An essence of Application Security in Healthcare Sector
Hackers and cyber criminals identify healthcare organizations as a source of assets, similar in a way that a bank has monetary assets. In case you have any doubt about the previous statement, I would like to reassure you that healthcare information has a monetary value and worth. And yes, it is at risk.
What is wrong with the Healthcare sector?
There are two critical facts about the healthcare industry:-
- They manage a treasure of information that is financially lucrative and has Personally identifiable information (PII)
- Their inefficiency in handling the information they possess i.e. They lack the resources, processes, and technologies required to prevent and adequately detect attacks.
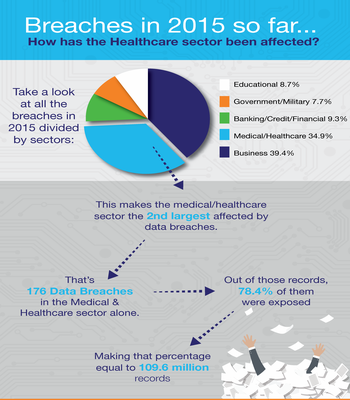
Source: www.idtheftcenter.org
Possible causes
Data breaches that occur due to malicious attacks mostly grab headlines, but a majority of data thefts are caused by employee negligence.
- Negligence : Almost two-thirds of data breaches in 2012 could be attributed to negligence or human error (35 percent) and system glitches (29 percent), was reported by the Ponemon Global Cost of a Data Breach study.
Source: www.pcworld.com
- User error as in use or handling of computer systems and devices.
Case Study
Excellus BCBS is a non-profit health insurance company. They discovered that their IT systems were attacked and compromised way back in December 2013. This revelation came two years after Excellus systems were open to the hackers in August this year. This was a result of a sophisticated attack to gain access to their systems and gather client’s personal data.
On August 5, 2015, Excellus BlueCross BlueShield learned that cyber attackers had executed a sophisticated attack to gain unauthorized access to our Information Technology (IT) systems. Our investigation further revealed that the initial attack occurred on December 23, 2013. As part of our own investigation, we notified the FBI and are coordinating with the Bureau’s investigation into this attack.
– President and CEO, Christopher C. Booth
The attackers gained unauthorized access to individuals’ information, which included:-
- Name
- Date of Birth
- Social Security number: A Social Security number abbreviated as SSN is a nine-digit number issued to the citizens of the United States under the Social Security Act. The number is issued by the Social Security Administration. The Social Security Administration operates as an independent agency of the US government). The purpose of this number is to track individuals for Social Security purposes. It has become a national identification number for taxation and other purposes.
- Mailing Address
- Telephone Number
- Financial Account Information
- Member Identification Number
- Claims Information
Community Vulnerability
Multiple points of attack & Increased surface area of attack
The healthcare organizations and business associates involved with them are a “community of organizations” and have shareable vulnerable patient data. This community that provides a large attack surface as they have many points of access to the attackers.
As in case of Excellus BCBS, members of other Blue Cross Blue Shield plans who had undergone treatment in the 31 county upstate New York service area of Excellus, including the individuals who do business with Excellus, and provided their financial account information or Social Security number to them were also affected.
Compensation they had to offer
Following the attack, the organization has offered two years of free identity theft protection services through Kroll (A global leader in risk mitigation and response solutions), credit monitoring through TransUnion, to all the affected individuals. They have established a dedicated call center for affected individuals and their questions. The organization also sent e-mails to its customers to let them know about the attack and how can they prevent themselves from future attacks.

Source: Excellus BCBS
Impacts of Data Breach
If an attacker is able to obtain information about a person’s medical condition, there will be additional risks. Any medical information about a patient’s mental health or HIV treatments could be disclosed, and there’s no way to make the information private again. There’s no way to remedy this, there’s no recourse to this action.
- Healthcare organizations should try to make data security central as a way of managing information systems
Healthcare organizations rely on legacy systems, these systems are engineered keeping in mind that this data is not sensitive. Many organizations refrain from investing in cyber security and fail to match the rate of threats they face. This has resulted in Healthcare industry lagging behind other industries when it comes to security
Reactive Approach Vs Pro-Active Approach
Healthcare sector organizations have to comply with government rules and regulations on protecting patient privacy, including HIPAA and are enforced by HHS. The approach should be vigilant in assessing the current infra and addressing the risks to data should be done on a regular basis.
A Reactive Approach is in which organizations should be able to identify and respond to the security incidents when they happen and also to mitigate harm to affected individuals. This approach also includes preventing future incidents from occurring.
A Pro-Active Approach is in which organization should be having an approach that will help them identify which threats pose the highest level of risk and prioritize them accordingly.
Organizations should analyze the current security status, keeping in view all the departments of the organization namely IT, security, legal, compliance, HR and Chief level executives. So, they can collaboratively create risk management & an incident response plan. The objective should be focused upon creating a company-wide culture of security in which employees at every level understand the potential threats and the importance of following security practices, abiding by the policies and following all procedures. We can also educate employees such that they should be familiar with common attack vectors and make them understand the criticality of data they possess. So, they will be able to identify anomalies and detect potentially suspicious activity.
Thus, it is important to assess the level of security of your healthcare application at regular intervals. This is as simple as answering a 5-minute questionnaire like the one below:
Read the next blog in the series about the essence of application security in e-commerce applications.



