Connecting AWS API Gateway from Non AWS Environment using a private communication channel
What is API Gateway
An API gateway is an API management tool between a client and a collection of backend services. An API gateway acts as a reverse proxy to accept all application programming interface (API) calls, aggregate the services required to fulfill them, and return the appropriate result.
Problem Statement
How to access a Private API endpoint URL hosted on AWS from a client hosted in a Non-AWS environment?
Solution
Create a Site-to-Site VPN connection between the On Premise/Other Cloud (Eg, Azure) and AWS environment and configure the tunnels between them.
Steps to Create a Site-to-Site VPN Connection
(Taking Reference of Azure as Non-AWS env)
- Create Azure Virtual Network Gateway
This needs to be done by the Azure team (Client/Requester end), and note the Public IP address which is used while performing this step.
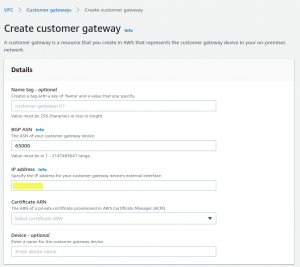
- Create AWS Customer Gateways
While creating the AWS Customer Gateway, put the IP address which was copied in Step 1 in the below highlighted field.
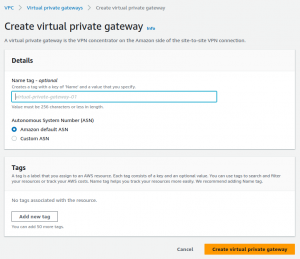
- Create AWS Virtual Private Gateway
Create AWS Virtual Private Gateway and attach it to the VPC

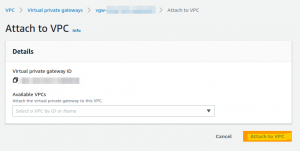
- Create AWS Site-to-Site VPN Connections
Enter the details in the requested fields:
- The target gateway type should be a Virtual private gateway, as selected in the above picture.
- Choose the Virtual private gateway created in the above step.
- Choose the Customer gateway created in the above step.
- Choose Routing options as static and enter the IPs.
- Put the values in Local and Remote IPv4 network CIDR.
- Later update the tunnel configurations for both tunnels, like entering the Pre-shared key used on the Client side, selecting the algorithms that both the client and server support, can keep others values as default, and enabling logging if required.
- Once the tunnels are created, share the Outside IP Addresses of tunnels with the Azure team so that they can configure them in Azure Local Network Gateways.
- The next step is to Create Azure connections. While creating connections, kindly put similar configurations which were used while creating tunnels at the AWS end in the above step.
Once the setup is done correctly, Status will be connected at both AWS and Azure end.
- Add VPN Route table to AWS VM subnet. This step will redirect all traffic from the AWS VM subnet to Azure Network through VPN by configuring the AWS Route table.
- Add Routes in the route table.
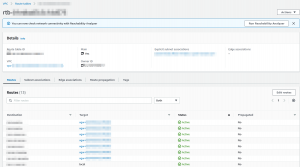
- Now add Static Routes.
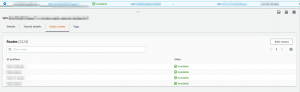
After the above steps, Tunnels should be established between Azure and AWS.
Note: Both the tunnels should be UP in order to provide high availability.
Implementation Plan for Connectivity from a Non-AWS Environment
Steps to connect AWS Private API Endpoint URL from Azure
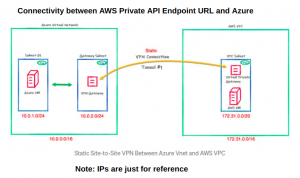
- Create Azure Virtual Network Gateway (Takes about 30 – 45 mins)
- Create AWS Customer Gateways
- Create AWS Virtual Private Gateways
- Create AWS Site-to-Site VPN Connections
- Create Azure Local Network Gateways
- Create Azure Connections
- Add VPN route table to AWS VM Subnet
Prerequisites:
- Site-to-Site VPN connection should be established between Azure and AWS environment, and tunnels should be up.
- Source IPs should be allowed at Static routes in VPN, Route tables associated with VPC, and WAF if WAF is used.
- VPC Endpoint is created to access and invoke API service.
Steps to connect AWS Private API Endpoint URL from On Premise / DC
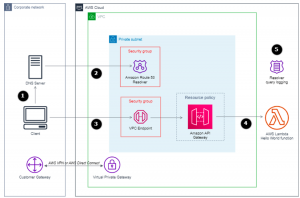
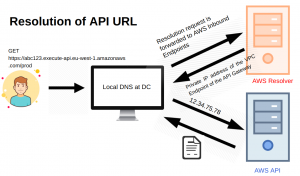
- The client calls the private API endpoint URL (eg – GET https://abc123.execute-api.eu-west-1.amazonaws.com/prod)
- The client asks the on-premises DNS server to resolve this (abc123.execute-api.eu-west-1.amazonaws.com).
- You must configure the on-premises DNS server to forward DNS queries for the AWS-hosted domains to the IP addresses of the inbound resolver endpoint.
- After the client successfully resolves the API Gateway private DNS name, it receives the private IP address of the VPC Endpoint of the API Gateway.
Prerequisites:
- Site-to-Site VPN connection should be established between the DC and AWS environment, and tunnels should be up.
- Source IPs should be allowed at Static routes in VPN, Route tables associated with VPC, and at WAF if WAF is used.
- VPC Endpoint is created to access and invoke API service
Conclusion
This blog demonstrates how to connect AWS API Gateway from a Non-AWS env like On-Premise/DC or from Azure using VPC endpoints on a private network with all the security measures at different security layers. The benefits of using the API Gateway on a private network are that it reduces the attack surface and decreases the network latency.

