Multi-Account Governance in AWS: Beyond Organizations and SCPs
Multi-Account Governance in AWS: Beyond Organizations and SCPs
Introduction
If you’ve worked with AWS for a while, you already know this story: things usually start with one account. Life is simple. Then teams grow, projects multiply, compliance knocks at the door—and suddenly you’re staring at dozens (or even hundreds) of AWS accounts.
That’s when governance gets tricky. AWS Organizations and Service Control Policies (SCPs) are often the first tools we lean on. They’re solid, but at scale, they’re not enough. In this blog, let’s talk about why, and what the next generation of governance in AWS looks like.
Why Multi-Account Is the Default for Enterprises
There’s a reason companies move beyond a single AWS account pretty quickly:
- Separate environments – nobody wants a developer experiment to take down production.
- Blast radius control – a mistake in one account doesn’t take down the whole company.
- Compliance and regulation – sometimes law requires separate accounts for different business units or regions.
- Billing transparency – easier to track costs per project or department.
It’s the right strategy, but it comes with headaches: identity sprawl, inconsistent policies, and the ongoing challenge of maintaining compliance.
Where Organizations and SCPs Fall Short
Don’t get me wrong—Organizations + SCPs are essential. They centralize billing, group accounts, and apply guardrails, such as “no one can create resources outside approved regions.”
But if you’ve ever tried managing SCPs for 50+ accounts, you’ll know:
- The number of policies quickly balloons, and exceptions are a nightmare.
- SCPs are static. They stop bad behavior, but they don’t enforce best practices like tagging or encryption.
- They can’t adapt when business or compliance requirements shift.
- In short, SCPs are a good starting point. But for real enterprise governance, you’ll need more in the toolbox.
The New Ways of Governing at Scale
1. AWS Control Tower & Landing Zones
Think of Control Tower as AWS’s “starter kit” for governance. It comes with pre-set guardrails, central logging, and an Account Factory for spinning up new accounts consistently.
- Pro: Great if you’re starting fresh.
- Con: Retrofitting it into an already messy multi-account setup? Painful.
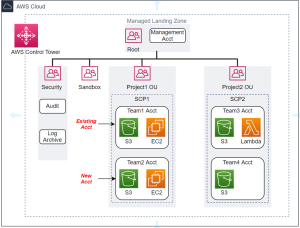
control
2. Policy as Code (PaC)
Instead of writing policies in a console and hoping people follow them, treat policies like application code.
- AWS Config rules to continuously check compliance.
- CloudFormation Guard / Terraform Sentinel to block bad IaC before it ever hits AWS.
- OPA (Open Policy Agent) if you’re running multi-cloud and want one standard.
The nice thing here: policies become version-controlled, testable, and enforceable early in the pipeline.
3. Event-Driven Governance
Static checks are good, but what if you could auto-correct problems in real time?
Example: Someone spins up an unencrypted S3 bucket. EventBridge notices, triggers a Lambda, and bam—the bucket gets encrypted automatically. No waiting for audits, no security team chasing people down.
4. Centralized Identity
Managing IAM across 100 accounts is… let’s just say, not fun. Enterprises are now leaning on:
- AWS IAM Identity Center (formerly SSO).
- Integration with IdPs like Okta or Azure AD.
- Role-based access mapped to jobs, not individuals.
This keeps access clean and auditable, instead of a jungle of IAM users and roles.
Where Governance is Heading
We’re moving from guardrails that just say “no” → to systems that guide, fix, and even predict. Some trends worth watching:
- AI-assisted governance – imagine AWS suggesting policies based on your risk profile.
- Self-healing guardrails – violations not just flagged, but auto-fixed.
- Cross-cloud standards – one set of rules that work across AWS, Azure, GCP.
- Data-aware policies – governance that adapts depending on whether data is sensitive, regulated, or public.
A Few Hard-Earned Best Practices
- Set up a Landing Zone early. Retrofitting later is a nightmare.
- Standardize tagging and billing. It pays off when finance comes knocking.
- Shift governance left. Catch issues in CI/CD, not in production.
- Test your guardrails. Even chaos-engineering them to see if they hold.
- Don’t strangle innovation. The best governance enables speed, not blocks it.
Conclusion
Multi-account setups are the reality for any serious AWS adoption. Organizations and SCPs are the foundation, but they won’t take you all the way.
The future of governance is automated, policy-driven, event-based, and increasingly intelligent. Enterprises that embrace this shift will move faster, stay compliant, and sleep better knowing guardrails are always on.



