Security measures for Angular Application
Angular is a popular JavaScript framework for building SPA (Single page applications). It is known for its strong performance, flexibility, and ease of use. However, like any other web application, Angular applications are also vulnerable to security attacks.
In this blog post, we will discuss some best practices for securing your Angular applications. We will cover topics such as:
- Preventing cross-site scripting (XSS) attacks
- Using a content security policy (CSP)
- Blocking HTTP-related vulnerabilities
- Avoiding risky Angular APIs
- Not customizing Angular files
- Staying up-to-date with the latest Angular library
- Be careful about what data you expose
- Using a Code review Tool
- Training your developers
By following these best practices, you can help to protect your Angular applications from security vulnerabilities.
Preventing Cross-Site Scripting (XSS) Attacks
XSS attacks are a type of attack where an attacker injects malicious code into a web page that is then executed by the victim’s browser.Cybercriminals can use this technique to compromise sensitive data, such as cookies or session tokens.
To prevent XSS attacks, you should always sanitize user input before it is displayed on the page. Angular provides a number of built-in sanitization functions that you can use.
For example, to sanitize user input for display in an HTML attribute, you can use the DomSanitizer service:
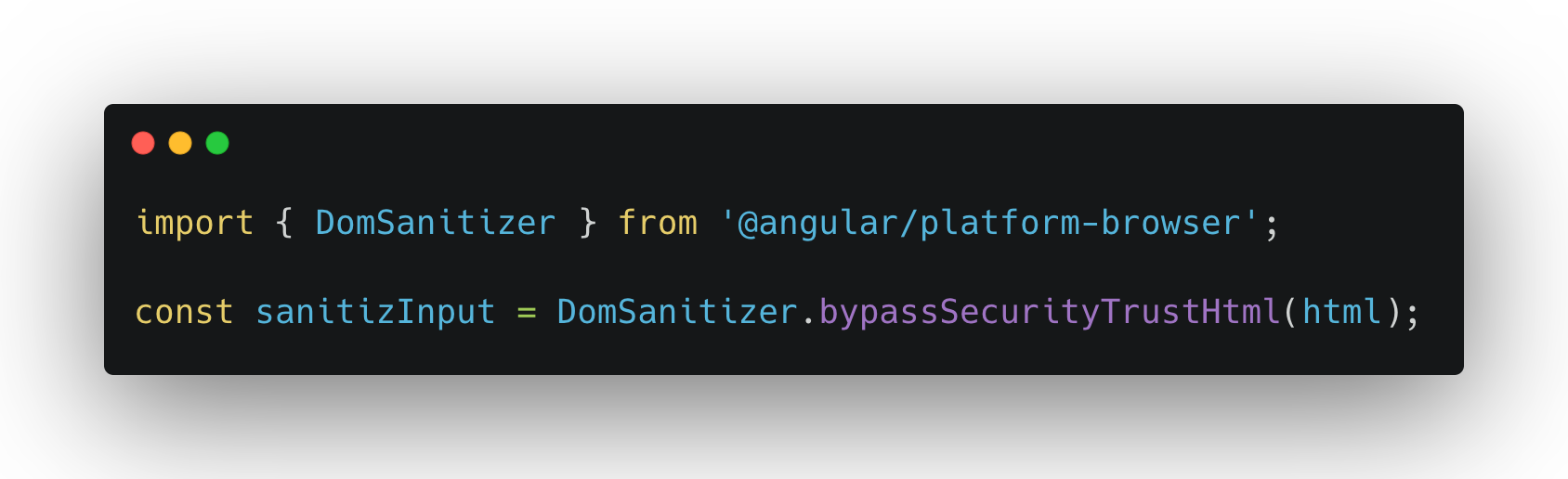
Different techniques are used to ensure that a value is reliable, depending on its type.
These methods are described below:
-
bypassSecurityTrustScript
-
bypassSecurityTrustStyle
-
bypassSecurityTrustUrl
Using a content security policy (CSP)
A CSP can help to prevent attackers from injecting malicious code into your application. To use a CSP, you need to add the following line to your index.html file:
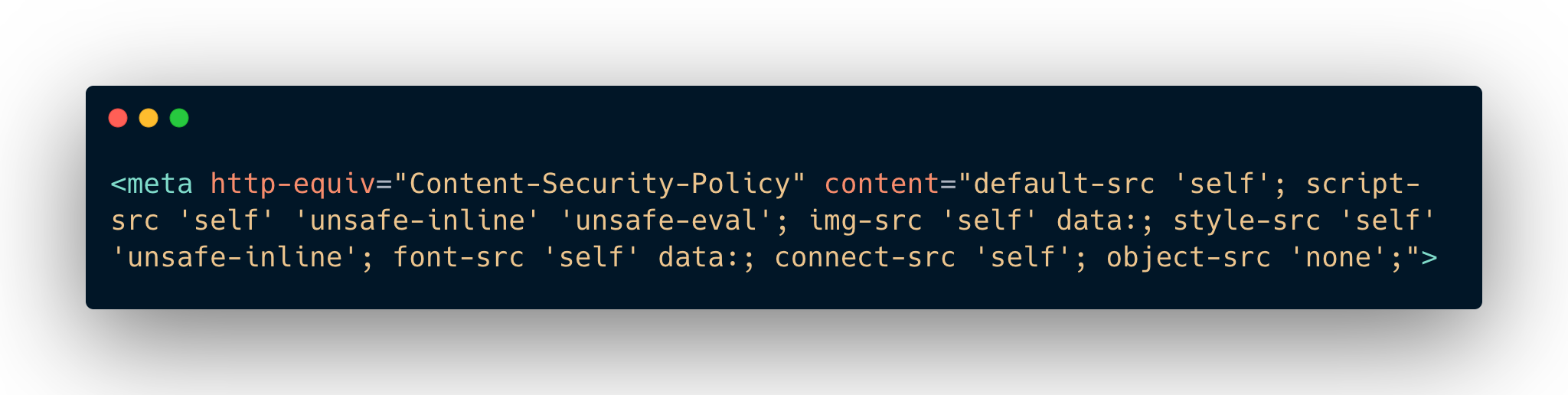
This CSP policy will allow your application to load resources from your own domain, as well as from a few trusted third-party domains. It will also prevent attackers from injecting malicious code into your application.
Blocking HTTP-Related Vulnerabilities
HTTP-related vulnerabilities can be exploited by attackers to steal data or take control of your application. To protect your application, you should use a web application firewall (WAF) to block common attack vectors. You should also use HTTPS to encrypt all traffic between your application and the user’s
Avoiding Risky Angular APIs
Some Angular APIs are more risky than others. For example, the ElementRef API allows you to directly access the DOM, which can make your application more vulnerable to XSS attacks. You should avoid using these APIs unless absolutely necessary.
For example, instead of using the ElementRef API to directly access the DOM, you can use the DomSanitizer service to sanitize user input before it is displayed on the page.
Not Customizing Angular Files
Customizing Angular files can introduce security vulnerabilities. If you need to customize Angular files, you should use a code obfuscator to make it more difficult for attackers to reverse engineer your code.
For example, you can use the AngularJS Obfuscator to obfuscate AngularJS code.
Staying Updated with the Latest Angular Library
Angular is constantly being updated with new security features. To stay up-to-date with the latest security features, you should always use the latest version of Angular.
You can check the Angular release notes to see what security features have been added in the latest version.
By following these best practices, you can help to protect your Angular applications from security vulnerabilities.
Be careful about what data you expose
Only expose the data that is necessary for your application to function. Do not expose sensitive data, such as passwords or credit card numbers. For example, if your application does not need to display user passwords, then you should not expose them in the HTML markup.
Using a code review tool
A code review tool can help to identify security vulnerabilities in your code. There are a number of commercial and open source code review tools available. (TSLint, Sonar, Codelyzer)
Training your developers
Your developers should be trained in security best practices. This will help them to avoid making mistakes that could lead to security vulnerabilities. There are a number of resources available to help you train your developers, such as the OWASP Foundation’s Security Awareness Training.
Conclusion
Angular is an awesome tool for constructing web apps with advanced capabilities. However, like any other web application, Angular applications are also vulnerable to security attacks. By following the best practices outlined in this blog post, you can help to protect your Angular applications from security vulnerabilities.
Explore our blogs for an in-depth understanding of various trending topics.



