing keys on AEM.
Here are the Adobe documentation link for keystore and truststore setup. Using these steps you can store receivers public certificate in truststore and senders private public key pair in keystore for safekeeping.
This complete the cert setup.
2. Fetching Keys
Next is fetching these certificates. I am using RSA keys in the project which are the most commonly used type of encryption keys in asymmetric encryption techniques.
Check code from the repo below for understanding how to fetch keys from Keystore and trustore.
KeysUtil.java
3. Using the Library
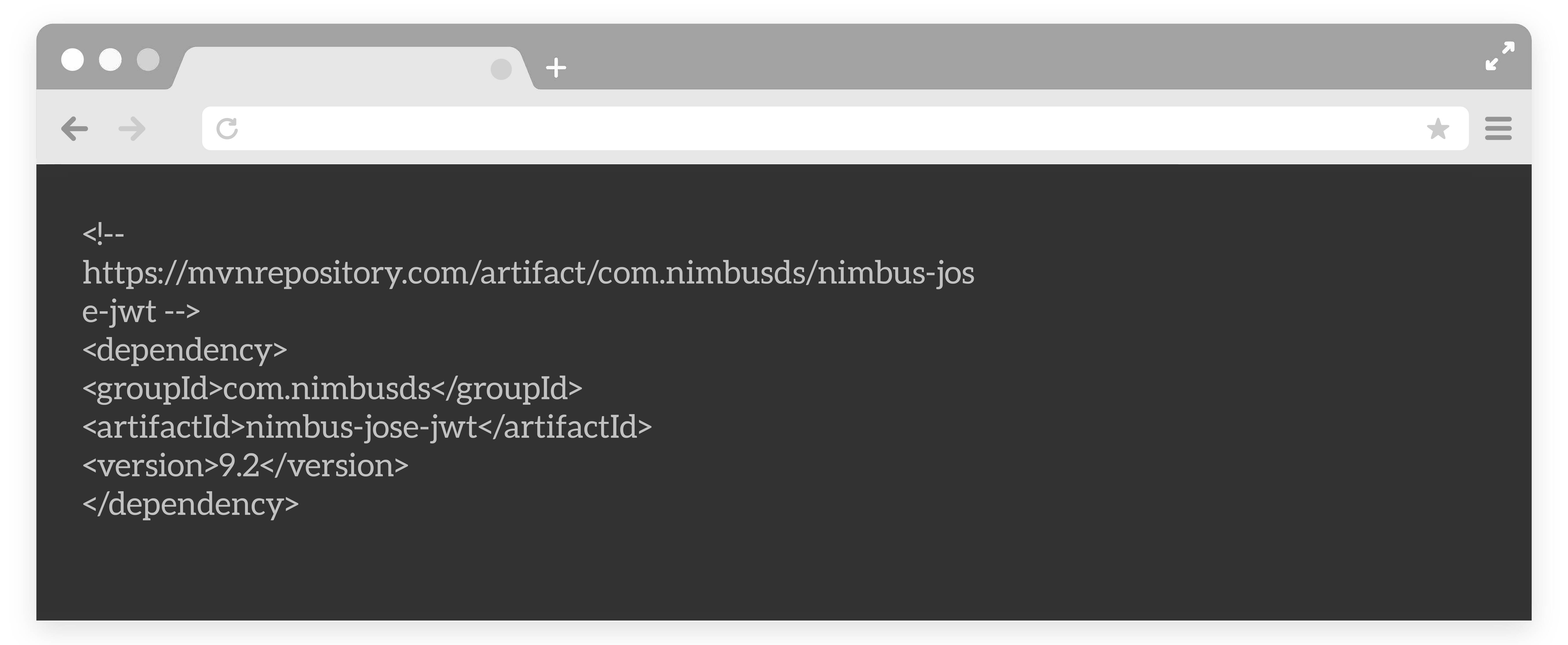
We are using nimbus-jose-jwt maven dependency in our project.
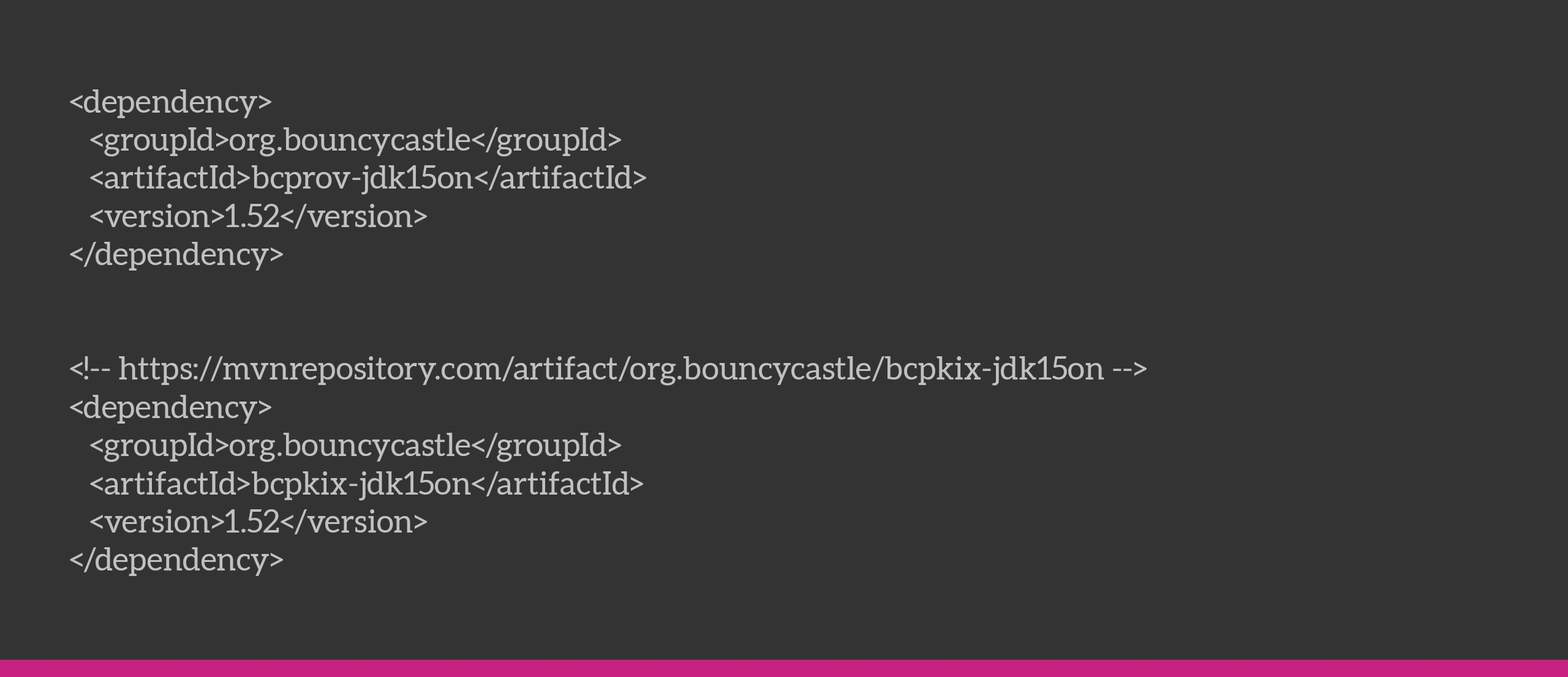
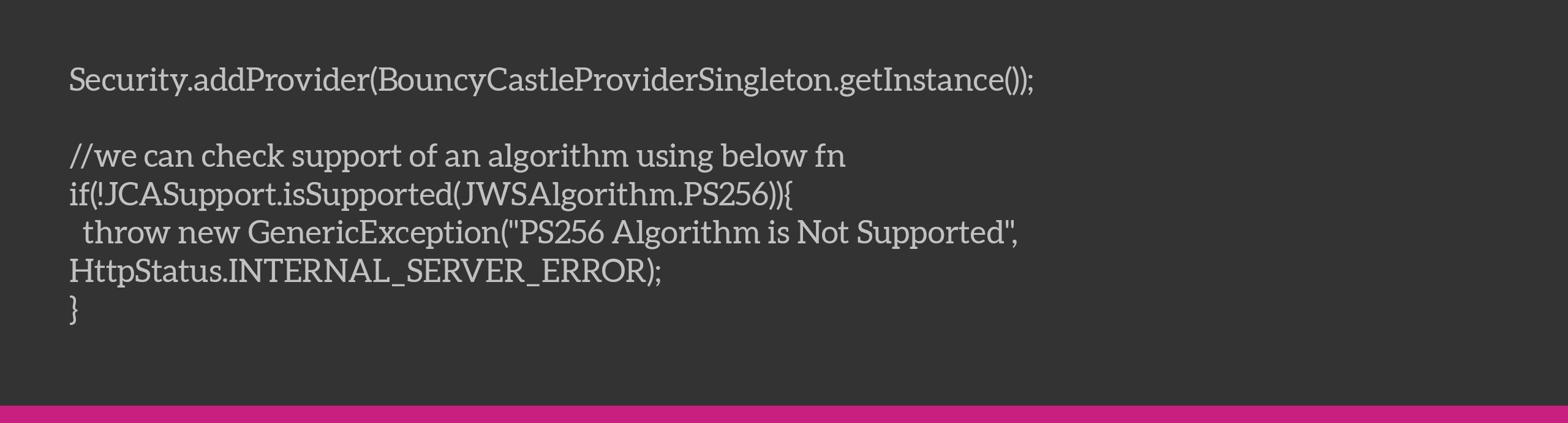
Nimbus also doesn’t provide support for PS256 right away, but using BouncyCastle provider we can ensure the same. We also tried with the JOSE4j library but we couldn’t use that one because it did not have support for PS256 encryption, which is a rather scarcely used encryption algorithm.
As you’ll be seeing below, we are using this algorithm for signing our JWT web token.
Now what we need to do is make sure this line gets executed at the start to allow the PS256 algorithm to work for Nimbus JOSE.
4. Performing JOSE Encryption
Check the functions for encryption and decryption in the repo below.
JoseUtil.java
References
- No way, JOSE! This is a ppt that covers the basics of hashing and encryption along with some insights to prevalent encryption algorithms. Then it gives a detailed insight into the workings of JOSE.
- JWT.io This is the documentation for JSON Web Token that can cover your interests in JWT.
- No Way JOSE! Cryptography & Encryption – JS Monthly London – January 2021: This is the presentation on the above mentioned PPT. Great watch!
- The RSA Encryption Algorithm (1 of 2: Computing an Example): Now this is something of interest if you are geeky about the math of the RSA encryption Algorithm and its basic working. It has 2 very short parts, part1 and part2. Definitely recommended. Very well explained.

