The Crucial Role of Security Testing in Contemporary Software Development
In the present era of hyper-connected digital environments, where technology continuously evolves, security testing has emerged as an indispensable element of software development. With individuals and businesses increasingly relying on software applications for various purposes, the imperative to shield sensitive data and systems from potential threats has never been more pronounced.
Additionally, Application Programming Interfaces (APIs) play a pivotal role in enabling data exchange and functionality across diverse applications. However, alongside the convenience they offer comes a significant responsibility: the imperative to fortify your APIs against potential vulnerabilities.
Exploring Security Testing
Security testing is a methodical process designed to pinpoint weaknesses in software applications and evaluate their susceptibility to potential security risks. The primary aim of security testing is to uncover vulnerabilities in a software’s security controls that could be exploited by malicious actors, compromising the confidentiality, integrity, or availability of data and systems.
Why Security Testing is Indispensable
- Safeguarding Sensitive Data: In an era where personal information, financial data, and intellectual property are digitally stored and processed, security breaches can have severe repercussions. Security testing ensures the confidentiality of such data, guarding against theft or unauthorized access.
- Upholding User Trust: Users expect their data to be handled securely. A data breach can erode trust and harm a company’s reputation. Through security testing, organizations demonstrate their commitment to safeguarding user information.
- Compliance with Legal and Regulatory Requirements: Many industries and regions impose stringent regulations on data security and privacy, such as GDPR in Europe or HIPAA in healthcare. Security testing helps organizations adhere to these legal requirements, sidestepping potential fines and legal entanglements.
- Cost Efficiency: Identifying and rectifying security vulnerabilities early in the development process is more cost-effective than dealing with security incisdents and their aftermath following a breach.
- Ensuring Business Continuity: Security incidents can disrupt operations and result in downtime. Security testing mitigates the likelihood of security-related disruptions, ensuring business continuity.
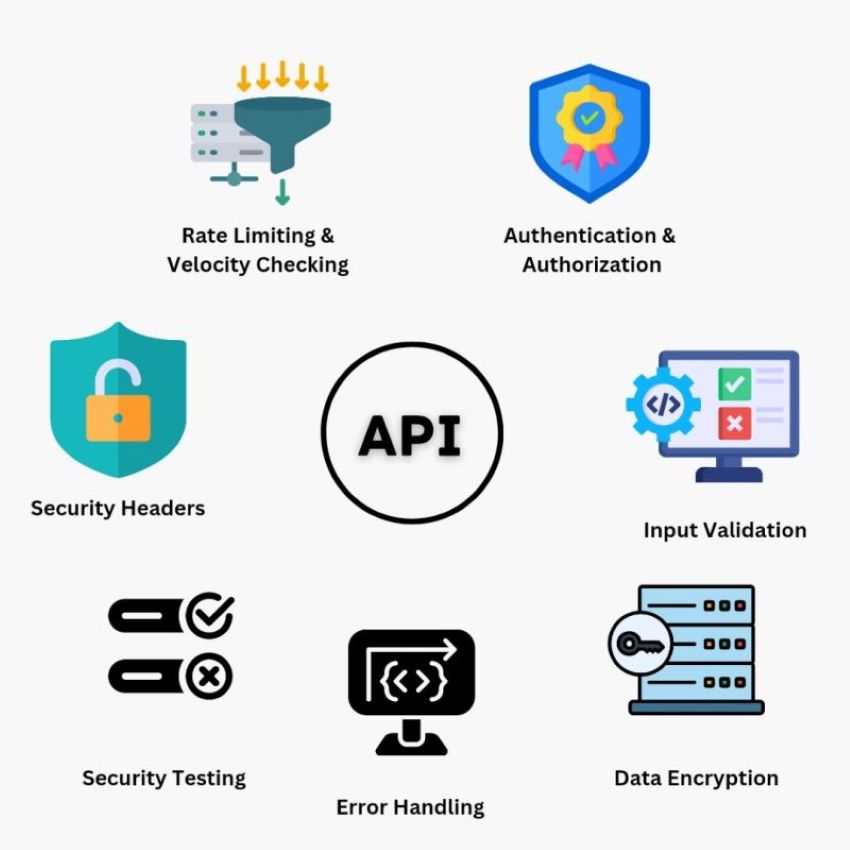
Here are some top API security best practices to protect your digital assets:
- Authentication & Authorization: Implement robust authentication mechanisms like OAuth or API keys to grant access only to authorized users and applications.
- Rate Limiting: Establish rate limits to prevent abuse or overload of your APIs, maintaining performance and preventing DDoS attacks.
- Data Encryption: Utilize TLS/SSL to encrypt data transmitted through APIs, safeguarding it from eavesdropping.
- Input Validation: Sanitize and validate input data to thwart injection attacks like SQL or XSS vulnerabilities.
- Security Headers: Employ security headers like Content Security Policy (CSP) and Cross-Origin Resource Sharing (CORS) to control data access and protect against common web vulnerabilities.
- Error Handling: Implement robust error handling to provide meaningful error messages to clients while preventing information leakage that could assist potential attackers.
- Security Testing: Regularly conduct security assessments, penetration testing, and code reviews to pinpoint and rectify vulnerabilities.
Key Principles of Security Testing
- Comprehensive Coverage: Security testing should encompass all facets of an application, including authentication, authorization, input validation, session management, and data protection.
- Realistic Testing: Test scenarios should closely resemble real-world attack scenarios to unveil vulnerabilities that malicious actors might exploit.
- Continuous Enhancement: Security testing should be an ongoing process, spanning the software development lifecycle from design and development to deployment and maintenance.
- Interdisciplinary Collaboration: Effective resolution of security issues necessitates collaboration between development, operations, and security teams.
Methodologies and Best Practices
- Penetration Testing: Ethical hackers simulate attacks on a system to identify vulnerabilities and assess the system’s resilience to attacks.
- Static Application Security Testing (SAST): SAST analyzes an application’s source code to identify potential security flaws and vulnerabilities.
- Dynamic Application Security Testing (DAST): DAST tests a running application to uncover vulnerabilities that can be exploited in real-time.
- Security Code Reviews: Manual code reviews by experienced security experts can reveal vulnerabilities that automated tools may overlook.
- Security Training: Ensuring that development and testing teams are well-versed in security best practices is essential. Regular security training can prevent security issues from arising.
- Vulnerability Management: Establish a process for tracking and prioritizing identified vulnerabilities, ensuring timely remediation.
In Conclusion
Security testing is an integral component of the software development process, acting as a crucial shield against the ever-evolving landscape of cybersecurity threats. By implementing robust security testing practices and fostering a security-conscious culture, organizations can establish trust with their users, protect sensitive data, and safeguard their digital assets. In today’s interconnected world, the question is not whether to invest in security testing but how to seamlessly integrate it into the development lifecycle for maximum protection.



