IAM Role based access to S3 bucket.
In one of our projects, we came across a requirement where we were required to fetch a file containing important data from S3 in order to use it. Due to Security concerns we were not keen on storing access keys on the EC2 instance. Which basically meant that we could not configure S3 on that very system as configuring S3 would create a configuration file (.s3cfg) with access keys stored on it.
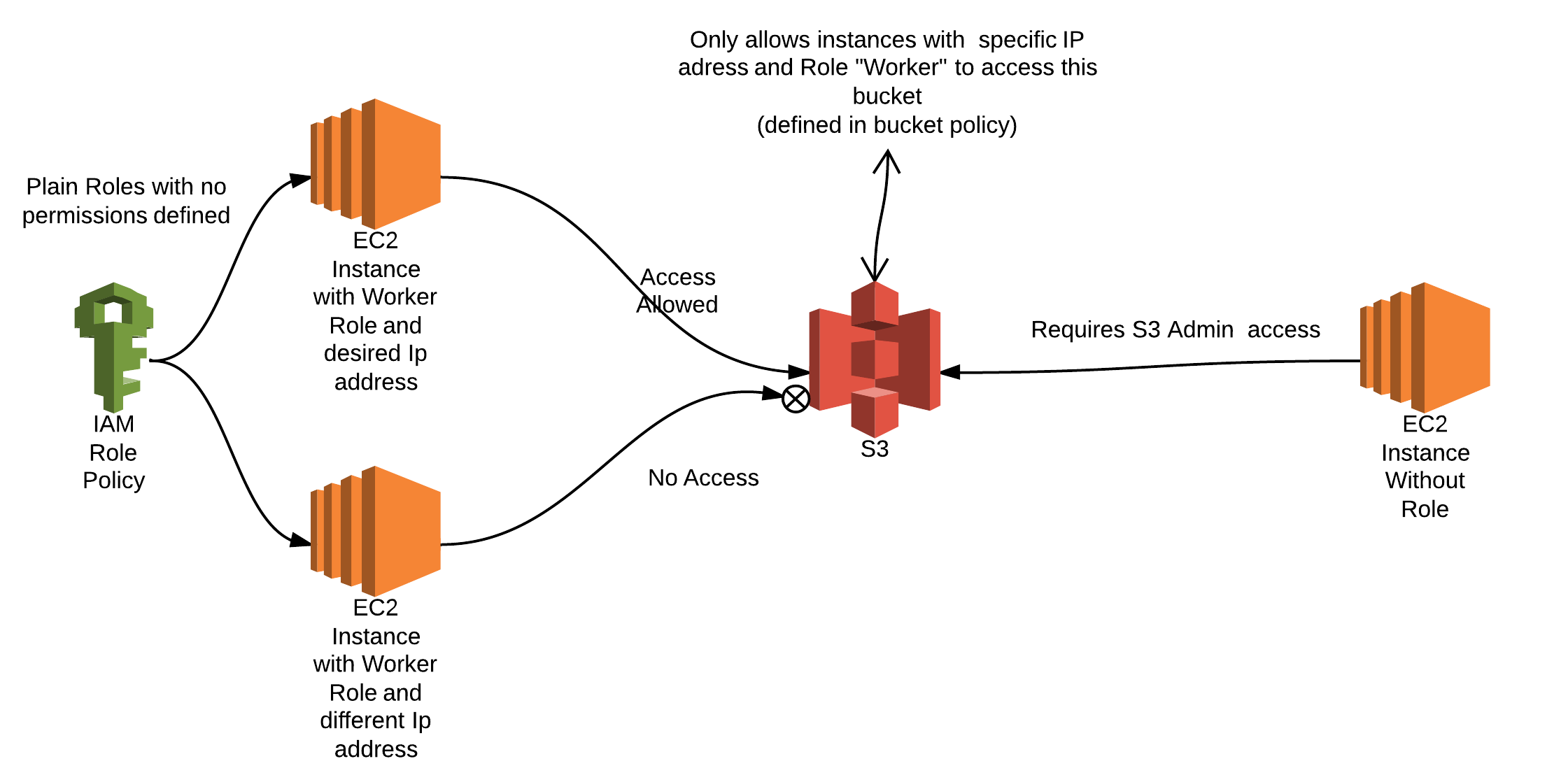
The architecture is described in image below.
To accomplish this we followed the steps mentioned below
- Created an AWS Role named “Worker” which EC2 instances can assume with no specific permission policy.
- Created an EC2 instance with Role “Worker” and Ip address : 54.254.196.37
- Added policy to our bucket “com.intelligrape.rolebasedaccess.test” which only allows EC2 instances with Role “worker” and IP address “54.254.196.37” to access the file named “SIPD”.
A role in AWS IAM defines the permissions for service requests and it is assumed by AWS resources like EC2 Instance. The benefit of using roles was that we didn’t have to configure S3 separately on the instance. S3 in this case used ROLE credentials which are temporary and rotated automatically.
"Version": "2008-10-17",
"Id": "Policy1388257451238",
"Statement": [
{ "Sid": "1232343455",
"Effect": "Allow",
"Principal": { "AWS": "arn:aws:iam::10987654321:role/worker" }, //arn:aws:iam::accountnumber:role/rolename
"Action": "s3:GetObject", // actions allowed, only allowed to fetch object.
"Resource": "arn:aws:s3:::com.intelligrape.rolebasedaccess.test/SIPD", //"arn:aws:s3:::bucketname/file"
"Condition": {
"IpAddress": {"aws:SourceIp": "54.254.196.37/32"} // Ip address to allow access to
}
}
]
}
(Do not forget to remove the comments before putting it to use.)
And its done, with this we were able to limit access to S3 bucket to EC2 instance with specific IP address.
More about IAM Roles can be learned at AWS Documentation Page.




would this work even if the bucket object is set as private?