EC2 Image Builder in Action: From AMI Creation to Cross-Account Sharing
Introduction
EC2 Image Builder is an AWS service that automates creating, updating, and deploying your Amazon Machine Images (AMIs).
EC2 Image Builder creates a pipeline for Linux or Windows Server images for use with Amazon EC2. The pipeline manages all stages, including image creation, maintenance, validation, sharing, and deployment.
Image Builder is free to use, except for the cost of the AWS resources needed to create, store, and share the images.
Refer to this blog to know more about EC2 Image Builder – Packer Alternative: Migrating to AWS EC2 Image Builder for Automated AMI Pipelines
Scenarios in Action
1. Using EC2 Image builder service and its sub-resources to build an EC2 Image Pipeline to automate AMI creation and AMI sharing to the destination AWS Account via CFN template only.
Here, we’ll install a CloudWatch Agent and the Testing Component Script, which will validate if the CW agent is running or not. If the CloudWatch agent status is not in the running stage, break the AMI build process.
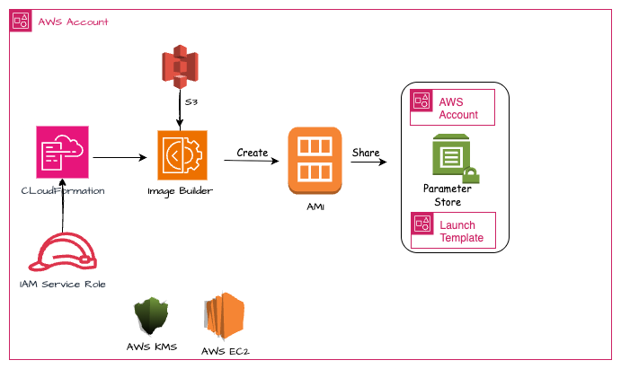
EC2 Image Builder
Prerequisites before deploying the EC2 Image Builder CFN Stack
IAM Role – Permission of the S3 bucket and SNS Notification. Here, Image Builder download scripts from the S3 bucket and sends a notification to SNS.
VPC and subnet (private only) – EC2 launch via Image builder privately, and access to the internet is required to download the packages.
KMS key – To encrypt the AWS EBS volume, the best practice is to follow.
Note – The above resources mentioned in the prerequisite are not part of the CFN template. They are passed as a parameter in the template.
Deploy the CFN template to create resources
CFN Template GitHub URL – Click Here
Component Scripts – Click Here
Once the CFN template is deployed, the EC2 Image Pipeline is created, and it clubs all the resources within the pipeline to build in CI/CD pipeline. It builds, validates and on successful share the AMI to other accounts.
Stack Output –

CFN Stack Output
EC2 Image Pipeline –

EC2 Image Pipeline
Distribution of the AMI –

AMI Distribution

AMI Distribution
It’s important to do unit testing on our end to validate if the agents are up and running. Launch an EC2 Instance via a custom AMI and check the CW agent status using the command below.
Command: sudo systemctl status amazon-cloudwatch-agent

CloudWatch Agent
2. To validate the package’s installation via the EC2 image builder itself using a custom component script
- Here we are configuring and installing the CloudWatch agent, but before creating an AMI, there must be a testing process to validate if the agent is running or not.
- If the agent status is not running, break the build pipeline because we don’t want to share a broken AMI with a misconfigured agent setup.
- In Scenario 01, it successfully configures the agent. Let’s try to break the build process on failure.
- In the Script InstallLinuxComponent.sh script, after the installation, let’s STOP the CloudWatch agent.
- Add a command at the end of a script – sudo systemctl stop amazon-cloudwatch-agent
- Upload the updated script to the S3 bucket path.
- Execute the EC2 Image Pipeline

Build Workflow
Here is the flow: when the validation script checks for the CloudWatch agent service status, it’s not running, which returns the exit code. The exit code can be any number except 0, due to which the Build workflow failed because the agent is not UP and Running and breaks the build process.

Workflow ID logs
3. SNS Integration in EC2 Image Builder to receive pass/success status of the AMI.
Once AMI is created, Image Pipeline sends a huge Raw JSON, which can be filtered via a lambda, and the lambda can send the output to a new SNS as an input to receive a pass/fail status.
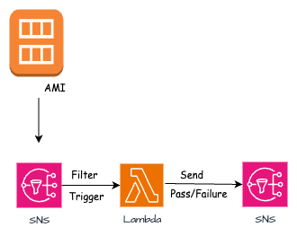
AMI Notification
Once the AMI is in an available or fail state, it triggers the SNS configured in the Infrastructure configurations in EC2 Image builder via a CFN template.
Configure AWS Lambda and a custom Python script to filter the Raw JSON sent by the pipeline to deliver filtered and formatted key: values to the stakeholders/team.
Key Notes
- The Pipeline fetches the latest AMI, always using the x.x.x semantic versioning. It’ll always pick the latest Major, Minor, and Patch version whenever the EC2 image pipeline gets triggered.
- It requires no other AWS service dependency to trigger the pipeline. It has a cron expression scheduler built in.
- It can share AMIs across accounts, SSM parameters, update the launch template and so on.
- The components in the recipe are executed in the sequence order in which they are defined.
Wrapping Up
While learning and implementing EC2 Image Builder, I realised that we can achieve much more with this service than I initially thought. Don’t stop here—explore new scenarios and possibilities with it.



