Security Testing
You won’t ever want to implement software that frustrates your customers and has issues every two weeks. Prior to deploying software at the client’s location, security testing is an essential step.

What is Security Testing?
Software testing, which is done to find a software application’s flaws and vulnerabilities, includes security testing as a crucial component. The major goals are to find software vulnerabilities and determine if data and other resources are safe from outside intruders. It is a method of determining whether or not confidential information is kept that way.
Security testing has become even more crucial because of the worldwide increase in e-commerce websites. After the program has been created and installed, testing is completed. Network security testing is advised to find all the serious flaws.
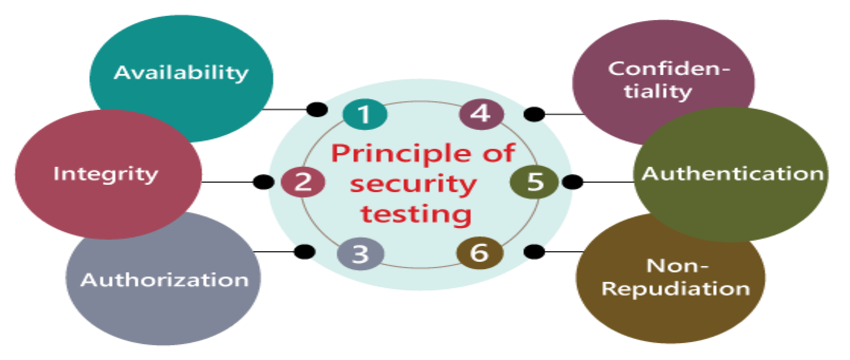
Seven attributes the security testing needs to follow are:
- Authorization
- Authentication
- Confidentiality
- Integrity
- Availability
- Resilience
- Non-repudiation
Why Security Testing?
In current scenarios, security testing is mandatory to identify and fix web application security vulnerabilities and to avoid:
-Losing customer trust.
-Disrupting online revenue generation/collection funds.
-Website downtime, loss of time and money for damage recovery (reinstalling services, restoring backups, etc.)
-The cost of protecting your web application from future attacks.
-The associated legal implications and fees for lax security measures.
Security Testing “Terminology”-
- Penetration Testing:
This type of test uses various malicious techniques to assess systems and networks. The purpose of these tests is to protect sensitive data from users who do not have access to the system, like hackers. It takes place after careful registration, consideration, and planning.
Penetration testing is divided into two types: black-box testing and white-box testing. White box testing gives testers access to all important information, such as code, IP addresses, infrastructure diagrams, etc. Black box testing does not allow testers access to critical information. Black box testing tends to be the most accurate test because the tester has no access to the information and simulates testing as a hacker.
- Cracking Password:
The password crack test tests your system to identify weak passwords. Password cracking tools are used to test this attribute. The end result is that users are using strong passwords.
- Vulnerability:
This is to identify the weakest attributes in the system, which might lend easy paths for the malicious software to be attached by unauthorized users. Vulnerability can occur due to bugs in software, inaccurate software testing, or the presence of malicious code. This phase requires fixes and patches to prevent compromised integrity by malware or hackers.
- URL manipulation:
A URL manipulation attack is when someone edits the URL text in the browser’s location bar to probe a website. URLs are easily changed and often follow a pattern, which makes them inviting targets. By manipulating certain parts of a URL, a hacker can get a web server to deliver webpages he is not supposed to have access.
- SQL Injection:
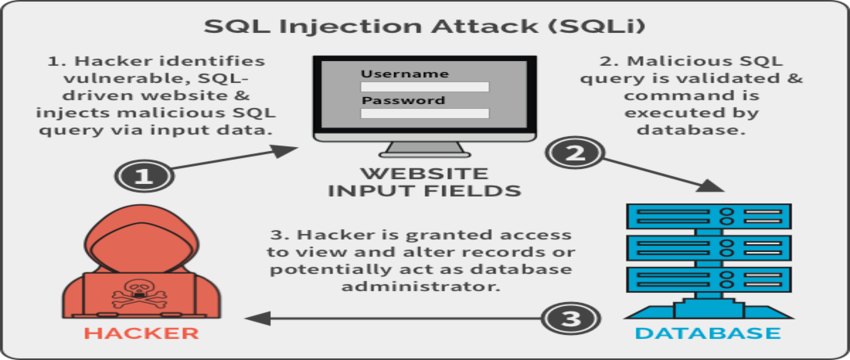
One of the other common ways picked by hackers to steal vital information from the web, is SQL Injection testing ensures all the databases are safe and protected. It is a type of testing that takes advantage of the loopholes that make the hackers easily pass into the system by passing all possible SQL queries to hack it.
They try to query the database using the SQL Injection statements to pull information and crash the system. Even the errors displayed while crashing the system will give the hackers a generous amount of important data.
So, SQL Injection testing is purposed to take care of the input fields like comments, text boxes, etc.
- Denial of Service:
A denial-of-service (DoS) attack is an explicit attempt to make a machine or network resource unavailable to its legitimate users. Applications can also be attacked in ways that render the application, and sometimes the entire machine, unusable.
Security Testing Approach:
We can take the following approach while preparing and planning for Security testing:
- Security Architecture Study: The first step is to understand the business requirements, security goals, and objectives in terms of the organization’s security compliance. The test planning should consider all security factors, like the organization might have planned to achieve.
- Test Planning: Based on identified Threats, Vulnerabilities, and Security Risks, prepare a test plan to address these issues.
- Traceability Matrix Preparation: For each identified Threat, Vulnerabilities, and Security Risk, prepare a Traceability Matrix.
- Security Testing Tool identification: All security testing cannot be executed manually, so identify the tool to execute all security test cases faster & more reliably.
- Test Case Preparation: Prepare the Security tests case document.
- Test Case Execution: Perform the Security Test cases execution and retest the defect fixes. Execute the Regression Test cases.
- Reports: Prepare detailed report of Security Testing, which contains Vulnerabilities and Threats contained, detailing risks, still open issues, etc.
Hope for the Best, but Test for the Worst.



