An Introduction to Palo Alto VM-Series Next-Generation Firewall in the AWS Cloud
Introduction
As more organizations move their workloads to the cloud, traditional security models are no longer enough. Modern cloud environments need security that can keep up with changing infrastructure and workloads.
The Palo Alto Networks VM-Series Next-Generation Firewall (NGFW) stands out by bringing enterprise-level security controls to virtualized and cloud-native environments.
What Is Palo Alto VM-Series?
The VM-Series is a virtual form factor of Palo Alto Networks’ industry-leading next-generation firewall. Unlike traditional firewalls that rely only on ports and IP addresses, VM-Series provides application-aware, user-aware, and content-aware security—even in fully dynamic cloud environments.
It runs the same PAN-OS software as Palo Alto’s physical appliances, ensuring feature parity across on-premises, hybrid, and multi-cloud deployments.
Hybrid Connectivity & Traffic Flow Using VM-Series
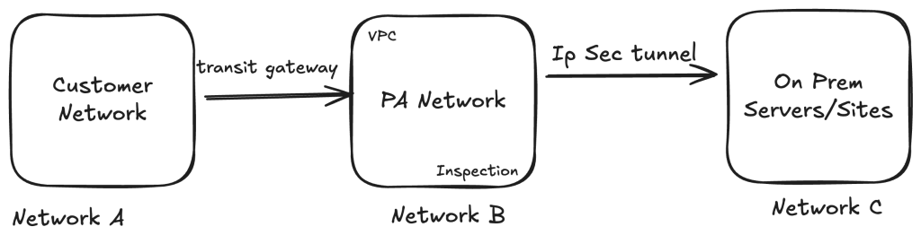
In a typical hybrid architecture, Network A communicates with an AWS VPC (Network B) through an AWS Transit Gateway, and from there, traffic is routed further to the on-premises environment (Network C).
In this design, the Palo Alto Networks VM-Series Next-Generation Firewall is deployed within AWS VPC Network B and acts as a centralized security inspection point. All north-south and east-west traffic passing between AWS and on-premises networks is inspected and secured by the VM-Series firewall before being forwarded to the respective remote or on-prem Palo Alto firewalls.
The Palo Alto VM-Series can be deployed on an AWS EC2 instance and used to establish a site-to-site VPN between the AWS VPC and on-premises networks. This enables secure, encrypted communication while maintaining consistent security policies across cloud and on-prem environments.
This architecture is especially useful for organizations operating hybrid or multi-site environments, as it ensures centralized visibility, policy enforcement, and secure connectivity—without compromising cloud scalability or performance.
Palo Alto
Few factors why it’s considered an enterprise choice
- Application-Level Visibility (App-ID) helps control where traffic is coming from and exactly what the traffic is. This is essential to secure modern cloud and hybrid environments.
- Advanced Threat Prevention—built-in capabilities to prevent malware, ransomware, intrusion attempts, and so on.
- Supports Cloud-Native Integration, Virtual Environments & Automation—It integrates with different cloud environments such as AWS, Azure, and Google Cloud.
- Consistent security configurations—It supports centralized management & visibility of configs via the Panorama centralized management tool for the firewall.
- It provides the same capabilities as physical Palo Alto firewalls and faster deployment.
Palo Alto NextGen firewall (NGFW) High Availability Considerations on AWS
It’s easy and straightforward to deploy a single instance of the Palo Alto Networks VM-Series Next-Generation Firewall (NGFW), but before deploying the NGFW in HA mode, there are a few things to remember.
- Palo Alto can’t span the firewall to Multi AZ due to ENI movement limitations via AWS.
- The classic active/passive VM-series firewall keeps both servers active, meaning utilising AWS resources and resulting in expense.
- Classic active/passive VM-series can be set up in a single AZ, but due to the traditional setup, the AWS AZ’s failover can make the firewall infrastructure go down.
- The highly available NGFW can be deployed with the integration of Panorama (centralized management), AWS ASG, and ALB.
Two ways to make Palo Alto VM-Series Next-Gen Firewall highly available
A. Classic Active/passive VM-Series Next-Generation Firewall (NGFW) NGFW HA setup
On AWS, the VM-Series can be deployed in HA mode within a single AWS Availability Zone. If any failure occurs in the active NGFW (primary), then it can move ENIs to the passive NGFW (secondary). This may cause 60 seconds or more of downtime because of ENI movement.
B. Panorama Firewall Management + AWS ASG + AWS ALB
The Panorama is used to manage firewall configuration centrally. If the AWS load balancer detects failure, it diverts traffic to another server. In the meantime, the auto-scaling group automatically removes the failed firewall and replaces it with a new server with the same and fully configured VM-series firewall.
Note – Panorama itself has the licensing cost.
Challenges to Consider
- It has high licensing costs compared to other basic firewalls.
- The feature-rich VM-series firewall can require some time to adapt for new users.
- The instance size makes an impact on the performance of the firewall.
Conclusion
The Palo Alto Networks VM-Series Next-Generation Firewall is not just a virtual firewall—it’s a cloud-ready security platform. It empowers organizations to maintain strong security controls while embracing agility, automation, and scale.
Stay tuned for Part 2, where we’ll walk through a step-by-step hands-on setup for HA VM-Series Next-Generation.



