Modernizing Enterprise Security: How Microsoft Sentinel Powers Proactive Threat Defense
Introduction
As cyber threats grow in sophistication, businesses require a powerful solution to detect, analyze, and address security incidents efficiently. Microsoft Sentinel, a cloud-native Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platform, empowers organizations to strengthen their security framework while simplifying operations.
In this blog, we will explore Azure Sentinel, its key features, benefits, and how it can be integrated into your security operations.
What is Azure Sentinel?
Azure Sentinel is a cloud-native SIEM and SOAR platform that provides intelligent security analytics and threat intelligence across an organization’s infrastructure. It enables security teams to collect data, detect threats, investigate incidents, and automate responses efficiently.
Key Capabilities:
Microsoft Sentinel offers a complete set of tools for end-to-end security operations:
- Collect data from across your systems using built-in connectors
- Detect threats with analytics, threat intel, and watchlists
- Hunt for risks using queries and notebooks
- Investigate incidents with rich visual insights
- Respond automatically using playbooks and automation rules
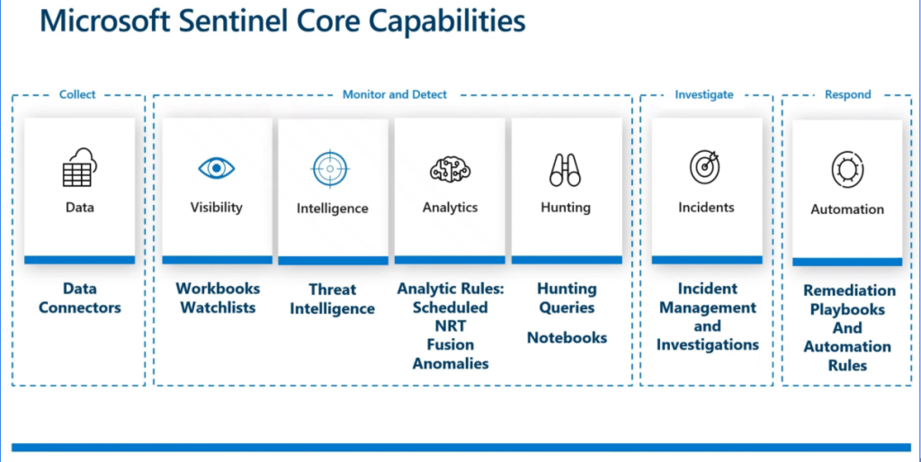
Sentinal Core capabilitues
Why Use Azure Sentinel?
Organizations choose Azure Sentinel for the following reasons:
1. Scalability & Flexibility
Unlike traditional SIEM solutions that require significant infrastructure and maintenance, Azure Sentinel is cloud-native, making it highly scalable and cost-efficient.
2. AI-Powered Security Analytics
With built-in machine learning and AI capabilities, Azure Sentinel detects advanced security threats in real-time, reducing false positives and improving accuracy.
3. Integration with Microsoft Security Tools
Seamlessly integrates with Microsoft Defender, Azure Security Center, Office 365, and Azure Active Directory, ensuring comprehensive security coverage.
4. Third-Party Integrations
Supports connectors for various third-party tools such as AWS, Cisco, Palo Alto Networks, Check Point, and Splunk, making it a versatile security solution.
5. Cost Efficiency
Azure Sentinel operates on a pay-as-you-go model, eliminating the need for expensive hardware and reducing overall operational costs.
Key Features of Azure Sentinel
1. Data Connectors:
- Seamlessly gather data from a variety of sources, such as cloud platforms, firewalls, endpoints, and identity solutions.
- Microsoft provides integrated connectors to simplify linking with different security tools.
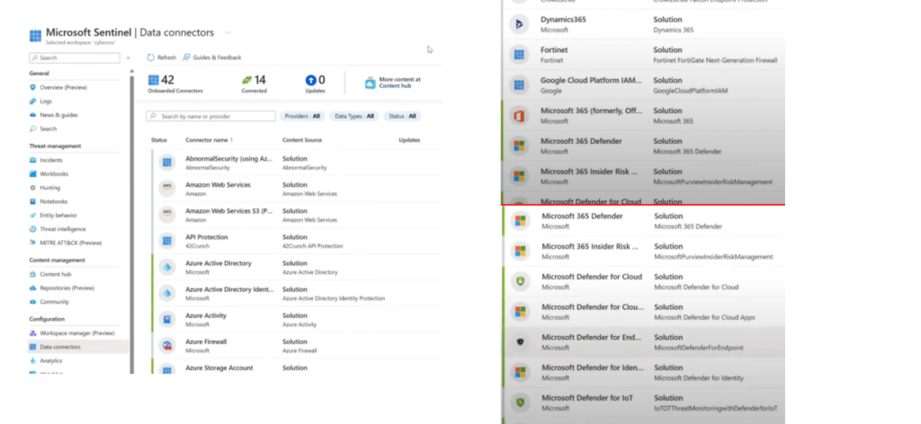
Data connectors
2. Advanced Threat Identification :
- Employs AI-based behavioral analysis to detect unusual security patterns.
- Integrates information from multiple sources to detect possible threats.

SentinalIncidents
3. Threat Investigation and Hunting
- Utilizes the powerful Kusto Query Language (KQL) for examining security logs.
- Supports proactive threat hunting with ready-to-use workbooks and dashboards.
KQL Query
4. Automated Response Processes
- Leverages Azure Logic Apps to develop automated workflows for incident response.
- Enables automatic alerts and actions based on set conditions.
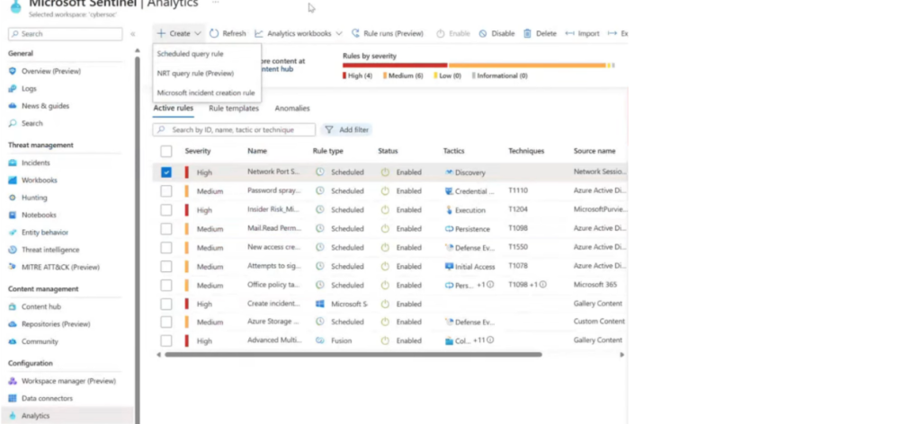
Sentinal Rules
5. Unified Dashboard and Reporting
- Features a centralized dashboard offering real-time security insights.
- Allows users to design custom reports using analytics rules and workbooks.
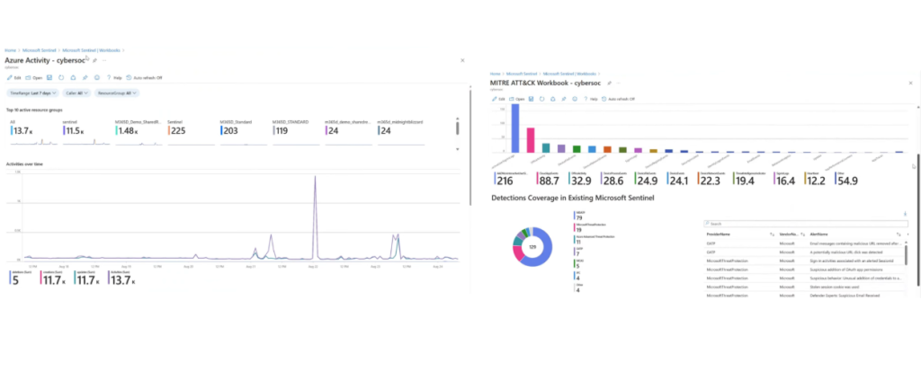
sentinalWorkbook
Key Roles in Microsoft Sentinel: Who Does What?
Microsoft Sentinel assigns specific roles to help manage security operations efficiently without giving everyone full access. Here’s a quick breakdown:
- Sentinel Reader: Can view data, dashboards, and logs, but can’t make any changes. Ideal for compliance or audit teams.
- Sentinel Responder: Has permission to manage and investigate incidents, making it perfect for security analysts responding to threats.
- Contributor: Has full access to create, update, and delete resources in Sentinel. This is the go-to role for security engineers or architects setting things up.
- Sentinel Playbook Operator: Can trigger and manage playbooks (automated workflows), useful for teams handling automated responses.
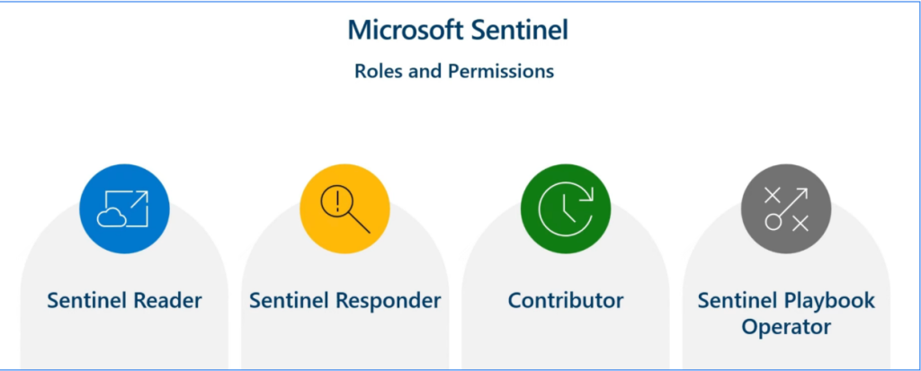
Sentinal Roles
Automating Threat Detection: Blocking Invalid SSH Attempts Using Sentinel
Securing cloud-based virtual machines is critical, especially when SSH access is exposed to the internet. This Below steps walks through how Microsoft Sentinel can be used to automatically detect failed SSH login attempts and trigger a real-time response — reducing manual intervention and improving security posture.
Step 1: Connect the VM to Microsoft Sentinel
To begin, ensure the virtual machine (VM) is connected to Microsoft Sentinel:
- Install the Log Analytics Agent (also called the MMA agent) on the VM.
- Link it to a Log Analytics Workspace using the workspace ID and primary key, both available from the Azure portal.
This connection enables system logs, including SSH login events, to flow into Sentinel for monitoring and analysis.
Step 2: Enable the Syslog Data Connector
After the agent is installed, Microsoft Sentinel needs to know how to handle the incoming data. This is done through a Data Connector.
-
- In the Sentinel portal, navigate to Data connectors.
- Search for and open the Syslog connector (usually titled “Syslog (Linux Servers)”)
- Adhere to the configuration guidelines to link your Log Analytics Workspace
This connector acts as a bridge, telling Sentinel to ingest and process Syslog events like SSH login attempts coming from Linux VMs.
Step 3: Configure a Data Collection Rule (DCR)
A Data Collection Rule (DCR) specifies which logs should be collected from the VM:
-
- Create a DCR in Azure Monitor.
- Select Syslog as the data source.
- Configure it to collect logs with:
- Facility: auth
- Severity: Information or Notice
This ensures that authentication-related events, such as failed SSH login attempts, are captured and sent to Sentinel.
Step 4: Build a Custom Analytics Rule to Detect Failed SSH Logins
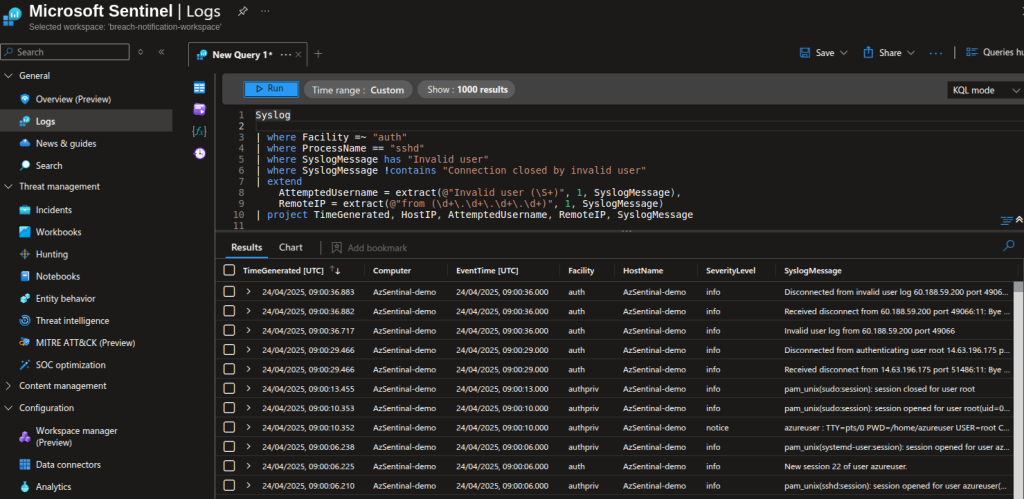
Syslog
| where Facility =~ “auth”
| where ProcessName == “sshd”
| where SyslogMessage has “Invalid user”
| where SyslogMessage !contains “Connection closed by invalid user”
| extend
AttemptedUsername = extract(@”Invalid user (\S+)”, 1, SyslogMessage),
RemoteIP = extract(@”from (\d+\.\d+\.\d+\.\d+)”, 1, SyslogMessage)
| project TimeGenerated, HostIP, AttemptedUsername, RemoteIP, SyslogMessage
This query finds SSH login attempts with invalid usernames by filtering auth-related syslog messages from the sshd process and extracts the attempted username and source IP. It helps detect suspicious or brute-force SSH access attempts.
When activated, this rule generates an alert in Sentinel.
Step 5: Automate the Response Using a Logic App
Once an incident is created, Logic Apps can be used to respond automatically. This reduces the requirement for manual involvement.
Possible automated actions:
-
- Send an alert via Teams, Slack, or email
- Trigger a Runbook to shut down or isolate the VM
- Tag the VM as “UnderAttack” for visibility
The Logic App is linked directly to the analytics rule under the Automated Response section.
Outcome: Real-Time Detection and Response
With this setup, Microsoft Sentinel continuously monitors for suspicious SSH activity, automatically raises incidents for brute-force behavior, and initiates a rapid response. This provides improved visibility and faster threat mitigation for cloud-based environments.
Understanding Sentinel Costs
What Are You Paying For?
Microsoft Sentinel is billed based on:
- The volume of data analyzed by Sentinel, and
- The amount of data stored in an Azure Monitor Log Analytics workspace.
Data entering Sentinel falls under two categories, each with its own purpose and impact on cost.
Types of Logs: Analytics vs. Basic
1. Analytics Logs
These logs support rich analytics and alerting with no query limitations. They are designed to handle high-value security data that reflects system usage, posture, and performance. Ideal for:
- Real-time threat detection
- Alert generation
- Deep investigations and hunting
Most appropriate for critical security data needing comprehensive analytics and ongoing monitoring.
2. Basic Logs
These are lower-cost logs used for storing large volumes of less sensitive data. They don’t support full Sentinel features like alerts or continuous monitoring. Use cases include:
- Verbose or noisy logs
- Rarely queried data
- Ad-hoc investigations
Great for cost savings when full analytics aren’t needed.
Sentinel Pricing Tiers (Analytics Logs)
Pricing depends on how much data you ingest daily. The greater your commitment, the more you save.
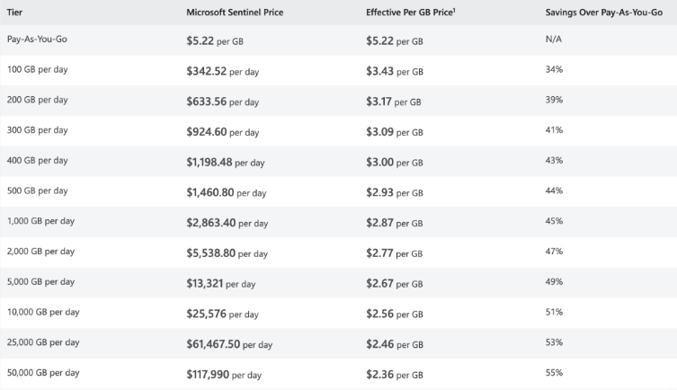
Sentinal Pricing
This tiered pricing encourages organizations to commit to larger volumes of data ingestion upfront for significant cost savings.
Quick Tip for Cost Management
- Store essential security events as Analytics Logs
- Use Basic Logs for noisy, infrequent, or low-priority events
- Regularly review data ingestion patterns to avoid unnecessary costs
- Apply retention policies and data caps to control expenses
Conclusion
Azure Sentinel is a powerful and scalable cloud-native SIEM and SOAR solution that helps organizations detect, analyze, and respond to security threats efficiently. With AI-driven analytics, automation capabilities, and seamless integrations, it is an excellent choice for businesses looking to strengthen their security posture.
If you’re looking to enhance your security operations, Azure Sentinel is a must-have tool. Start your journey today by exploring Azure Sentinel in the Azure Portal!



