Using Encryption with AWS Aurora

Encrypting RDS provides additional security by encrypting the underlying storage of your RDS data. Amazon uses AES-256 encryption algorithm to encrypt your RDS data on the devices on the servers hosting your database instances.The performance impact of the encryption is minimal on your DB instance. Your end application does not require to implement any changes to handle the encryption for storing or retrieving the data. The Encryption is enabled during the DB instance creation and is performed while storing the data on the devices on the servers hosting your DB instance. The input and retrieval of the data remain the same as it is before enabling the encryption.
Key Management Service (KMS)
AWS KMS is a service which enables you to create and use the encryption keys to protect your data. Encryption Keys can be managed by the AWS console or the CLI provided by the AWS.
AWS uses HSM (Hardware Security Module) to protect your keys. Keys are basically two types: CMK( Customer Managed Key) which are created by you and AWS provided key, A key is already created in your account by the AWS which can be used for the encryption of your data. These keys can be used on other services like EBS, S3 along with the RDS instances.
Customer Managed Key (CMK)
Using Console
- Access your AWS IAM console: https://console.aws.amazon.com/iam/
- On the navigation pane selecct Encryption Keys. Using filter you can select required region.
- Select Create Key.
- Enter the Alias for key to be created.
- Enter the Description of key and Select Next.
- Choose Users and Roles who will administer the Key. Select Next.
- Select which users can use the CMK for Encryption and Decryption data using KMS API.
- Select Next Step
- Select Finish
Creating a Customer Managed Key via CLI
First configure AWS CLI on your machine then create a file with the following content
[js]
{
"Version": "2012-10-17",
"Id": "defaultKey",
"Statement": [
{
"Sid": "Enabling IAM permissions",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::71193944530519:user/<username>"
},
"Action": "kms:*",
"Resource": "*"
}
]
}
[/js]
Create a key by using the following command
[js]$aws kms create-key –policy file://pathtocreatedabove[/js]
The command will return a JSON output similar to below:
[js]{
"KeyMetadata": {
"KeyId": "6fa334012-0383-4589-bcce-21015524258",
"Description": "",
"Enabled": true,
"KeyUsage": "ENCRYPT_DECRYPT",
"CreationDate": 1453286099.818,
"Arn": "arn:aws:kms:us-east-1:71251342259:key/6fa334012-0383-4589-bcce-21015524258",
"AWSAccountId": "71251342259"
}
}
[/js]
You have to use the value:
[js] KeyId": "6fa334012-0383-4589-bcce-21015524258"[/js]
for further steps.
Creating RDS instance with Encryption enabled.
You can use the AWS console for Creating the RDS instance with encryption. (Ref. Aurora Create Instance )
We will be performing the above operation using CLI.
Before creating the RDS instance you need to setup the AWS cli on your machine. (Ref. aws cli )
create-db-instance command is used for creating the RDS instance via AWS cli.
In the below command we would not be configuring options like multi A-Z, monitoring etc. We will be using the basic options required for launching an Aurora Db instance via cli.
[js]
create-db-instance –db-name mydb –db-instance-identifier aurorainstance –allocated-storage 5120 –db-instance-class db.r3.large –engine aurora –master-username admin –master-user-password Admin123 –db-security-groups default –vpc-security-group-ids default –availability-zone us-east-1b –db-subnet-group-name vpc-d0f904b4 –db-parameter-group-name default.aurora.5.6 –port 3306 –no-multi-az –engine-version 5.6.19a –license-model general-public-license –iops 2000 –character-set-name utf8 –publicly-accessible –storage-type io1 –storage-encrypted –kms-key-id rdskey –generate-cli-skeleton
[/js]
Benchmarking Aurora performance with encryption against Aurora performance without encryption
The test scenario used includes, a t2.micro instance with sysbench installed, r3.large Aurora RDS instance. The test was performed within single VPC. 500 sysbench threads were used for the tests.
Test results for Aurora DB performance without encryption
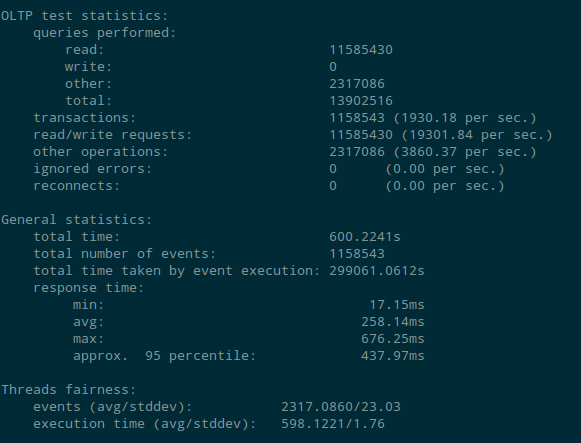
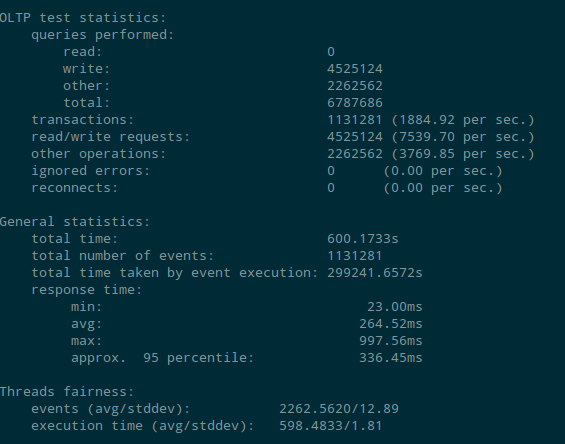
Test results for Aurora DB performance with encryption
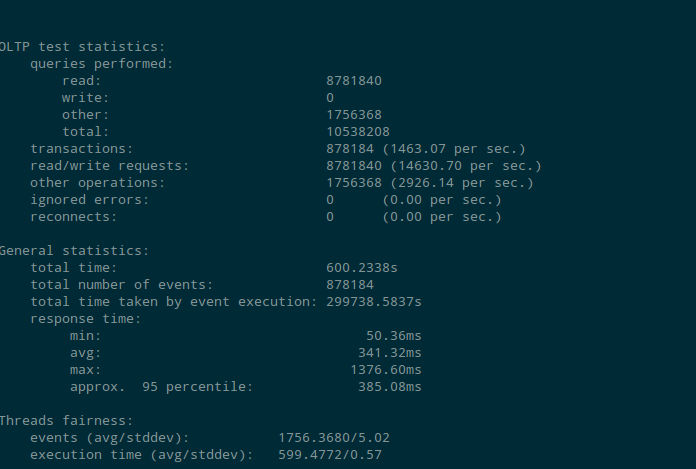
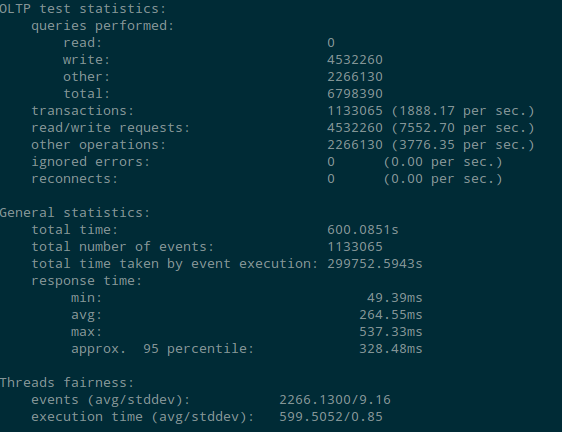
The number of read transaction per second with encryption enabled were 1463 (approx.) per sec as compared to 1930 (approx.) when encryption was disabled. Though the read operation seems low on encryption enabled instance but the 1463 transactions per sec is quite good keeping in mind r3.large instance (2 CPU , 15G RAM).
While performing write operation the performance was not affected as much. The performance test showed 1888 transaction per sec with encryption enabled where as it was 1884 transactions per sec when encryption was not enabled.
The test shows that the Aurora DB performance is not much affected with encryption enabled. We should consider enabling encryption on Aurora DB considering the added data security benefits provided.



