Benefits of Using a Host-Based Intrusion Detection System

This blog discusses the utility and benefits of using a Host-based Intrusion Detection System (HIDS) tool: OSSEC in your environment. A host-based intrusion detection system provides real-time visibility into what activities are taking place on the servers, which adds to the additional security. There are various tools available in the market for this purpose:
- IBM Internet Security Systems Commercial HIDS-NIDS
- Intrusion Detection System (IDS)
- Trusted Computing Group
- OSSEC – a multi-platform open source HIDS
- Tripwire (software) – commercial HIDS
- Network Intrusion Detection System (NIDS)
- Trusted Platform Module
- Verisys – commercial HIDS
The focus of this article will be on understanding the concepts of OSSEC, HIDS tool.
Introduction
HIDS is an intrusion detection system that monitors, analyzes the computing systems and the network packets on its network interfaces. It is a method of security management for computers and networks.
OSSEC is a powerful Open Source Host-based Intrusion Detection System, written in C. It provides a platform to monitor your systems by performing log analysis, integrity checking, rootkit detection, windows registry monitoring, active response and real-time alerting. OSSEC supports most operating systems including Linux, Windows, Mac OS, Solaris etc. OSSEC is mainly a log-analyzer but with additional features such as:
- Centralized Logging: Works just like rsyslog, but it doesn’t store logs. It analyses the logs.
- Alert System & Analyzer: Just like logstash it analyzes the log and generates alerts.
- Active-Response Mechanism: Just like fail2ban, spots authentication failures.
- File Monitoring System: Just like tripwire
- Rootkit Engine: Just like rkhunter
- Policy Compliance: Customizable rules to ensure implementation of security policies.
Use cases and Features
- HIPPA and PCI Complaint: OSSEC is used to meet specific compliance requirements like HIPPA and PCI. It detects and send an alert for any unauthorized file system modifications or any malicious behavior.
- Real Time Alerting: Can be enabled on OSSEC to notify a customer about any unauthorized events. Also, different priority levels can be set on these events depending on the severity. Further, Integration of alerting mechanism with Splunk, SMTP, SMS and Syslog allows clients to be on top of alerts by sending them to e-mail enabled devices.
- Active Response: Allows OSSEC to take immediate action when specified level of alerts are triggered. For instance, Active Response option is used to block an attack, such as Brute force attack, immediately. To summarize, it prevents an incident from spreading before an administrator can take action.
- Centralized Management Server: OSSEC provides a centralized management server to manage policies across multiple operating systems. Moreover, it lets users to create new policies or modify the existing policies. Agent based and agentless monitoring of the environment is provided by OSSEC.
- File Integrity Checking: An attack on your environment, consisting of various systems and networks, definitely changes the systems in some way. The goal of file integrity checking or monitoring is to detect these changes and alert you when they happen. It can be an attack, or a mistake or may be misuse by an employee or even a typo by an admin, any file, directory or registry change will be alerted to you.
- Log Monitoring: Logs or events are being generated by every operating system, device and application on your network to let you know what is happening in your environment. OSSEC basically collects, analyzes and correlates these events or logs to let you know if something suspicious is happening (hacking, attack, misuse, errors, etc). For instance, OSSEC will notify you when a new application is installed on your machine, or when someone amends any rule in your firewall. By monitoring your logs, OSSEC will notify you.
- Firewalls, Switches, and Routers: OSSEC can receive and analyze Syslog events from a variety of firewalls, switches and routers. It supports all Cisco routers, Netscreen firewall, Cisco PIX, Cisco ASA, Cisco FWSM, Juniper Routers, Checkpoint and many more.
OSSEC Architecture
OSSEC has two working models:
- Master-Agent architecture: Where central server’s function is to monitor and receive information from agents.
- Standalone or Local Model: When you have a single system to monitor.
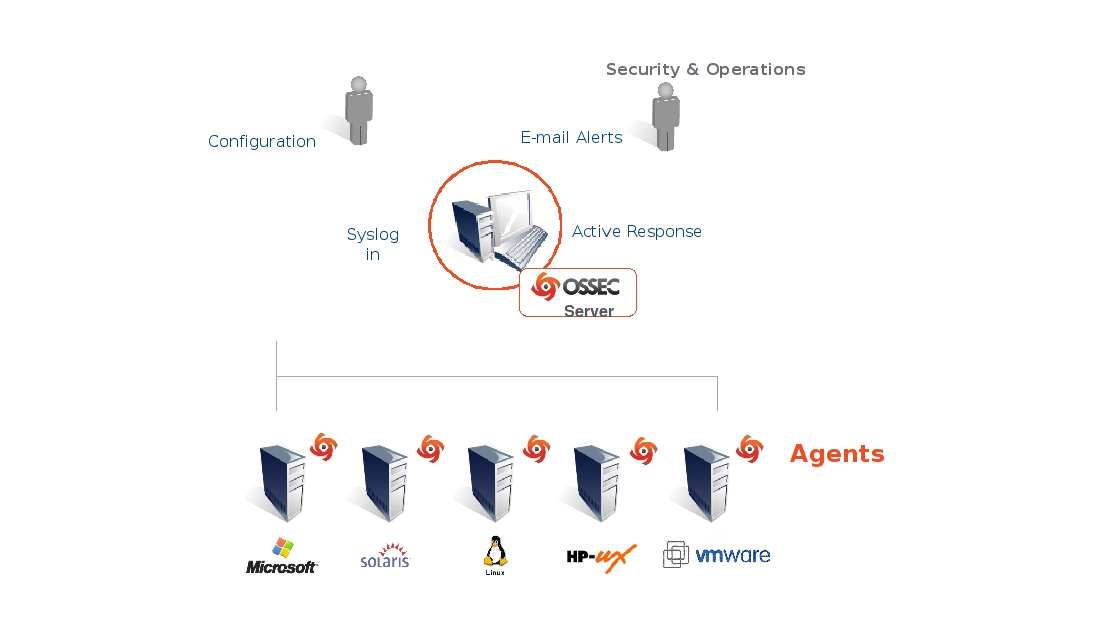
FIG: OSSEC ARCHITECTURE DIAGRAM
Manager or OSSEC server: The manager is the central piece of the OSSEC deployment. OSSEC Management server stores the events, file integrity checking databases, the logs, and system audit entries. All the rules, decoders, and configuration options are stored centrally in the manager server; thus making it easy to administer a large number of agents.
Agents: The agent is a small program, or collection of programs, installed on the systems to be monitored. The agent’s function is to collect information (raw data) and forward it to the OSSEC Manager for analysis and correlation. Some information is collected in real time, others periodically or timely as per the configuration. OSSEC agent has a very small memory and CPU footprint by default, not affecting the system’s usage at all. Moreover, OSSEC provides its agent’s security. It runs with a low privilege user that is created during installation and inside a chroot jail. Most of the agent configuration can be pushed from the manager.
Working of OSSEC:
OSSEC Management Server receives the events or logs from agents, then perform analysis and then execute active responses to admin in case of anything suspicious is detected.
Internal Processes of OSSEC Server:
➔ Analysisd – (main process) Does all the analysis of events.
➔ Remoted – This process receives remote logs from agents.
➔ Logcollector – It reads log files (syslog , Flat files, Windows event log, IIS, etc).
➔ Agentd – Simply, forwards logs to the Ossec server.
➔ Maild – It sends email alerts.
➔ Execd – This process executes the active responses.
➔ Monitord – It’s function is to monitor agent status, compressing and signing of log files, etc.
➔ Ossec-control – it manages the start and stop of all of the processes.
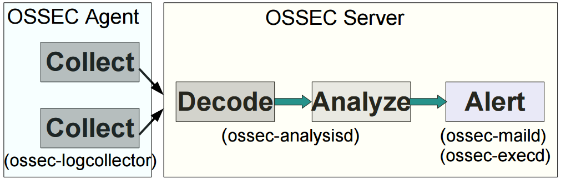
FIG: Log Analysis Flow Diagram – OSSEC
Generic log analysis flow for OSSEC client/server architecture is as follows:
➔ On the agent side, ossec-logcollector collects the log.
➔ On the master end, analysis and decoding of logs is done by ossec-analysisd.
➔ Ossec-maild is responsible for alerting.
➔ Active responses are executed by ossec-execd.
By default it uses UDP port 1514 for communication between client and server.
Conclusion
The objective of this blog is to make you familiar with the OSSEC architecture and it’s use cases. The next blog will feature the configuration and installation of OSSEC and some advanced use cases.



