Resolving Private DNS Queries using AWS VPC Resolver
AWS offers Route53, as a part of Amazon’s cloud computing platform, Amazon Web Services (AWS). It is a highly scalable web service that can be used as internal DNS hostings. With Route53 you can host multiple internal domain names within your VPC (or group of VPCs) which are visible and accessible to the internal hosts only and blocked for external traffic. This gives us a feasibility of calling our internal resources, ie. Application servers, Database servers, Load balancers with a friendly name according to our choice.

The resolver for a VPC always sits at +2 address. That means if the VPC is 172.16.0.0/16, the DNS resolver will be at 172.16.0.2. That also means that any machine on any subnet within this VPC will be able to talk to this resolver for internal (private zones) as well as external (internet) dns queries.
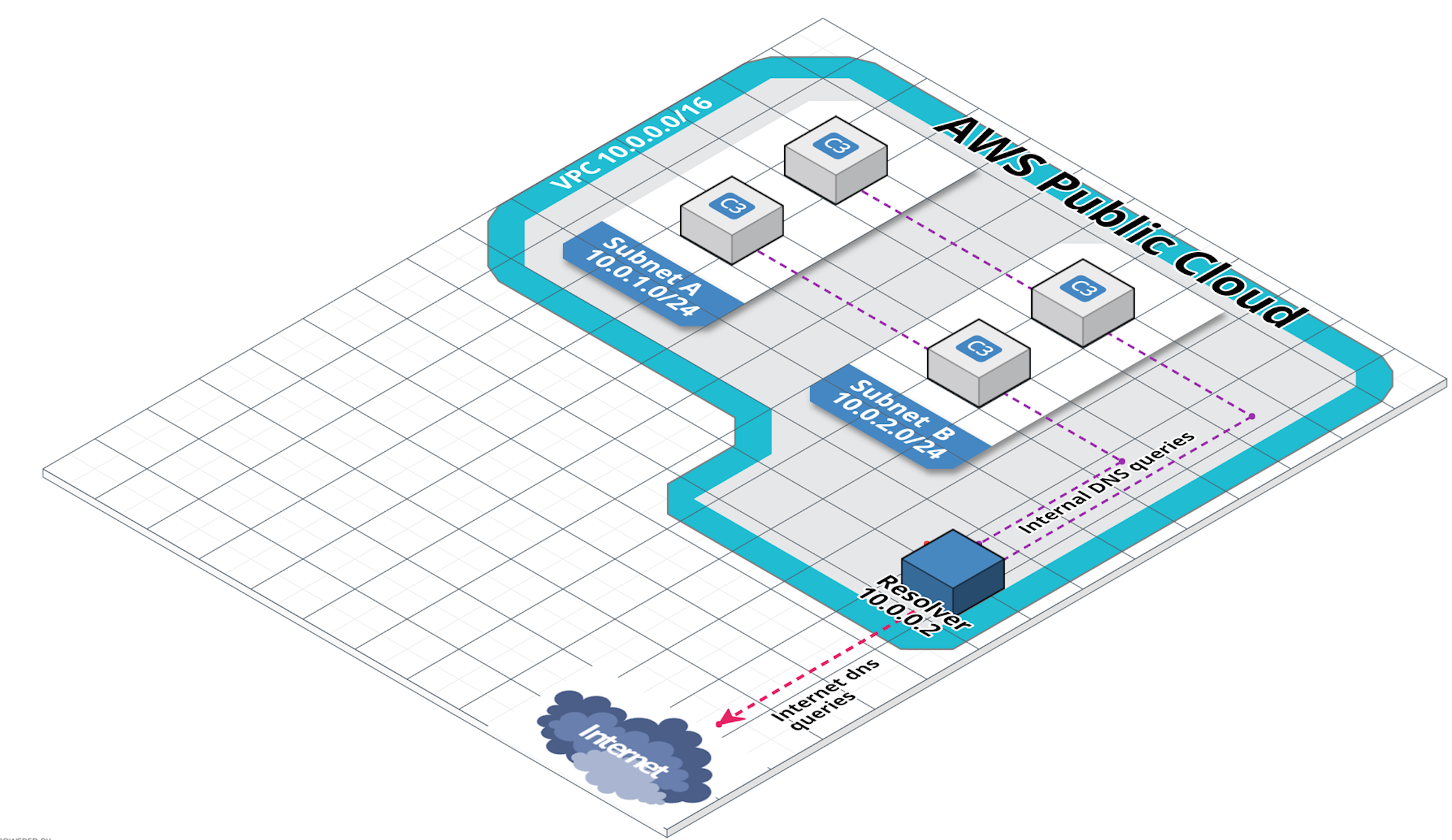
There are a few use cases for using the VPC DNS from outside of the VPC, particularly when connecting things into a VPC using a VPN. Here is when things get a little tricky, as the VPC Resolver is set up in a way that it won’t answer queries from outside its own network.
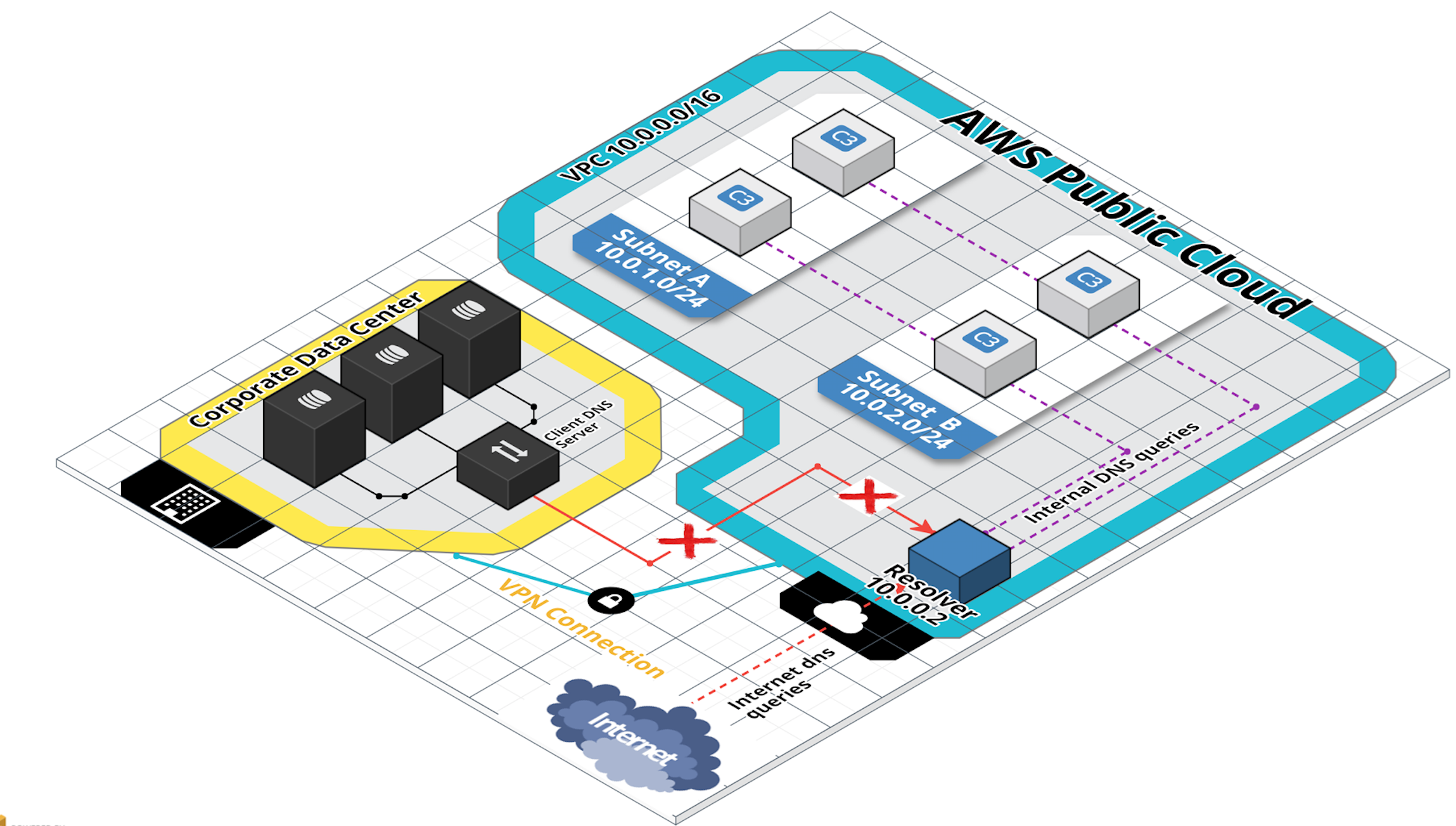
Here is when forwarder comes into picture. You could place a forwarder in the VPC in such a way that outside network (on VPN) uses this forwarder for DNS resolutions and connect to the VPC Resolver for all internal DNS queries.
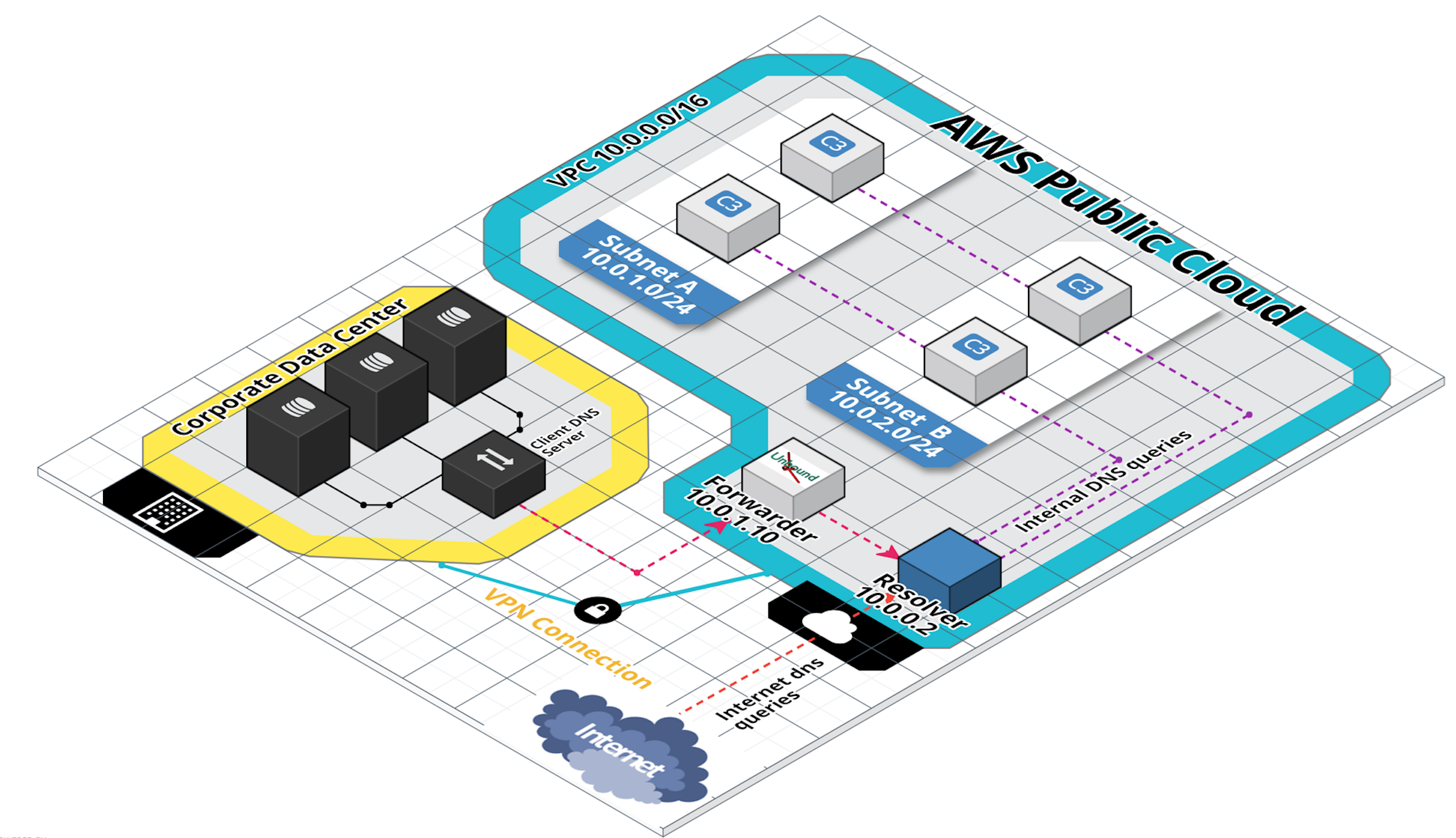
There are many ways to configure the forwarder. Here in this blog, we will see how Unbound can be used to serve our purpose. Unbound is a recursive caching DNS server which will be used as a forwarder to forward all the queries for a specified domain to the VPC resolver.
Once Unbound is installed, following configurations will be used in unbound.conf.
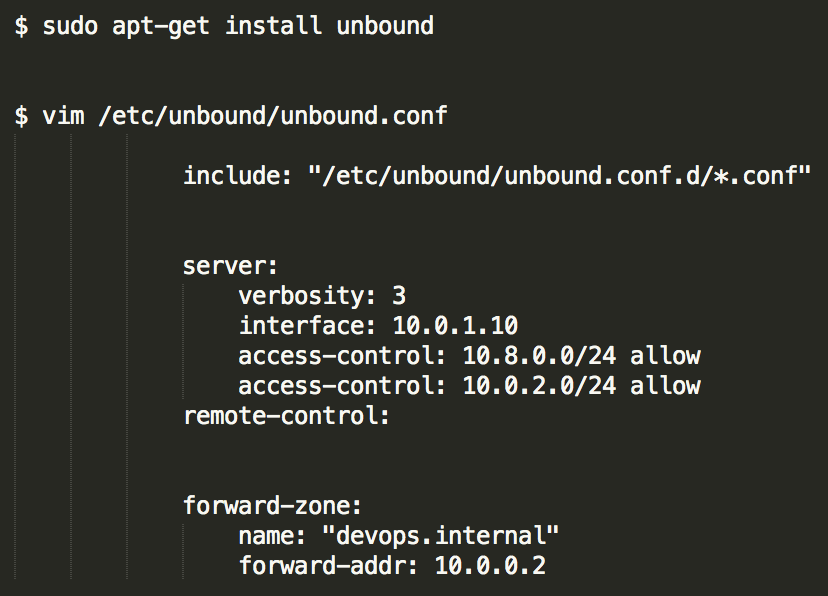
interface: The interface on which unbound will run and what clients will use as their primary nameserver.
access-control: IP or subnets which are allowed to make a request for query forwarding.
forward-zone name: The domain queries that needs to be forwarded. ‘ * ’ can be used to forward all domain queries.
forward-zone addr: VPC resolver address for the VPC.
You also need to ensure that the VPN clients are using the new forwarder as their primary nameserver. This way you can utilize VPC resolver to resolve internal DNS queries on any host within the VPC as well as on any host in extended data center. Similarly, you can utilize Unbound to forward all requests originating from AWS to the extended data center.




Hi,
Thanks for the nice tutorial
For some reason the forwarding isn’t working for me
I’m running both the VPN server and the DNS forwarder on the same host
This is the DNS forwarder config:
server:
interface: 0.0.0.0
access-control: 0.0.0.0/0 allow
remote-control:
forward-zone:
name: “.”
forward-addr: 172.31.0.2
And my VPN client is using in the resolv.conf the public IP of the server running both the VPN server and the DNS server (unbound)
telnet is working on port 53. What else should I be looking for ?
THANKS