Unlocking Security: Sessions, Cookies, JWTs & User Access in Roku Development
Security is always a big concern for OTT apps. Understanding user identity and their access levels is very crucial while developing secure and user-friendly Roku channels with BrightScript. There are many mechanisms which are used to adopt security in OTT apps. Some of the most commonly used security mechanisms are – Sessions, Cookies, JWTs, Authentication, and Authorisation. Developers often hear these terms but very few of them do understand what they are and what is their importance in the Roku ecosystem. In this blog we’ll understand these concepts with practical Roku examples.
- Sessions: Let’s understand what a Session is and how it is managed in Roku. A Session generally notifies a time interval a user remains logged in or stays connected to a service. Usually sessions are managed server side. A unique identifier(known as SessionId) is used to identify a valid user. However, in Roku you can store session related data locally too.
Let’s see how we can store tokens and user data in BrightScript. You can manage sessions using the roRegistry or by storing tokens and user data in roFileSystem.

Sessions
This allows your Roku app to handle the user’s login state between app launches.
→ It is always recommended to encrypt sensitive data while storing locally.
2. Cookies: Cookies are usually used in web browsers. Cookies are a special secure place where small data(sent by a web server) is stored. This data is sent back to the server via api calls(usually in api headers), when required. But In Roku, there’s no existence of Cookies. Still, if your app uses Apis that use Cookies mechanism, there’s a work around. You can save data(sent by the server) in the registry and send this back to the server using request headers. Here’s a practical implementation.
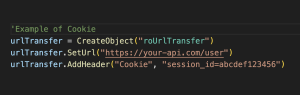
Cookie_In_Roku
3. JWT: JWT stands for JSON Web Token. JWTs are most commonly used for user authentication. A JWT is a combination of user info + a secret signature/token. It’s a compact token which is shared between client and server. JWTs are usually stored locally in your app. They are exchanged via api calls like we do with Sessions. JWTs can be securely stored and easily added to API requests. Example in Roku:
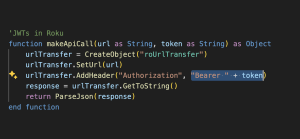
JWT_In_Roku
Here, the value(“Bearer ” + token) of Authorisation filed in the api header is a JWT. Please make sure that your token is stored in a secure place, such as roRegistry or encrypted files.
4. Authentication: Authentication means identifying Who You Are. Authentication is the process of validating a user’s identity. It’s pretty much similar to showing your ID at the school/office gate. The Login event is the best example of Authentication in Roku apps. When a user enters username and password in the Roku channel, these credentials are sent to the server. If the credentials are correct, the server returns a session ID or JWT. This session ID or JWT can be stored securely in a Roku device locally.
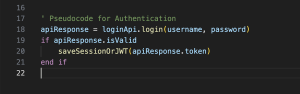
Authentication
5. Authorisation: Authorisation is a process of validating what rights a user has got. In simple words, it’s a procedure of checking what you are allowed to do. This can be understood with a very simple example – A guest user can browse an OTT application but the user should be having a subscription plan to watch a paid content.
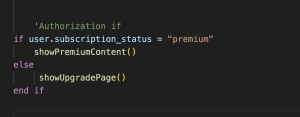
Authorisation_In_Roku
Conclusion: It’s really vital to understand these concepts in order to build Roku channels that are secure and user-friendly. Security is always a concern with OTT apps and sessions, cookies, or JWTs always pulls security in your apps. Final takeaways from this blog are:-
- Authentication = Who you are
- Authorisation = What you can do
- Session/Cookie/JWT = How server remembers and trusts you
Please drop comments below if you have questions or want to share your own ideas/suggestions!

