SSH tunneling with AWS private subnet
It has been a long time while I was working over the project where we required accessing Rabbit MQ dashboard. I know accessing the Rabbit MQ is not the difficult task but my scenario was bit complex.
Scenario: I was supposed to access Rabbit MQ dashboard from AWS Linux machine which is placed in the private subnet of VPC (AWS) with no public IP. At the same time I used to login over Rabbit MQ server using bastion host to do command line changes.
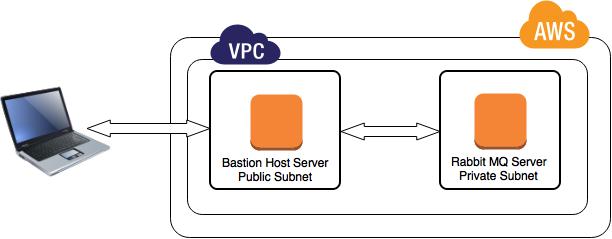
After digging into some of the blogs over the internet, I have decided to go for SSH tunneling to access the dashboard over my local machine.
To do SSH tunneling I am assuming given pointers are taken care
- Necessary ports are open between Bastion host and Rabbit MQ server.
- SSH access between your local machine and bastion host
Here is command
[js]ssh -p 2200 -f -N user@BastionHost -L 27651:RabbitMQServer:15672[/js]
Here is attributes explanation
-p : port number if you are using other than 22.
-F : Requests ssh to go to background just before command execution
-N: Do not execute a remote command. This is useful for just forwarding ports
-L : Specifies that the given port on the local (client) host is to be forwarded to the given host and port on the remote side.
Now, to access Rabbit MQ dashboard, Use http://localhost:2765 in the browser.
Reference:
https://help.ubuntu.com/community/SSH/OpenSSH/PortForwarding




Pingback: SSH Tunneling to AWS VPC private subnet instance | My Learnings
Pingback: Sending Scheduled/delayed messages with RabbitMQ through java client | TO THE NEW Blog