Basics of IPTables
Linux is the most-used open source operating system. Managing network traffic is one of the toughest jobs to deal with. For this, we must configure the firewall in such a way that it meets the system and users requirements without leaving the system vulnerable. The default firewall in most of the Linux distributions is IPTables.
IPTables is used to manage packet filtering, DNAT(Destination Network Address Translation), SNAT(Source Network Address Translation) rules. IPTables comes with all Linux distributions.
To update/install it, just retrieve the IPTables package:
[js]
sudo apt-get install iptables
[/js]
IPTables might contain multiple tables and tables might contain multiple chains and chains contain multiple rules where rules are defined for the incoming and outgoing packets.
Therefore structure is IPTables -> Tables -> Chains -> Rules.
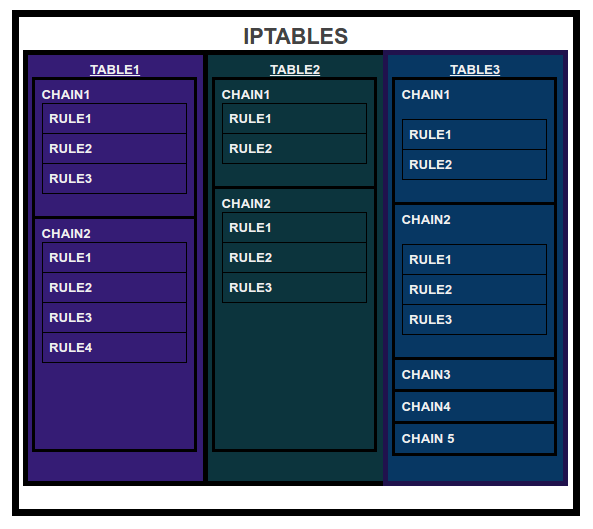
IPTables has the following 5 built-in tables:
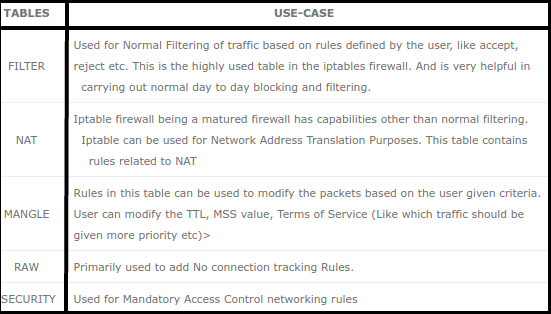
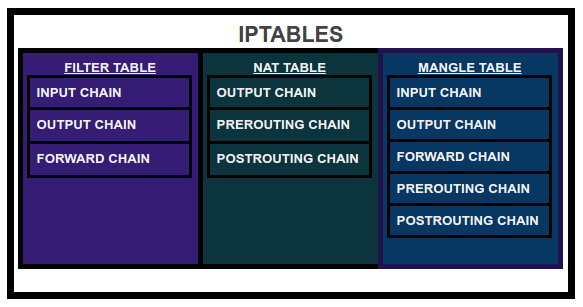
Mostly we play around with FILTER, NAT and MANGLE tables. There are five built-in chains in which we can place our firewall policy rules:
- INPUT CHAIN: It is used for rules which are applicable to the traffic/packets coming towards the server.
- OUTPUT CHAIN: It is used for rules which need to be applied on outgoing traffic/packets from our server.
- FORWARD CHAIN: It is used for adding rules related to forwarding an IP packet.
- PRE-ROUTING CHAIN: It is used to add rules which define actions that need to be taken before a routing decision is made by the kernel.
- POST-ROUTING CHAIN: It is used for adding rules which will define actions that need to be taken after a routing decision which is taken by the kernel.
Now, let’s see some useful commands:
- To see all the rules, we can type:
[js]
sudo iptables -t <table-name> -L
[/js]
where,
-t is used to specify the table name,
-v for verbose and
-L for listing the chains and rules
Ex:
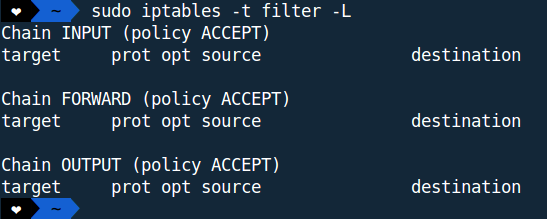
Here, we have listed the chains and rules defined inside filter table.
If we haven’t played with iptables before then by default, no rules are present in any of the built-in tables.
- To add a rule inside a chain of a table, we can type:
[js]
sudo iptables -t <table-name> -A <chain-name> -d <destination-address> -p <protocol> -j <action>
[/js]
where,
-A to append one or more rules to the end of the selected chain
-d for specifying a destination
-p protocol of the rule or of the packet to check
-j specifies the target of the rule; i.e., what to do if the packet matches it,
Ex:
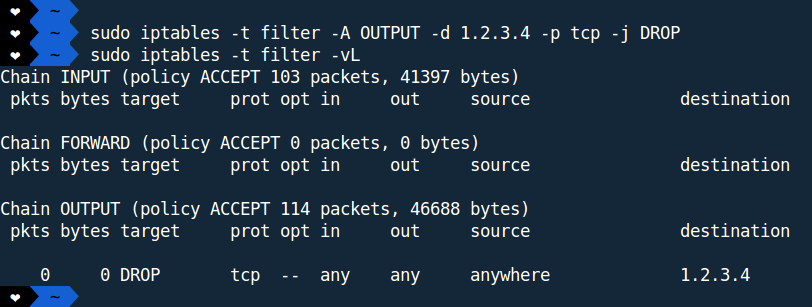
We have created a rule inside OUTPUT chain which says, drop any TCP packets going to 1.2.3.4.
- To flush all the rules:
[js]
sudo iptables -t <table-name> -F
[/js]
where,
-F to flush the selected table rules
Ex:
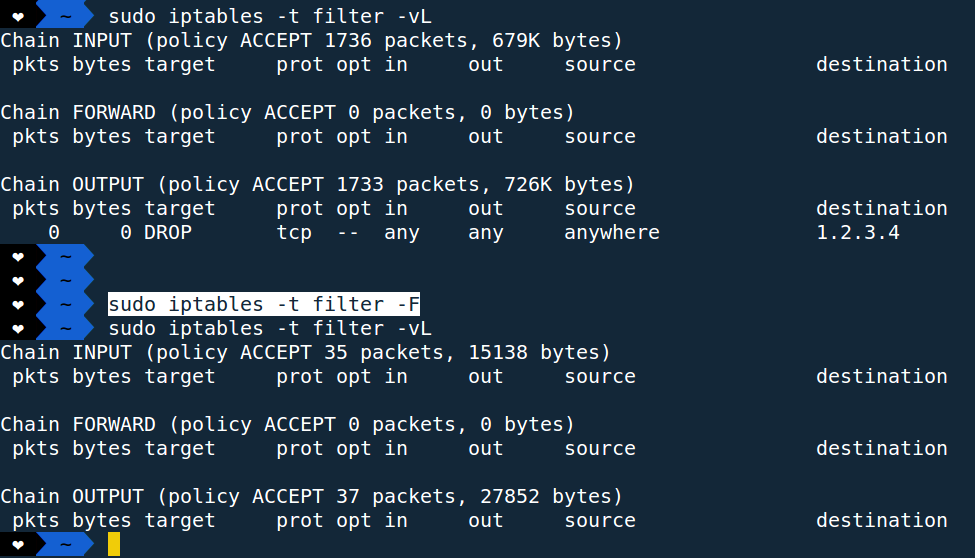
As we can see all the rules from filter table are deleted/flushed.
- To create a new chain:
[js]
sudo iptables -t <table-name> -N <chain-name>
[/js]
where,
-N for adding new chain to a particular table
Ex:
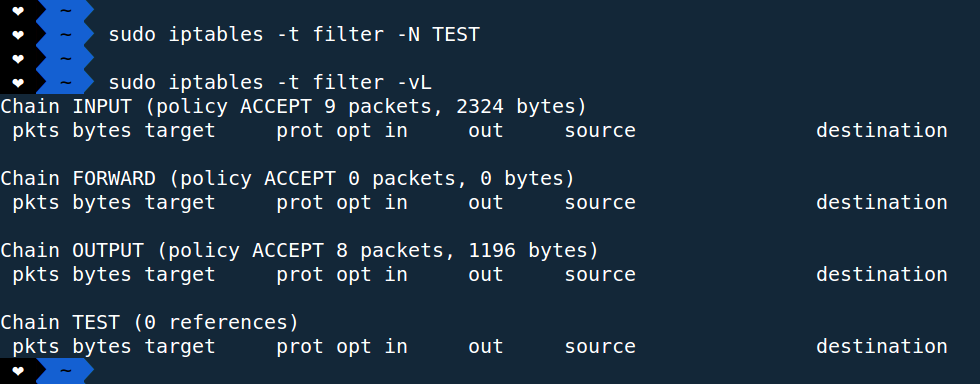
A new chain name “TEST” has been created by the above command shown in the figure.
- To delete a chain:
[js]
sudo iptables -t <table-name> -X <chain-name>
[/js]
where,
-X is for deleting the optional user-defined chain specified
Ex:
Chain name “TEST” has been deleted from filter table.
Simple Use Case :
Suppose our server has been hit by DoS attacks. In order to protect our server from common DoS (or small-scale DDoS) attacks, we can use IPTables.
Let’s block IP address with the help of rules defined inside the INPUT chain of filter table:
- Setting the rule:
[js]
sudo iptables -t filter -A INPUT -s x.x.x.x -p tcp -j DROP
[/js]The above command will block x.x.x.x from entering into the server. DROP action will drop all the TCP packets coming from x.x.x.x IP-address.:
- We can delete the rule in one of the two ways:
- Deleting by line number:
[js]
sudo iptables -D INPUT 1
[/js] - Deleting the particular rule:
[js]
sudo iptables -D INPUT -s x.x.x.x -p tcp -j DROP
[/js]
- Deleting by line number:
For more detailed information, we can refer the manual page of IPTables.




Thanks for sharing your blog. Its clear and easy to start with for any new engineer.
Dear anup , very nice explained. Very easy way . the confusion about iptables is solved .thank u boss .i m grateful to you .