AWS WAF – Web Application Firewall
Introduction
AWS WAF is a web application firewall that helps protect your web applications or APIs against common web exploits by monitoring and filtering the HTTP and HTTPS requests that reach your application. It allows you to create rules to block, allow, or monitor (count) web requests based on conditions that you define. AWS WAF is designed to integrate seamlessly with other AWS services, such as Amazon CloudFront and Application Load Balancer (ALB), to provide a comprehensive security solution for your applications.
Working with AWS WAF
AWS WAF works by inspecting web requests that reach your application and applying rules to determine whether to allow, block, or monitor the requests. You can create rules based on various criteria, such as IP addresses, HTTP headers, or request parameters. When a request matches a rule, AWS WAF takes the specified action, such as blocking the request or allowing it to proceed.
AWS WAF also provides a feature called Managed Rules, which are pre-configured rules that are designed to protect against common web exploits, such as SQL injection and cross-site scripting (XSS). You can use these Managed Rules to quickly enhance the security of your applications without having to create custom rules.
Features of WAF
Key Features of AWS WAF:
- Customizable Rules: You can create custom rules tailored to your application’s specific security requirements.
- Managed Rules: AWS WAF provides managed rule sets that help protect against common threats like SQL injection and cross-site scripting (XSS).
- Logging and Monitoring: AWS WAF provides detailed logs and metrics that help you monitor incoming traffic and identify potential security threats.
- Integration with AWS Services: AWS WAF integrates seamlessly with other AWS services like CloudFront and ALB, allowing you to protect your applications without impacting performance.
Use of WAF
How to Use AWS WAF?
1. Create a Web ACL: Start by creating a Web ACL, which is a set of rules that define how AWS WAF filters incoming requests.
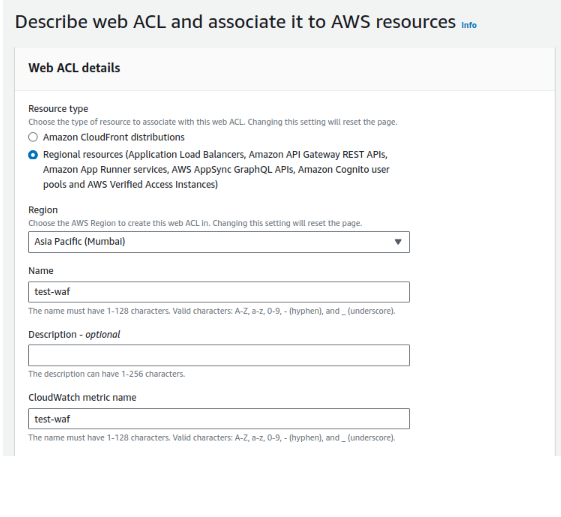
1.1 Choose a resource type for Cloudfront distributions the region is N.Virginia as it’s a global service, for Regional services such as Application Load Balancers, Amazon API Gateway REST APIs, Amazon App Runner services, AWS AppSync GraphQL APIs, Amazon Cognito user pools and AWS Verified Access Instances region needs to be selected where the resource that needs to be protected exists.
1.2 Provide a name for WebACL & Cloudwatch Metric name.
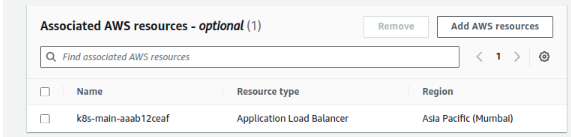
1.3 Choose the actual resources on which WAF needs to be implemented, here we are placing WAF over the Application load balancer named k8s-main-aaab12ceaf
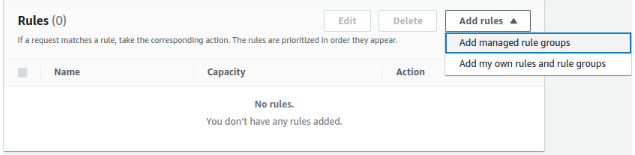
2. Define Rules: Define the rules within your Web ACL to specify which requests to Allow, Block, or Count.
2.1 We can either add managed rules or own rules, Managed rules are both free as well as paid and are managed by big vendors such as AWS,Cloudbric Corp., Cyber Security Cloud, F5, Fortinet, GeoGuard, Imperva, ThreatSTOP.
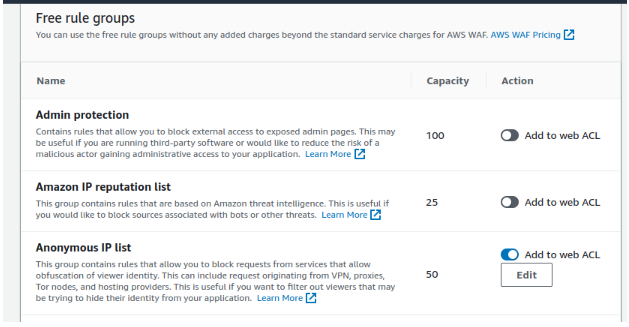
2.2 For Own managed Rules we can have rules such as IP list of our self-resources that we need to Allow and do not want our WAF to inspect and block.
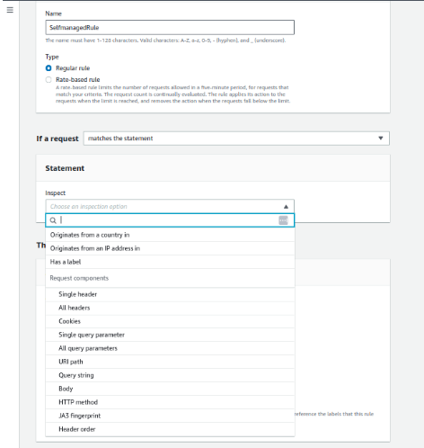
2.3 Rules that are implemented have 5 actions that can be if a rule matches our condition, actions are to Allow, Block, Count, CAPTCHA, Challenge.
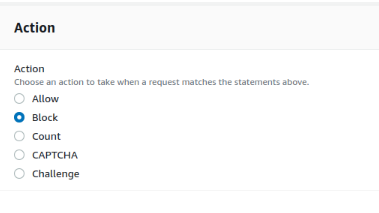
2.4 Default action for WAF should be decided to either Allow or Block connections and this is selected as per the use case.
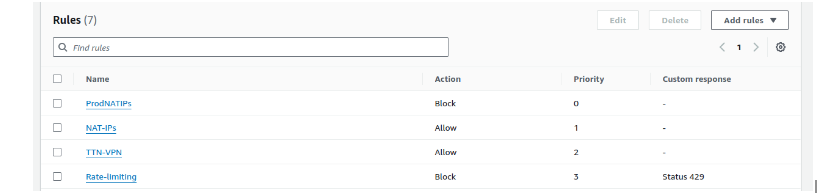
3. Setting the Rule Priority – Prioritize the rules as rules are evaluated from top to bottom, one such example is to keep the Allow list in top order.
4. Enable/Disable sampled requests that are used just for the quick look for the last 3 hours of data.
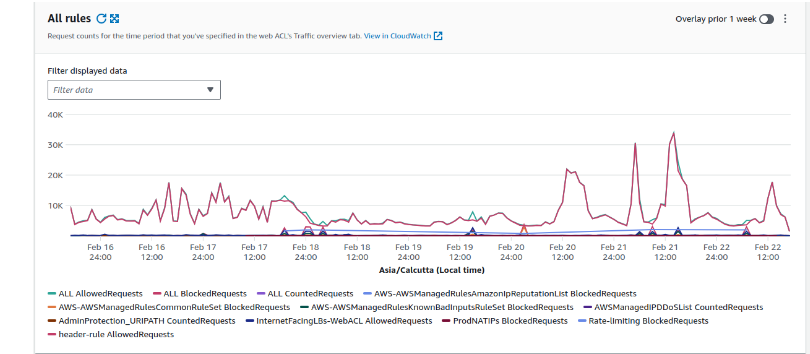
Snapshot of Sampled Requests
5. Successful WAF implementation: One More step towards Successful WAF implementation is to enable logging and to store logs so that which IPs are being blocked and under what Rules these IPs are blocked can be tracked.
5.1 Having track of these logs are required to monitor whether the genuine IP are being blocked or not.
6. Monitor and Fine-tune: Monitor the traffic to your web applications using AWS WAF logs and metrics. Fine-tune your rules based on the traffic patterns and security requirements of your applications.
Points to Remember
- WAF should always be implemented in Count mode for first time.
- WAF Logs should be evaluated in order to track IPs that are being blocked if WAF would be in block mode.
Conclusion
AWS WAF is a powerful tool that can help enhance the security of your web applications hosted on AWS. By creating rules to block, allow, or monitor web requests, you can protect your applications against common web exploits and ensure their availability and security. With its seamless integration with other AWS services, such as CloudFront and ALB, AWS WAF provides a comprehensive security solution for your applications in the cloud.



