Deploying Egress Gateway in Kubernetes : Istio
Introduction
Nowadays, In microservices architectures we have started using service mesh like Istio for managing and securing the traffic flow inside Kubernetes cluster ,In Istio service mesh we use Ingress and Egress gateways for routing the inbound and outbound traffic. In this blog we will be looking on how we can use Egress gateway to route external traffic leaving the mesh.
Prerequisites
- Basic understanding of Kubernetes and Its networking.
- Kubernetes cluster has already been setup with Istio installed.
- Istioctl should be installed.
You can use below command to confirm that istio is installed in you Kubernetes cluster. The istio components will be shown like istiod.
kubectl get pods -n istio-system
Step 1: Allowing the sidecar injection
So, we need to add the labels to the namespace so that the sidecar can be able to inject. You can use below command for this –
kubectl label namespace egress istio-injection=enabled
kubectl label namespace default istio-injection=enabled
Step 2: Deploying a sample application.
kubectl apply -f https://raw.githubusercontent.com/istio/istio/refs/heads/master/samples/sleep/sleep.yaml
we will be using this sample application to test the traffic if its going thorough the egress gateway.
Step 3: Updating mesh configuration
Istio by default allow unrestricted access traffic to external services lets restrict by updating the “outboundTrafficPolicy“ to “REGISTRY_ONLY“
kubectl -n istio-system get configmap
kubectl -n istio-system edit configmap istio
It will look like below, you need to update the “outboundTrafficPolicy“ like below –

configMap
Restart the isito control plan so that the changes come into effect. It will block all the egress traffic except the external services defined in ServiceEntry would be allowed.
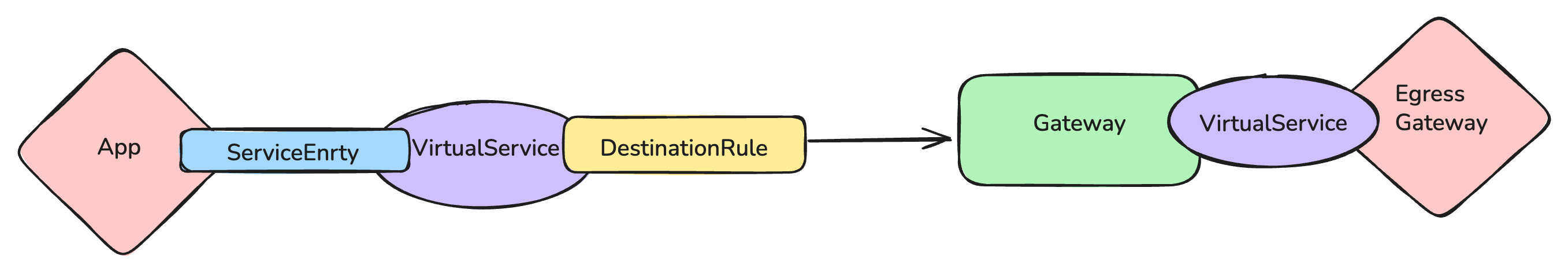
Traffic Flow
Step 4: Creating Service Entry and ServiceAccount
So, For enabling the egress traffic we need to define service entry for those hosts.

ServiceEntry
Note: “exportTo” Defines the namespace. Right now, its set to exportTo: [“.” ] which means its applicable to current namespace. You can use “*” istead of “.” to be applicable to all namespace.
Step 5: Deploying Egress Gateway Deployment

Deployment
Step 6 : Deploying Service

Service
Step 7: Deploying the Gateway
Let’s deploy the egress gateway using below yaml as it would be the point of exit from the mesh.

Gateway
Step 8 : Deploying DestinationRule
Let’s create a DestinationRule as it would be defining the destination host and subset name that would be referenced by virtual service.

DestinationRule
Step 9 : Deploying NetworkPolicy
Below network policy would make sure that our Egress gateway can receive traffic from Istio control plane and Sample App.

NetworkPolicy
Step 10 : Deploying VirtualService
So, this virtual service will redirect the traffic originating from the mesh (sidecar-proxy) port 80 or 443 to Egress gateway and then to external host.

VirtualService
Lets test the traffic now, to make sure it’s going through our Egress gateway –
kubectl exec -it deployment sleep -c sleep -- curl -I https://edition.cnn.com
Then we can look into the logs to confirm if the traffic is going through our egress gateway.
kubectl logs <Pod-name> -c istio-proxy
Below is the example of how logs will look like-
[2025-06-25T23:32:42.892Z] "- - -" 0 - - - "-" 304 6087 101 - "-" "-" "-" "-" "52.7.212.xx:xxx" outbound|443||edition.cnn.co 10.23.43.x:xxxxx 10.23.43.x:xxx 10.23.20.xx:xxxxx edition.cnn.com -
Conclusion
Now, you have configured a secure way to send your outbound traffic from the Kubernetes cluster using Istio’s Egress Gateway. It also adds a layer of security which also aligns the best practices that should be followed in mesh architectures for outbound traffic.
You can also refer the Official Documentation of Istio Egress Gateway – https://istio.io/latest/docs/tasks/traffic-management/egress/egress-gateway

