Creating And Importing IAM User to Opsworks
Opsworks is a wonderful SaaS tool provided by AWS which off-loads human driven tasks like managing own chef server, installing agents on each server, creating ssh user(s) even on run-time for the servers and various other benefits.
In this blog an IAM User will be created without any CLI credentials, it will be registered with opsworks, a .pem file will be used to login and create a public key to allow the user(s) ssh into server(s).
Creating an IAM User
Go to IAM Service from AWS Console.
Click on Users(On the left side of the Page)
And then click “Create New Users”
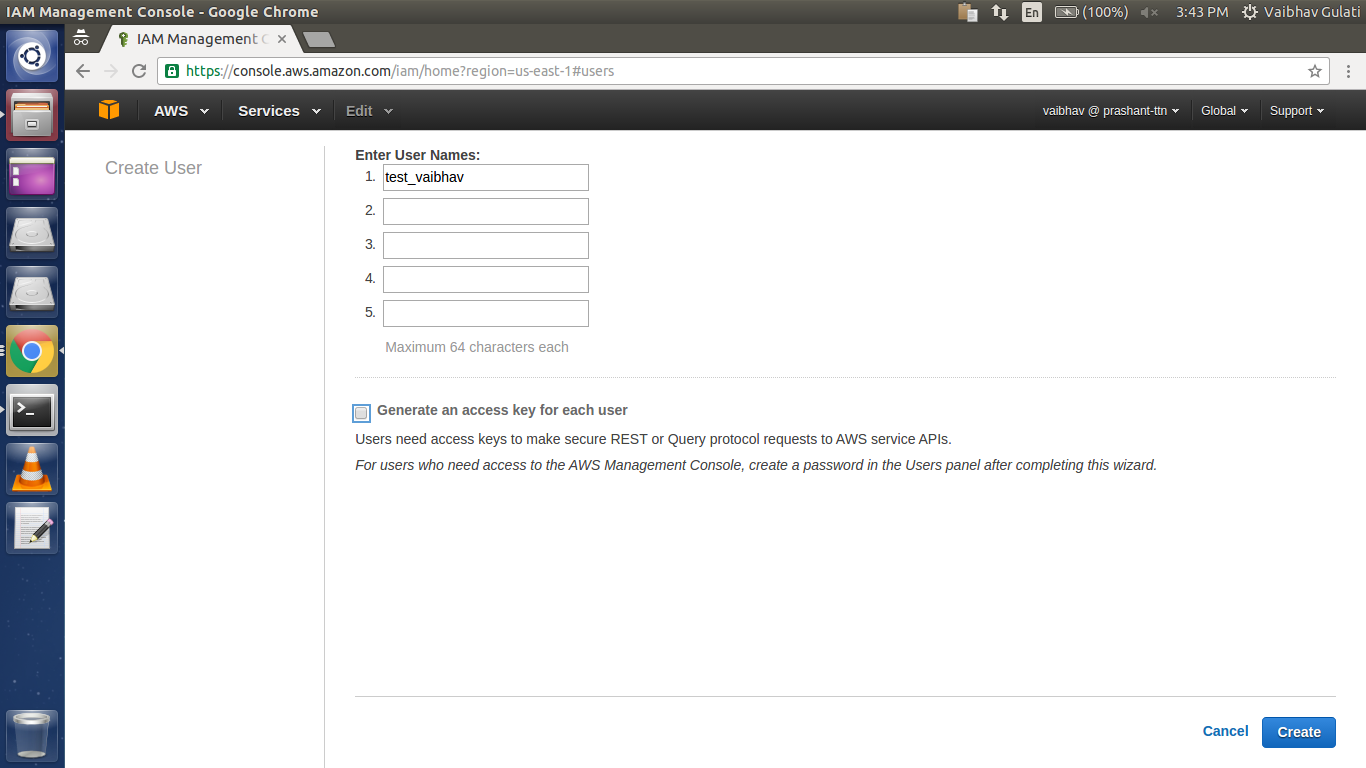
Specify the name of the IAM user to be created, uncheck “Generate an access key for each user” (access key(s) are required for giving CLI access to users) and then click “Create”.
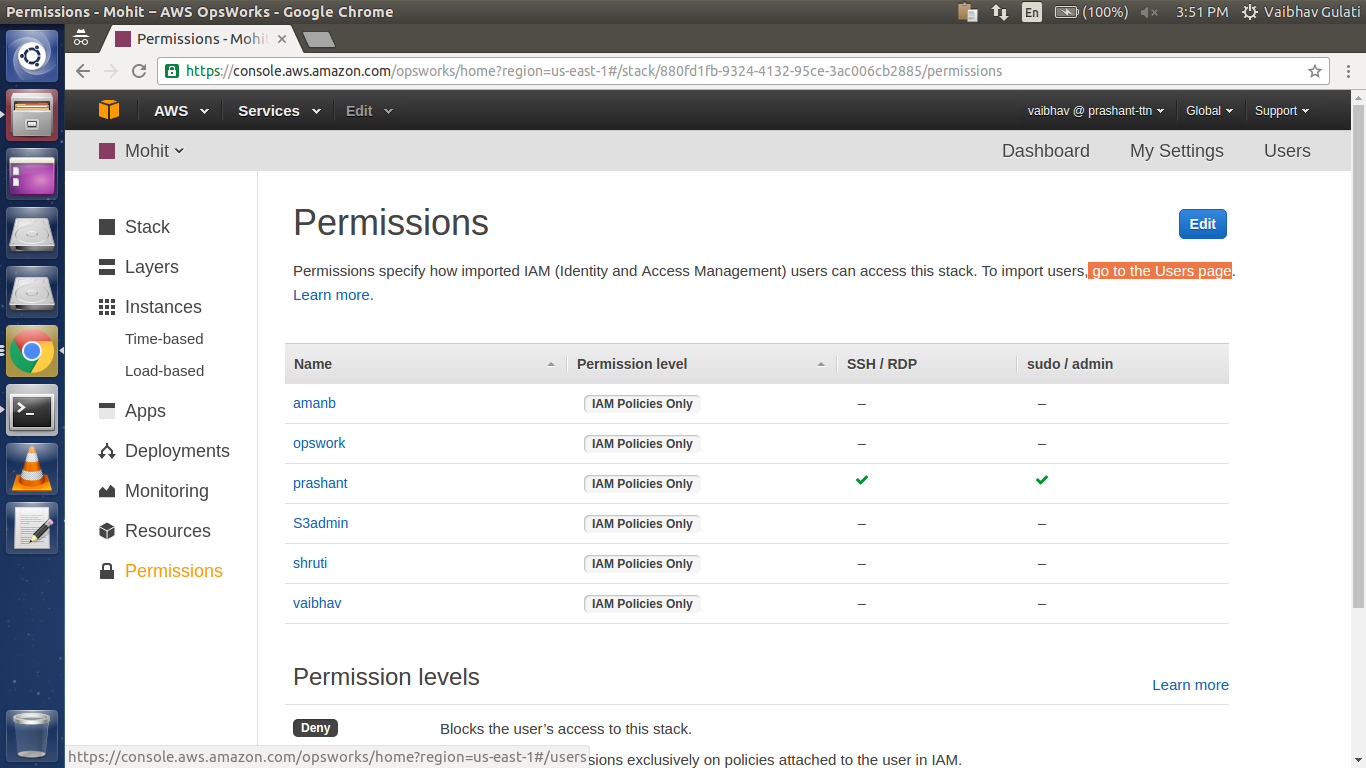
Now in Opsworks console, select “Permissions” then click Users link below the Edit button.
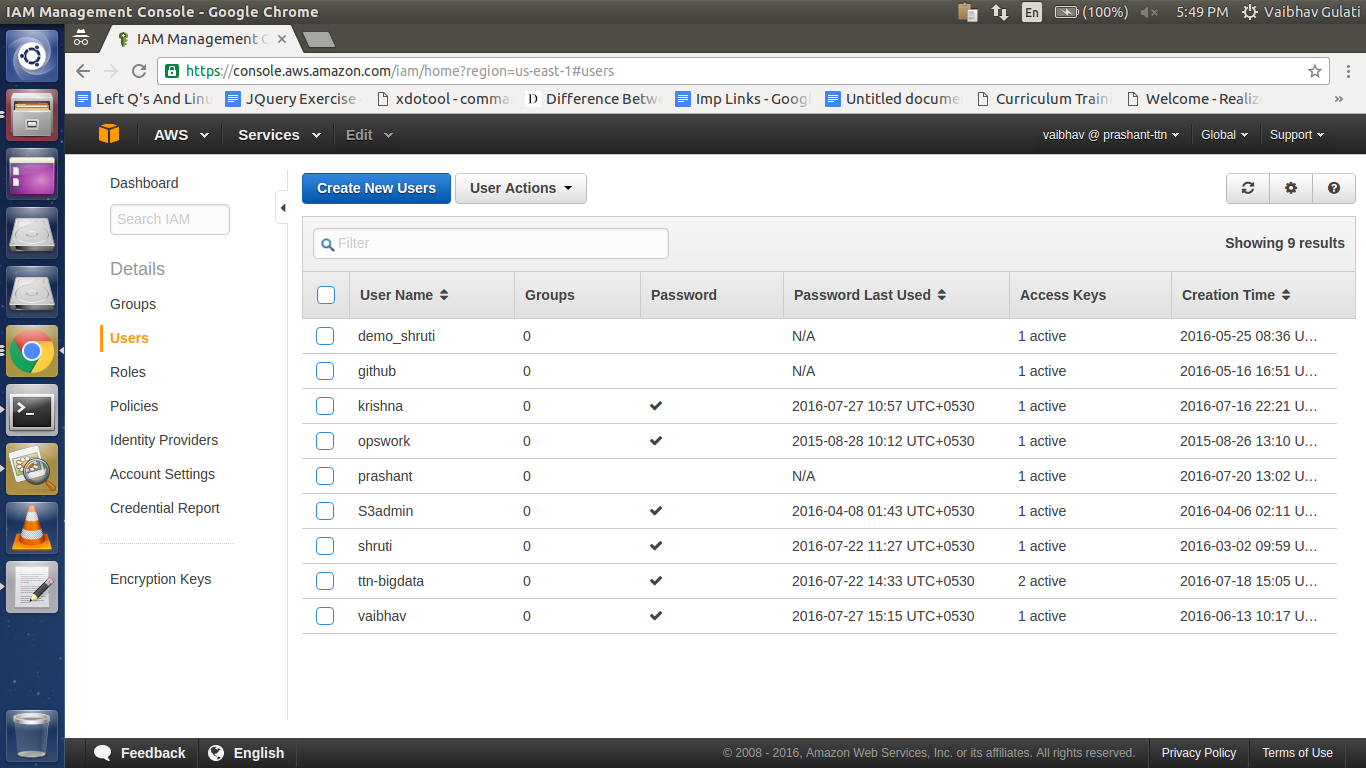
After getting into Users page
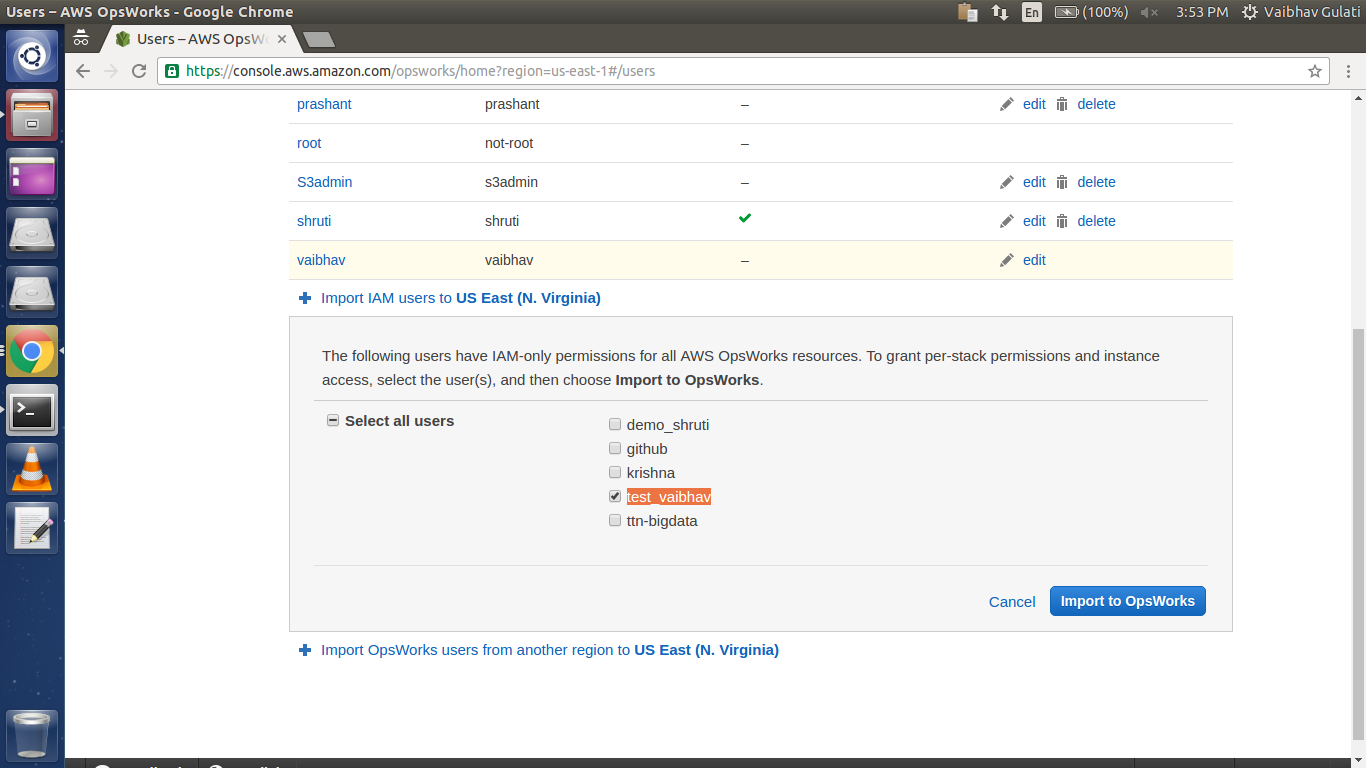
Click “Import IAM users to ‘Selected_Region_Name’ ”
And choose the required user.
Or to Import Users from different region
Click Import “OpsWorks users from another region to ‘Selected_Region_Name’ ”
After importing, it will reflect in the Users list as:
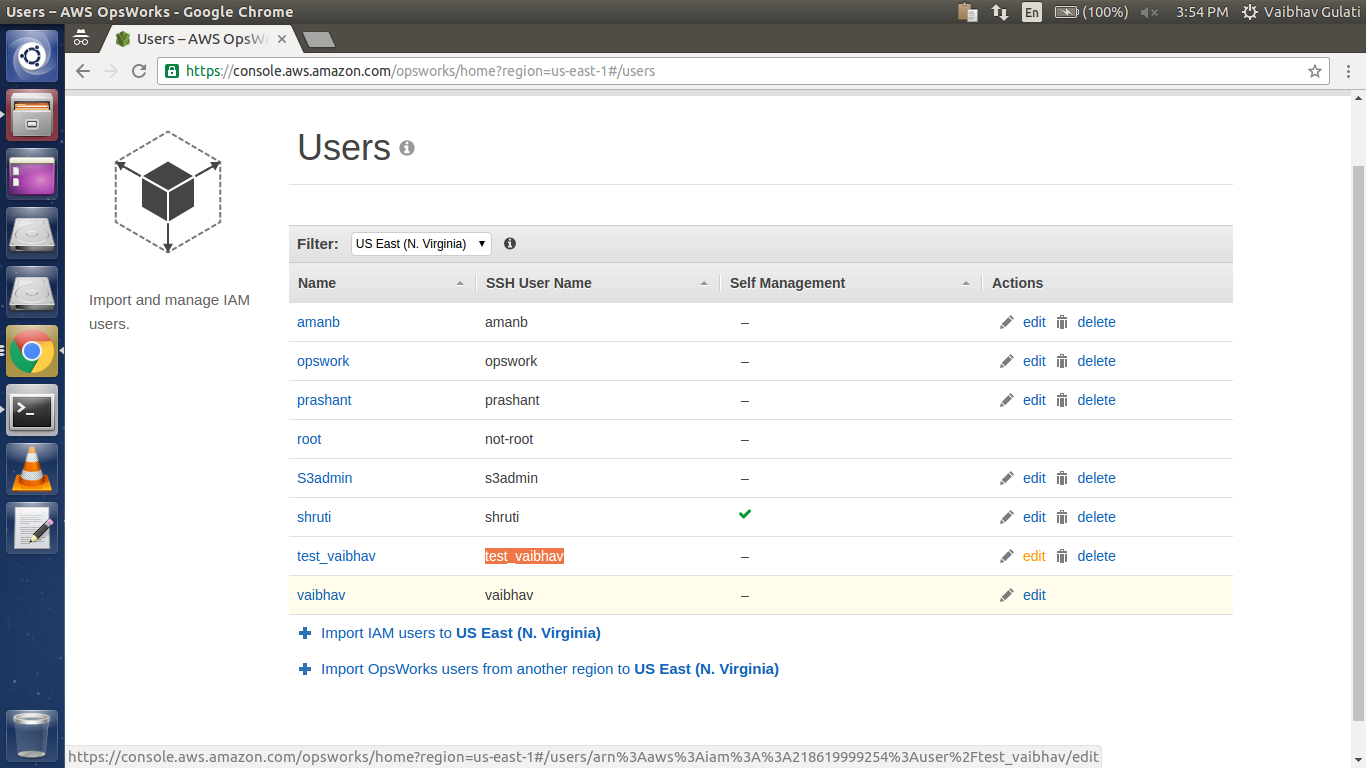
Click on “edit” to change it’s permissions and to provide its public key for ssh.
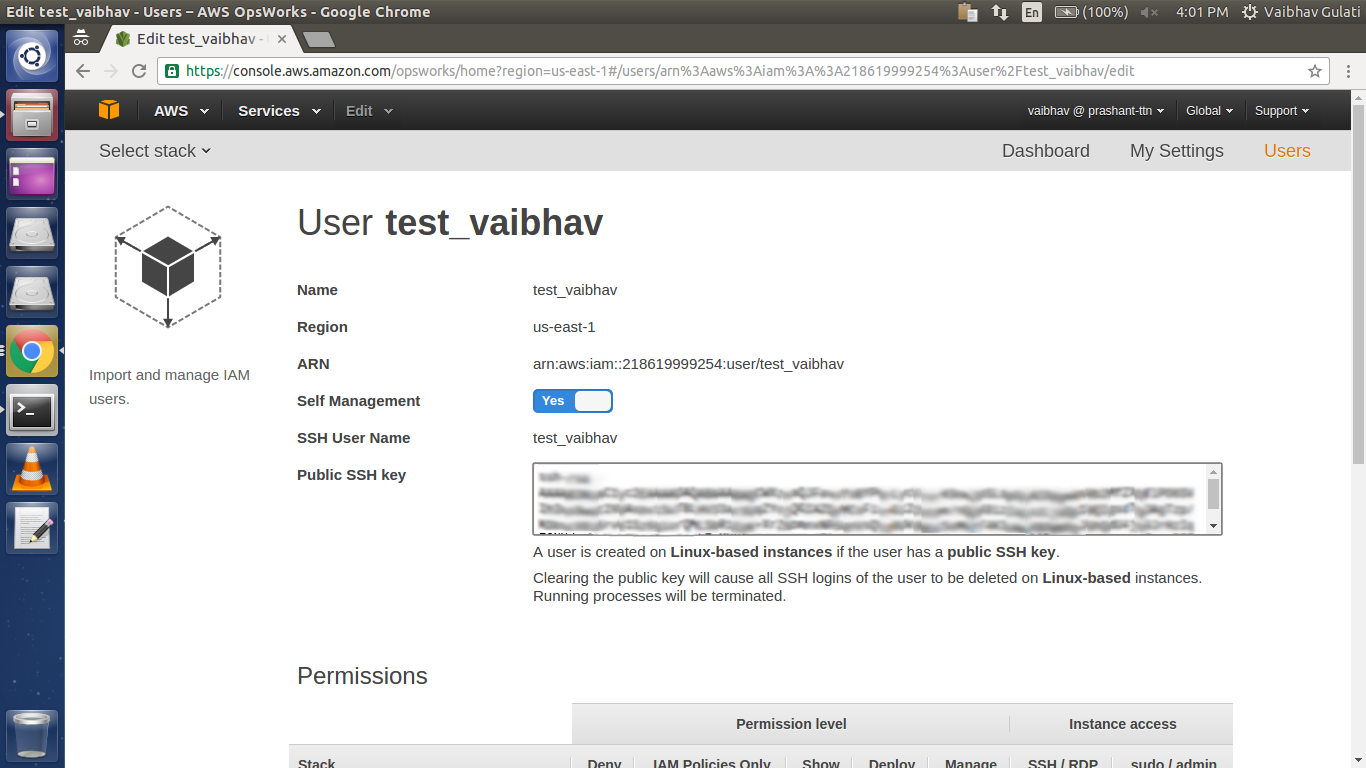
Keep Self Management to “Yes”, to put your own “Public SSH key”.
To generate public key from private key(.pem file) :
[sourcecode language=”bash”]
ssh-keygen -y -f <path_to_.pem_file> > test_vaibhav.pub
cat test_vaibhav.pub
[/sourcecode]

Granting Permissions:
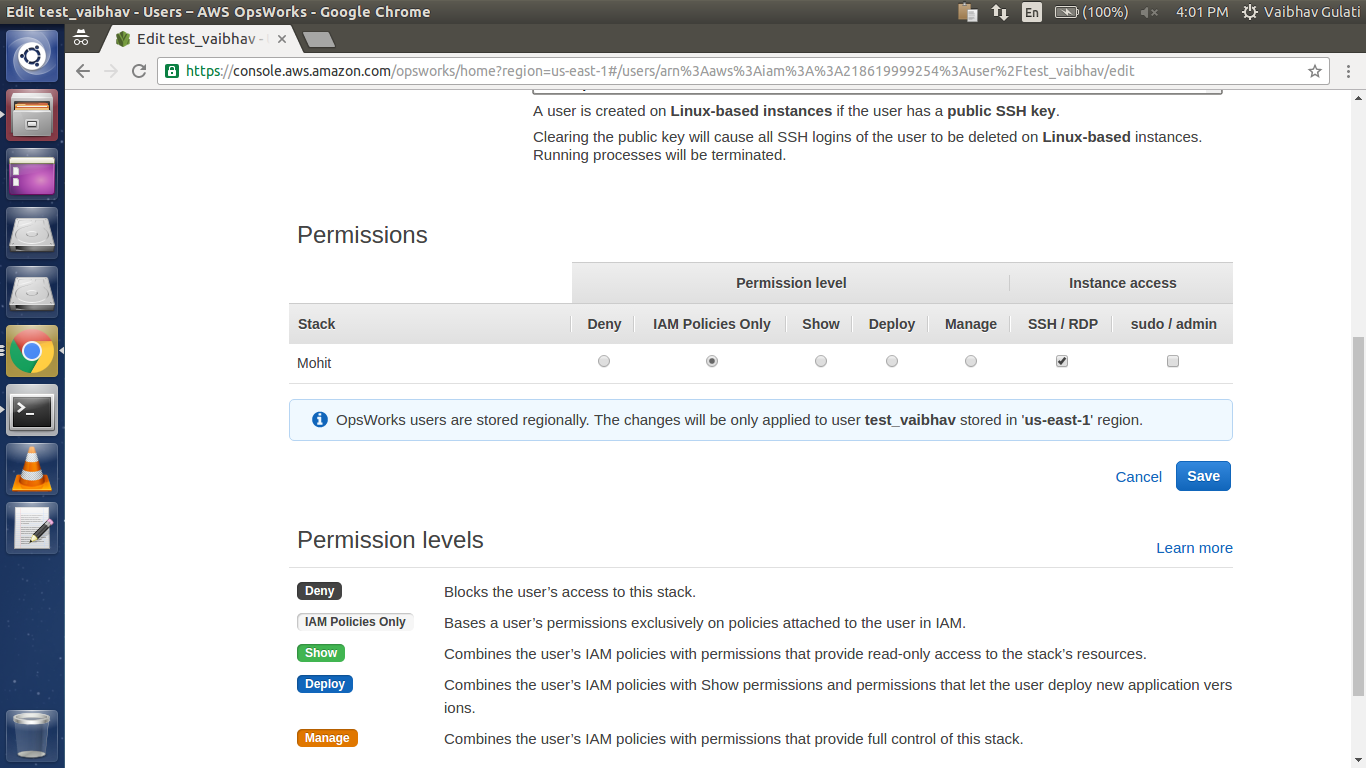
The SSH permissions are specific to the Stack(s).
Set Permission level to “IAM Policies Only” and Instance access to “SSH/RDP”.
Permission level is the amount of access a user has on the stack.
Deny : It means that to user cannot perform any perform on the stack.
IAM Policies Only : The user’s access on the stack is limited to the IAM policy applied on it.
Show : The user has only view access on the stack.
Deploy : The user has access to deploy app and view the stack.
Manage : The user has access to stack “Permissions” section, deploying apps and various management actions like modifying layers/instances, adding or removing resources.
Instance access
SSH/RDP : Giving SSH/RDP access to user corresponding to linux/windows.
sudo/admin : Giving sudo/admin privileges to user respective to linux/windows.
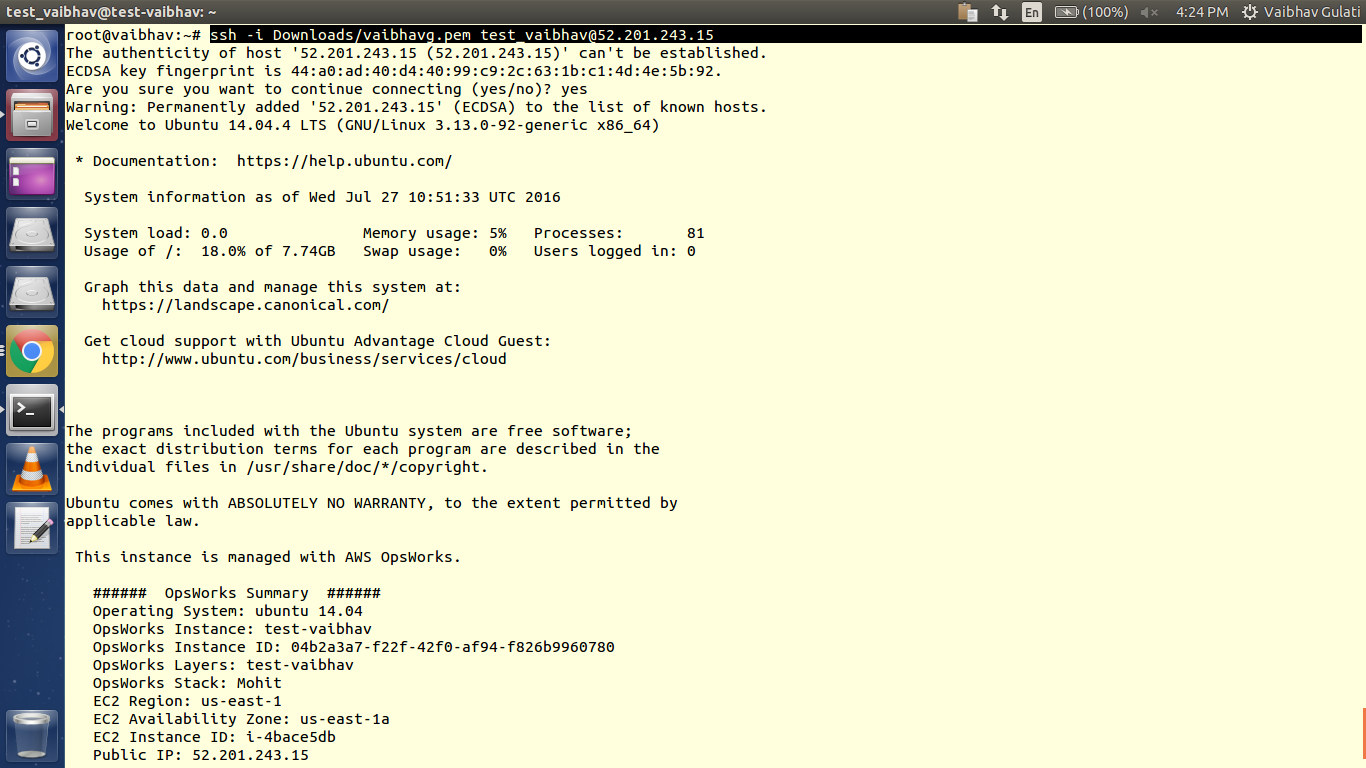
Now try to ssh into the server :
ssh -i ~/.ssh/[your-keyfile] test_vaibhav@INSTANCE-DNS
and make sure that ssh port is open for your ip in the security group in AWS Console.
Tip/Trick: If you lose .pem file of your EC2 Instance, you can register your Instance with Opsworks, add a new user to it and later modify the keys of your previous user.
Hope after reading this blog you’ll be comfortable in playing around with “Permissions” option in the Opsworks console !



