Connect AWS API Gateway from another AWS account on a private communication channel
What is API and API Gateway
Amazon API Gateway is a service that you can use to create application programming interfaces. Those are essentially the front door to your business logic or your applications on AWS. With the rapid increase in the use of mobile devices and the rise of the Internet of Things (IoT), due to this mostly backend systems and data are accessible to applications via APIs. To make it easy for you to use these APIs, API Gateway can generate client SDKs for a number of languages, including JavaScript, iOS, and Android. Using API Gateway, you can quickly and easily create a custom API for your application code and then call the Lambda function from your API. Using the API Gateway console, you can create your REST API and its associated resources and methods, manage your API lifecycle, generate your client SDKs, and view API metrics.
Benefits of API Gateway on private network
Amazon API Gateway is used to build RESTful and HTTP APIs. If the use of those APIs is limited to internal clients, customers prefer to use private APIs, because private APIs provide a secure means to invoke APIs via an interface VPC endpoint. API Gateway private integration makes it simple to expose your HTTP/HTTPS resources behind an Amazon VPC, for access by clients outside of the VPC. AWS provides all the security measures at different security layers to secure API gateway private integration. VPC resources such as Elastic Network Interface (ENI) and other associated resources can be secured by using a security group. Additionally resource policies are also applied to VPC endpoints to make it more secure.
Solution
VPC endpoint can be used to access the API gateway from another AWS account on a private network. Solution implementation steps are shown below.
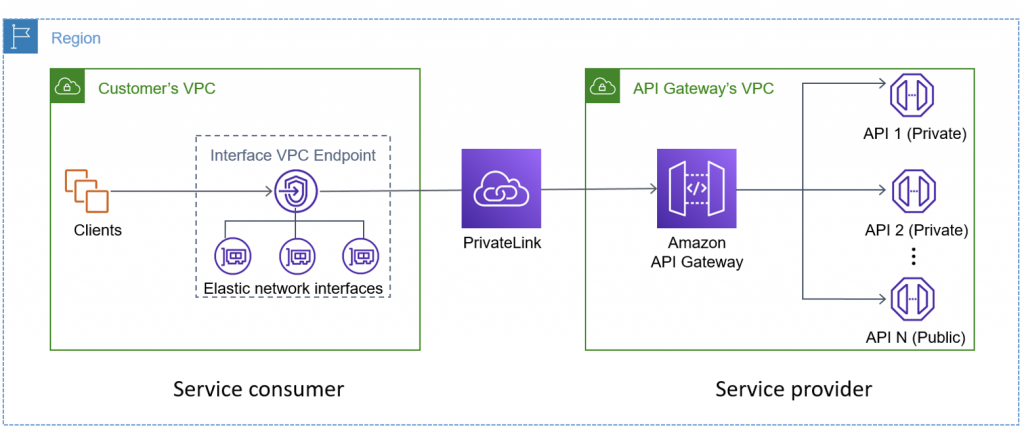
Implementation Steps
- Create an VPC endpoint in an Amazon Virtual Private Cloud (Amazon VPC) in account (account A).
- Goto VPC Management Console.
- In the navigation pane, choose Endpoints, Create Endpoint.
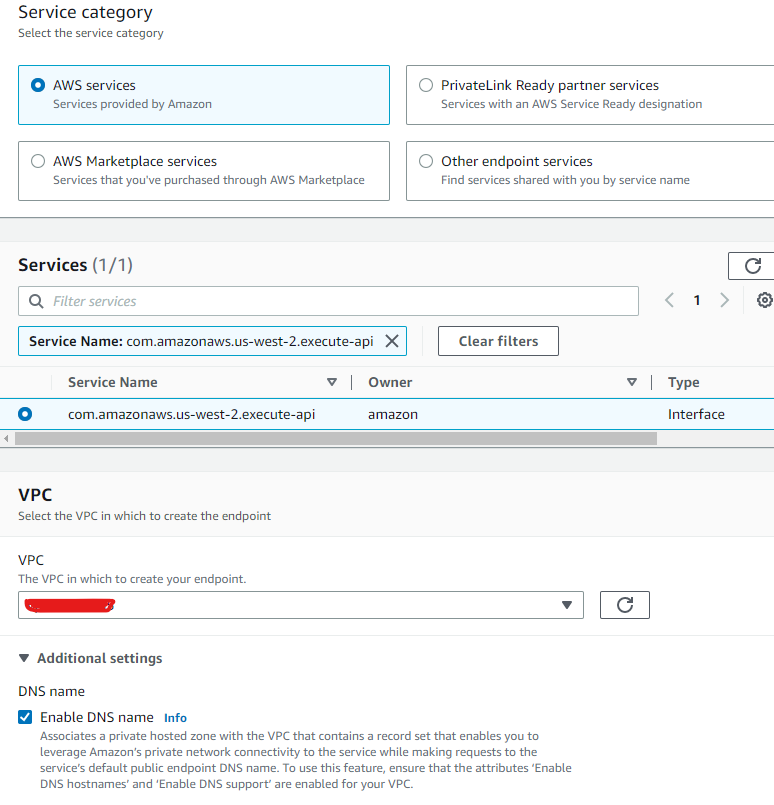
- Select AWS services for the service category.
- Select com.amazonaws.<region-name>.execute-api for the service name.
- Choose the VPC that you want to create the endpoint in for the VPC field.
- For Subnets, choose the subnets (Availability Zones) in which to create the endpoint network interfaces. To achieve high availability for your API, choose multiple subnets.
- Check Enable DNS name option.
- select the security group to associate with the VPC endpoint network interfaces.
Note :- Selected security group must allow HTTPS inbound traffic on TCP port 443 from the required IP ranges.
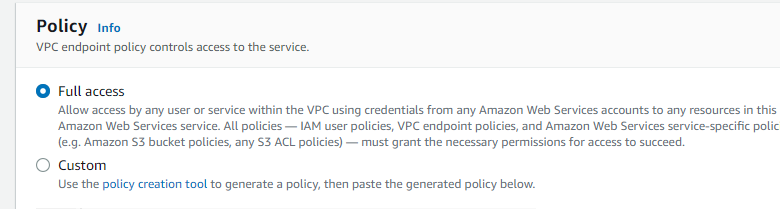
- Select Full Access for the policy and finally click on the Create endpoint button.
- Configure a rule in security group that allow TCP Port 443 inbound HTTPS traffic.
- After you choose Create endpoint and VPC endpoint will be created, Now copy the VPC Endpoint ID of your new interface endpoint (for example: vpce-1a2b3c456d7e89012). Then, choose Close.
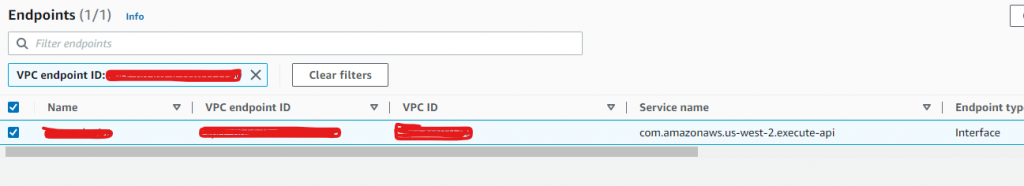
-
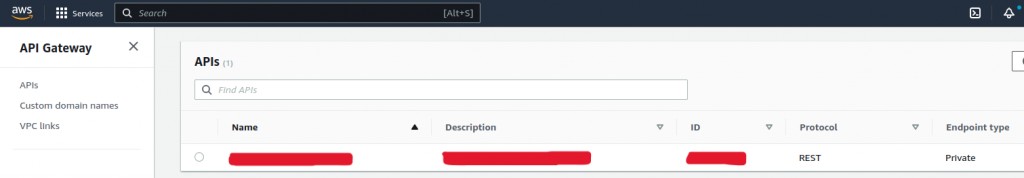
Create an API Gateway in a second account (account B).
- Goto API Gateway Console
- Choose Create API
- Under REST API, choose Build.
- Enter a name for API Name.
- For Endpoint Type, choose Private.
- Choose Create API.
-
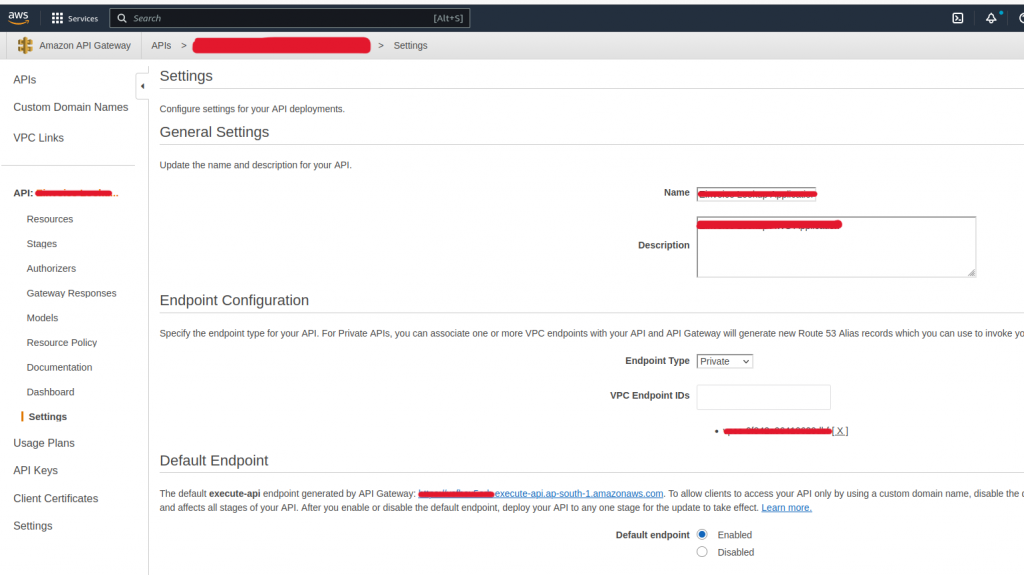
Configure a resource policy for the API Gateway to allow the VPC endpoint of Account A.
- In the left navigation pane of the API Gateway console, under your API, choose Resource Policy.
- On the Resource Policy page, use the below resource policy into the text box:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Deny", "Principal": "*", "Action": "execute-api:Invoke", "Resource": "execute-api:/*/*/*", "Condition": { "StringNotEquals": { "aws:sourceVpce": "<VPC-endpoint ID>" } } }, { "Effect": "Allow", "Principal": "*", "Action": "execute-api:Invoke", "Resource": "execute-api:/*/*/*" } ] }
-
Set up a method for the private REST API
Please refer to a link to Set up REST API methods in API Gateway.
-
Deploy the private REST API
Please refer to a link to Deploy a private API using the API Gateway.
-
Testing the private REST API from account A
- In account A, launch an Amazon Elastic Compute Cloud (Amazon EC2) instance in the same Amazon VPC as your interface endpoint.
- Connect to the Amazon EC2 instance.
- From the command line of your Amazon EC2 instance, use any of the following curl commands to call the private REST API in account B.
curl -i https://<api-gateway-id>.execute-api.<region-name>.amazonaws.com/stage-name
Conclusion
This blog demonstrates how to connect API Gateway from another AWS account using VPC endpoints on a private network with all the security measures at different security layers. Benefits of using the API Gateway on a private network that it reduces the attack surface and decreases the network latency.

